Hi everyone
Today we are going to look for a Box called Ignition which is rated as very easy in terms of difficulty. This machine has three phases: Recon, Enumeration and Exploitation.
- BOX Questions
- Task 1 Which service version is found to be running on port 80?
- Task 2 What is the 3-digit HTTP status code returned when you visit http://{machine IP}/?
- Task 3 What is the virtual host name the webpage expects to be accessed by?
- Task 4 What is the full path to the file on a Linux computer that holds a local list of domain name to IP address pairs?
- Task 5 Use a tool to brute force directories on the webserver. What is the full URL to the Magento login page?
- Task 6 Look up the password requirements for Magento and also try searching for the most common passwords of 2023. Which password provides access to the admin account?
- Recon & Enumeration
- Exploitation
- Key Takeaways
This room includes various tasks that needs to be completed to solve the entire CTF.
BOX Questions
Task 1 Which service version is found to be running on port 80?
nginx 1.14.2
Task 2 What is the 3-digit HTTP status code returned when you visit http://{machine IP}/?
302
Task 3 What is the virtual host name the webpage expects to be accessed by?
ignition.htb
Task 4 What is the full path to the file on a Linux computer that holds a local list of domain name to IP address pairs?
/etc/hosts
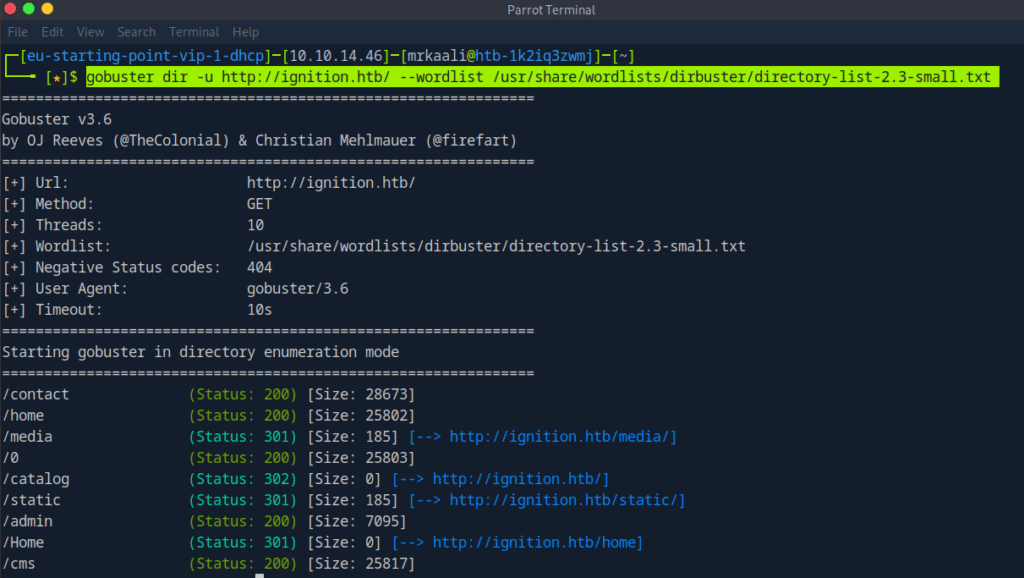
Task 5 Use a tool to brute force directories on the webserver. What is the full URL to the Magento login page?
http://ignition.htb/admin
Task 6 Look up the password requirements for Magento and also try searching for the most common passwords of 2023. Which password provides access to the admin account?
qwerty123
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP
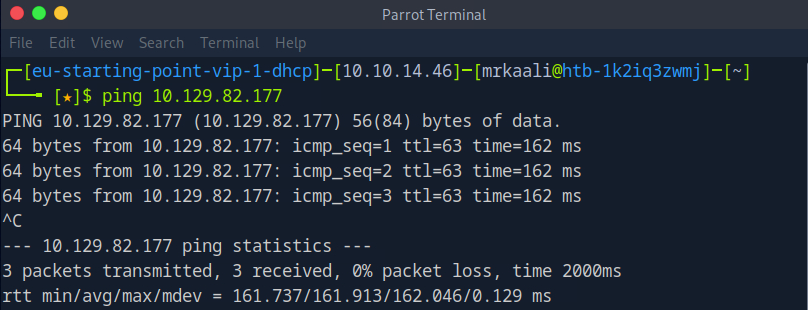
With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
sudo nmap -sV -sC -O Target_IP
sudo nmap -sV -sC -O -p- -T4 Target_IP

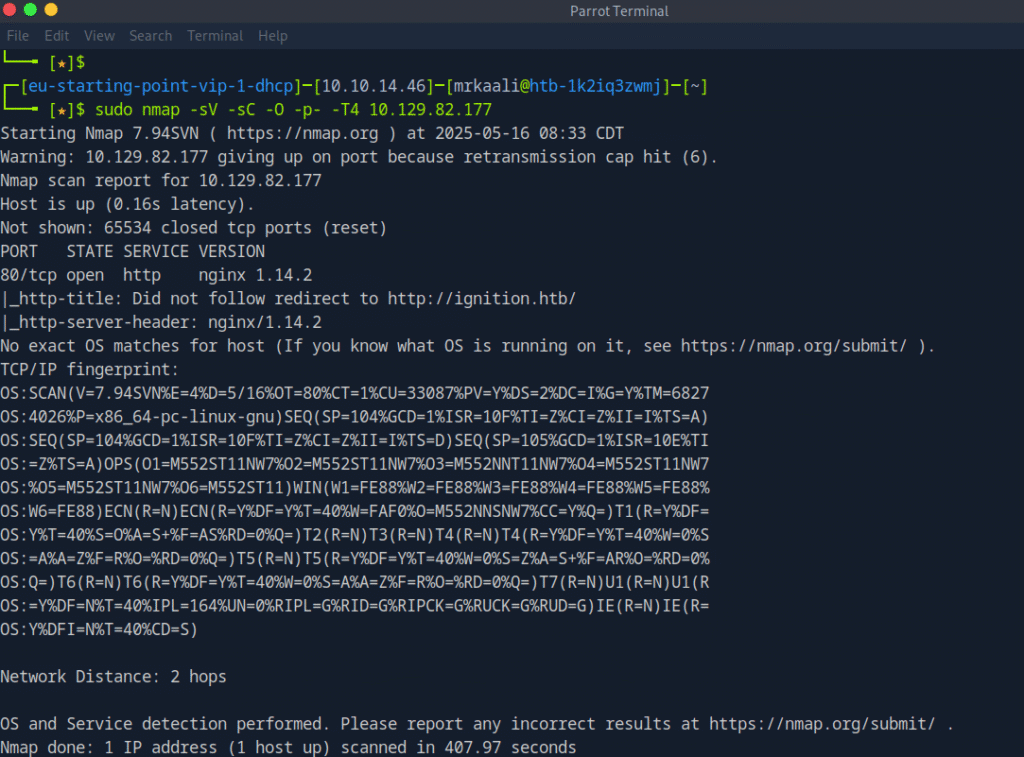
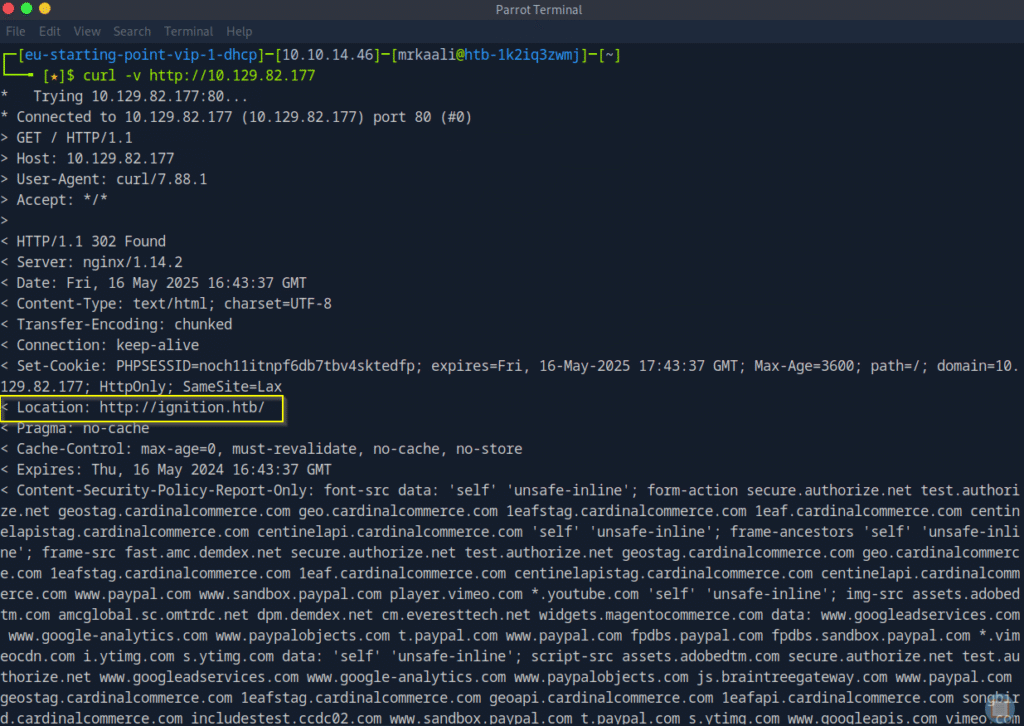
The above output shows that Port 80 is open and running nginx/1.14.2 and it redirects to http://ignition.htb/ and let’s see it get something on web browser:

What is Curl
curl is a command-line tool used to transfer data to or from a server using various protocols, most commonly HTTP, HTTPS, and FTP. It’s widely used for testing APIs, downloading files, and interacting with web services directly from the terminal.

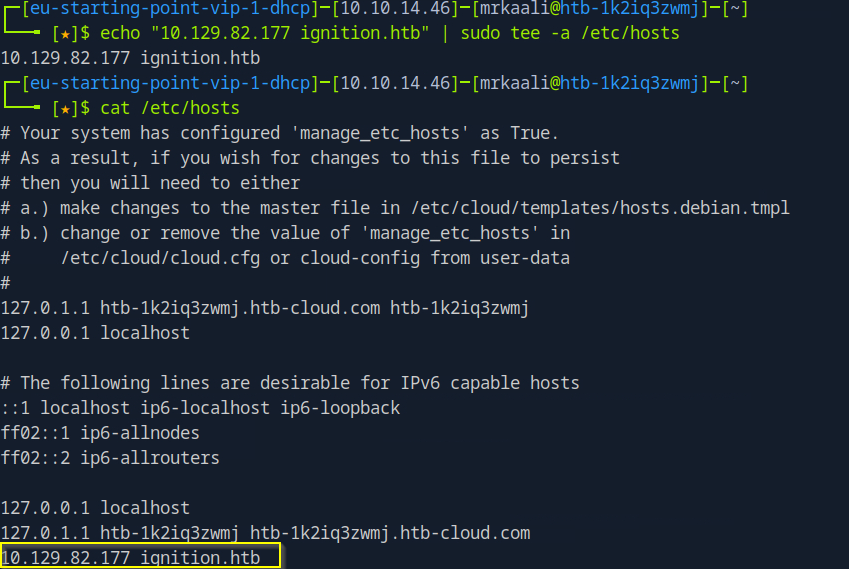
Command : echo “10.129.82.177 ignition.htb” | sudo tee -a /etc/hosts. This command appends the line 10.129.82.177 ignition.htb to the /etc/hosts file, mapping the domain ignition.htb to the IP address 10.129.82.177 on your local machine. This allows you to access ignition.htb in your browser or with tools like curl, and have it resolve to 10.129.82.177.
Exploitation
Now let’s move ahead and try gobuster.
Command: gobuster dir -u http://ignition.htb/ –wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt

We can see the top 10 common passwords list in 2025 from here

Finally admin and qwerty123 credentials worked:
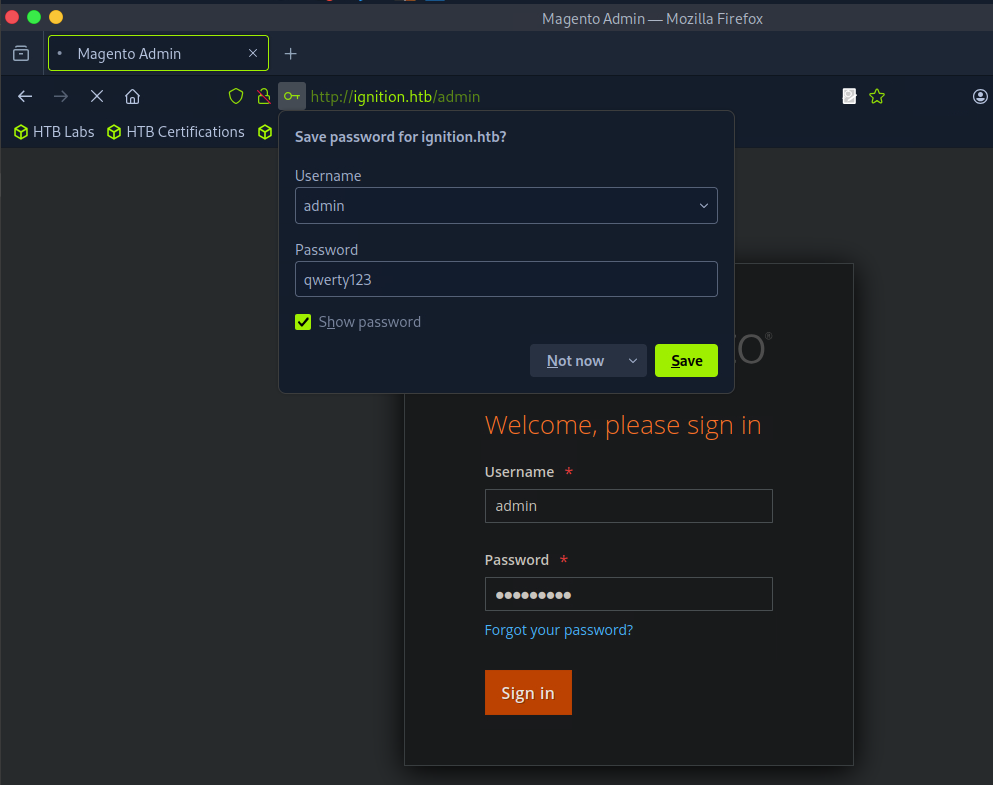

Submit root flag
And we got the flag value inside account.
Key Takeaways
- Always enumerate properly.
- Do not use default or weak credentials for services.
- Always check the worst password lists.
If you enjoyed this post, share it with your friends and colleagues!
