Hi everyone
Today we are going to look for a Box called Crocodile which is rated as very easy in terms of difficulty. This machine has three phases: Recon, Enumeration and Exploitation.
- BOX Questions
- Task 1 What Nmap scanning switch employs the use of default scripts during a scan?
- Task 2 What service version is found to be running on port 21?
- Task 3 What FTP code is returned to us for the “Anonymous FTP login allowed” message?
- Task 4 After connecting to the FTP server using the ftp client, what username do we provide when prompted to log in anonymously?
- Task 5 After connecting to the FTP server anonymously, what command can we use to download the files we find on the FTP server?
- Task 6 What is one of the higher-privilege sounding usernames in ‘allowed.userlist’ that we download from the FTP server?
- Task 7 What version of Apache HTTP Server is running on the target host?
- Task 8 What switch can we use with Gobuster to specify we are looking for specific filetypes?
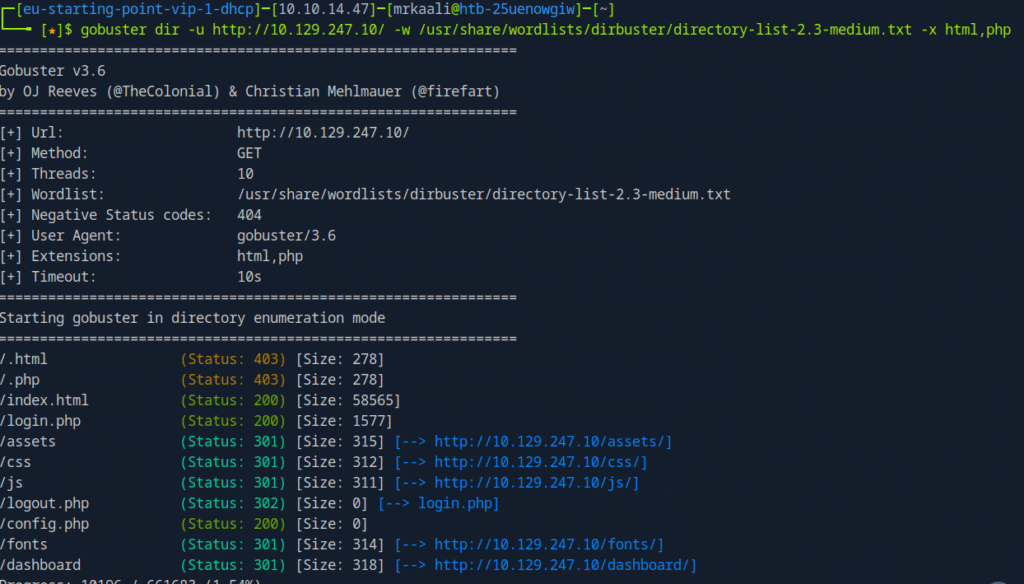
- Task 9 Which PHP file can we identify with directory brute force that will provide the opportunity to authenticate to the web service?
- Recon & Enumeration
- Exploitation
- Key Takeaways
This room includes various tasks that needs to be completed to solve the entire CTF.
BOX Questions
Task 1 What Nmap scanning switch employs the use of default scripts during a scan?
-sC
Task 2 What service version is found to be running on port 21?
vsftpd 3.0.3
Task 3 What FTP code is returned to us for the “Anonymous FTP login allowed” message?
230
Task 4 After connecting to the FTP server using the ftp client, what username do we provide when prompted to log in anonymously?
anonymous
Task 5 After connecting to the FTP server anonymously, what command can we use to download the files we find on the FTP server?
get
Task 6 What is one of the higher-privilege sounding usernames in ‘allowed.userlist’ that we download from the FTP server?
admin
Task 7 What version of Apache HTTP Server is running on the target host?
Apache httpd 2.4.41
Task 8 What switch can we use with Gobuster to specify we are looking for specific filetypes?
-x
Task 9 Which PHP file can we identify with directory brute force that will provide the opportunity to authenticate to the web service?
login.php
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP

With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
sudo nmap -sV -sC -O Target_IP
sudo nmap -sV -sC -O -p- -T4 Target_IP

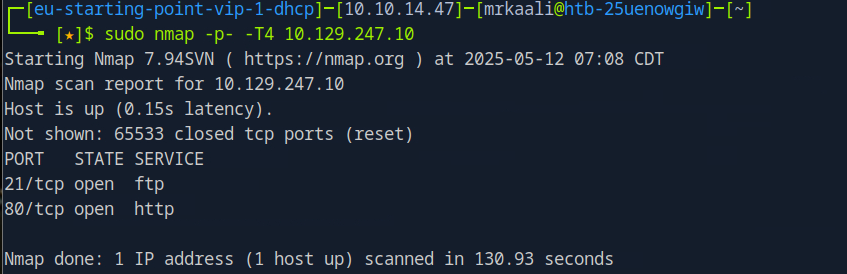
Exploitation
Now let’s move ahead and try connecting to FTP using the command ftp Target_IP
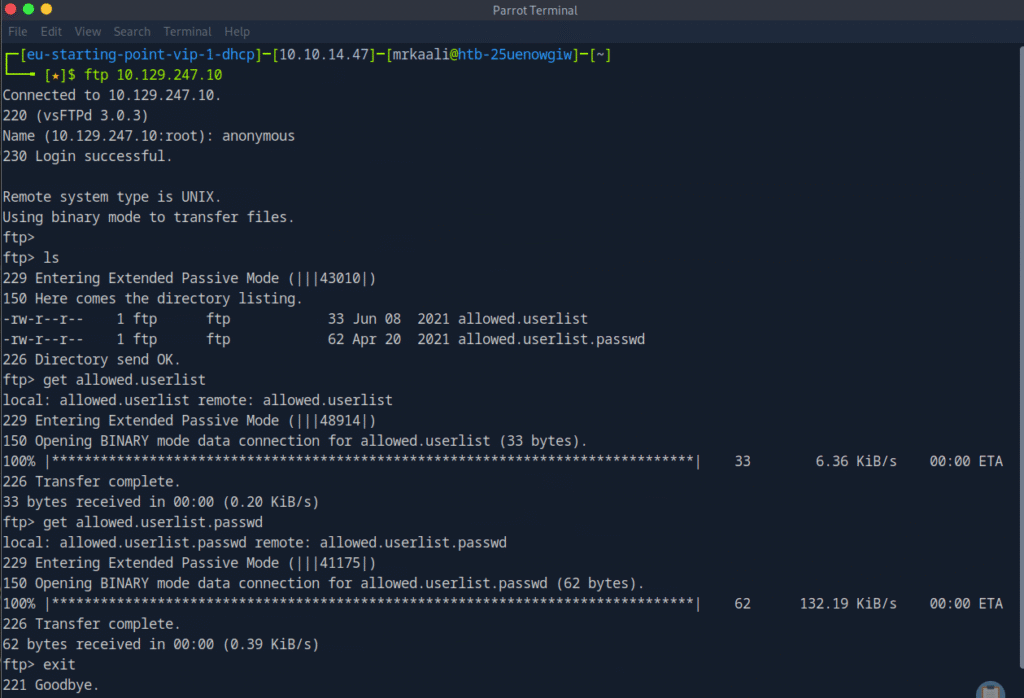
We can see that there are 2 files allowed.userlist and allowe.userlist.passwd. We will move it to our parrot directory with the get command.
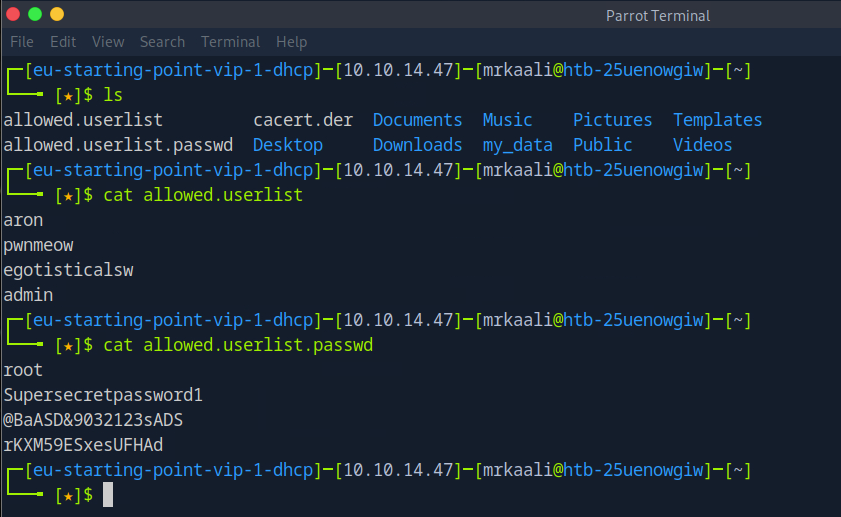
After inspecting both the files we got usernames and password which might work somewhere.
Now as HTTP service is also running so lets check it in the web browser.
We see a landing page for some website and checked page source but didn’t get anything.
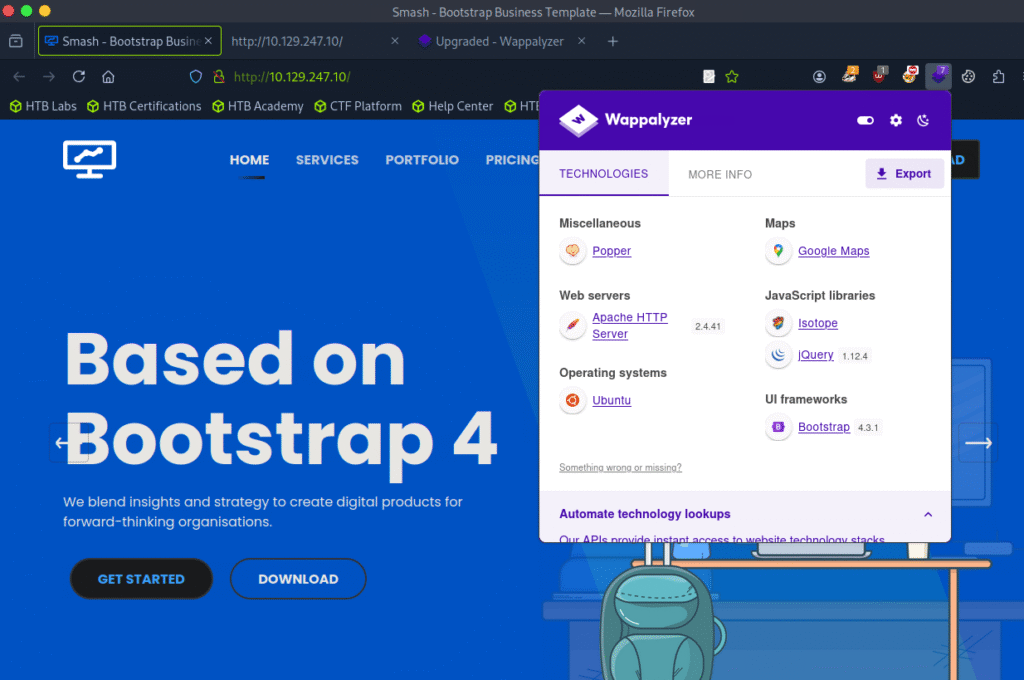
After checking the wappalyzer I got that the site is using PHP, JavaScript, Bootstrap and Apache HTTP Server.
A quick gobuster scan reveals login.php so I thought the credentials found through ftp might work here.
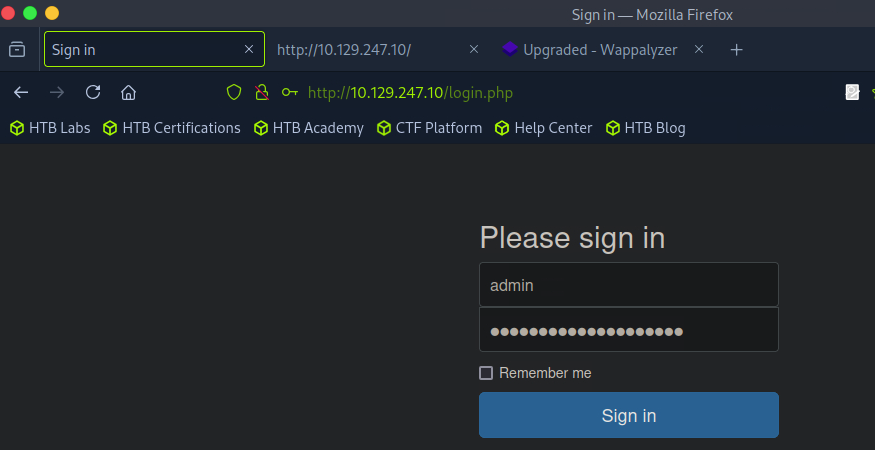
One of the credentials worked and I was successfully able to login to the web app.
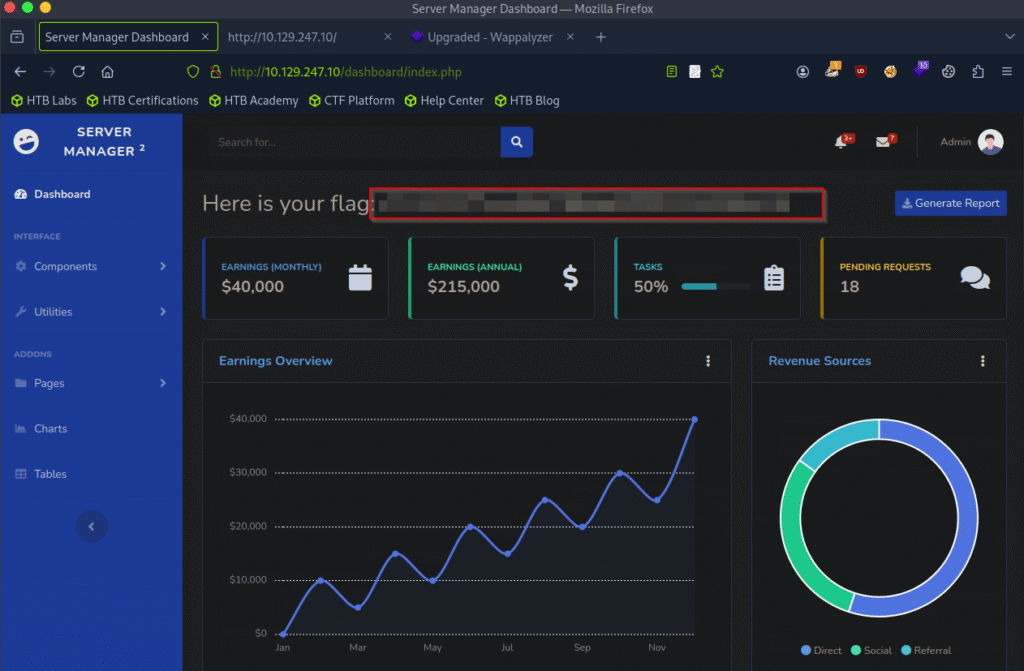
Submit root flag
And we got the flag value inside the flag file.
Key Takeaways
- Always enumerate properly.
- Do not use default or weak credentials for services.
- Securely configure the services such as FTP.
If you enjoyed this post, share it with your friends and colleagues!
