Hi everyone
Today we are going to look for a Box called Explosion which is rated as very easy in terms of difficulty. This machine has three phases: Recon, Enumeration and Exploitation.
- BOX Questions
- Task 1 What does the 3-letter acronym RDP stand for?
- Task 2 What is a 3-letter acronym that refers to interaction with the host through a command line interface?
- Task 3 What about graphical user interface interactions?
- Task 4 What is the name of an old remote access tool that came without encryption by default and listens on TCP port 23?
- Task 5 What is the name of the service running on port 3389 TCP?
- Task 6 What is the switch used to specify the target host’s IP address when using xfreerdp?
- Task 7 What username successfully returns a desktop projection to us with a blank password?
- Recon & Enumeration
- Exploitation
- Submit root flag
- Key Takeaways
There are various tasks that needs to be completed to solve the entire Machine/Box.
BOX Questions
Task 1 What does the 3-letter acronym RDP stand for?
Remote Desktop Protocol
Task 2 What is a 3-letter acronym that refers to interaction with the host through a command line interface?
CLI
Task 3 What about graphical user interface interactions?
GUI
Task 4 What is the name of an old remote access tool that came without encryption by default and listens on TCP port 23?
telnet
Task 5 What is the name of the service running on port 3389 TCP?
ms-wbt-server
Task 6 What is the switch used to specify the target host’s IP address when using xfreerdp?
/v:
Task 7 What username successfully returns a desktop projection to us with a blank password?
Administrator
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP
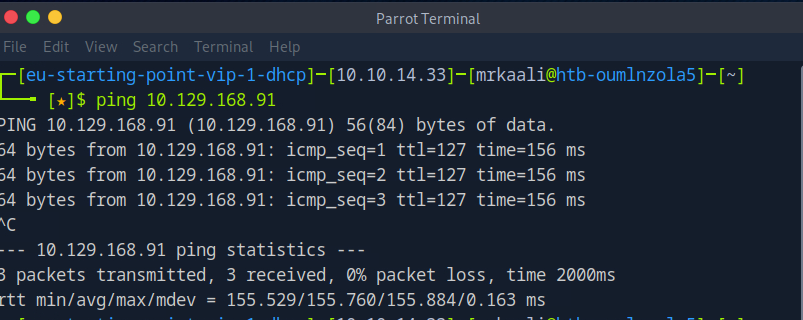
With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
sudo nmap -sV Target_IP
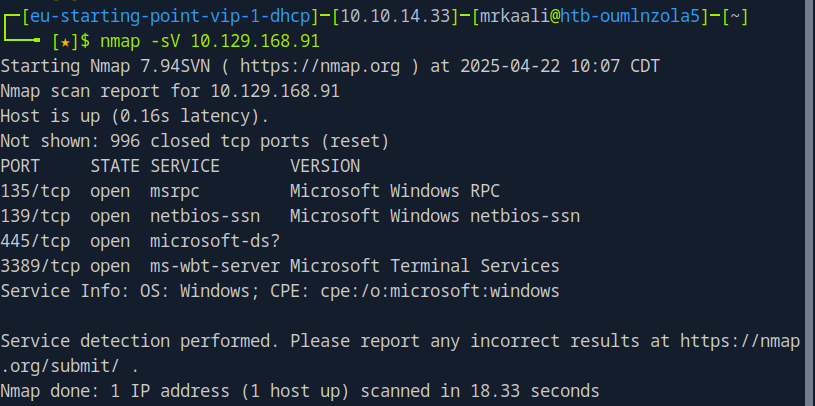
The above output shows that Port 135,139,445 and 3389 are open, and also we found that the target OS is Windows OS.
Exploitation
What is xfreerdp?
Users can connect to and manage Windows PCs remotely from Linux or other Unix-like operating systems using xfreerdp, an open-source command-line client for the Remote Desktop Protocol (RDP). Often used for remote administration, penetration testing, and accessing Windows desktops or servers from non-Windows environments, it is a component of the FreeRDP project.
We will connect from our Parrot Security virtual machine using xfreerdp. Entering the command name in the terminal will allow you to see if xfreerdp is installed.
Command: xfreerdp
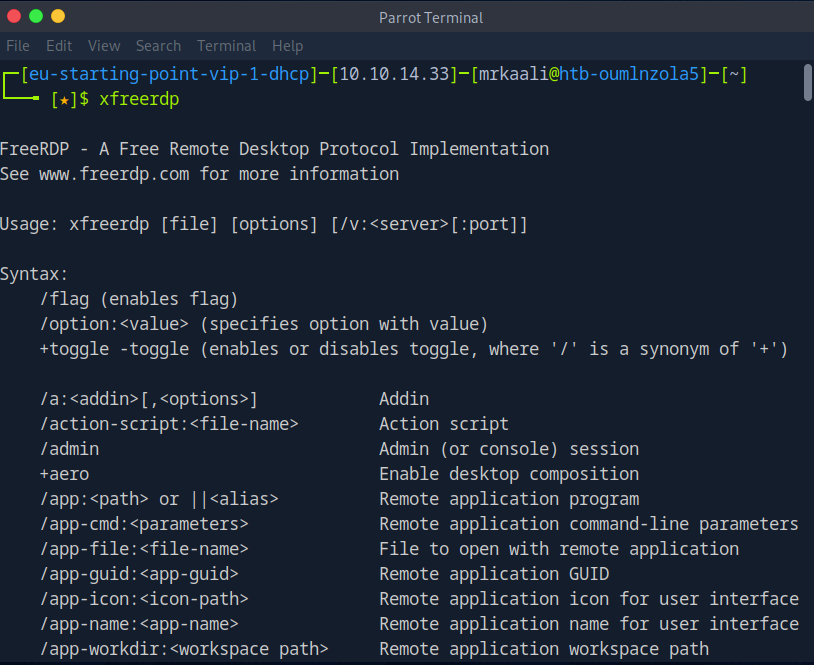
Let’s move ahead and try connecting RDP session:
Command: xfreerdp /v:{target_IP}
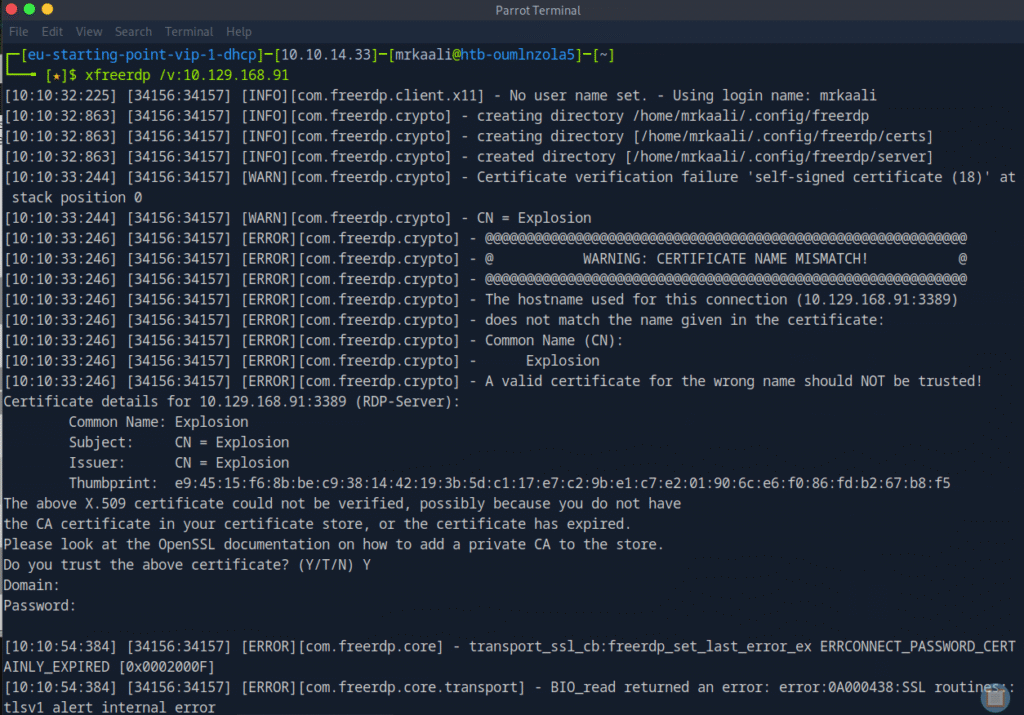
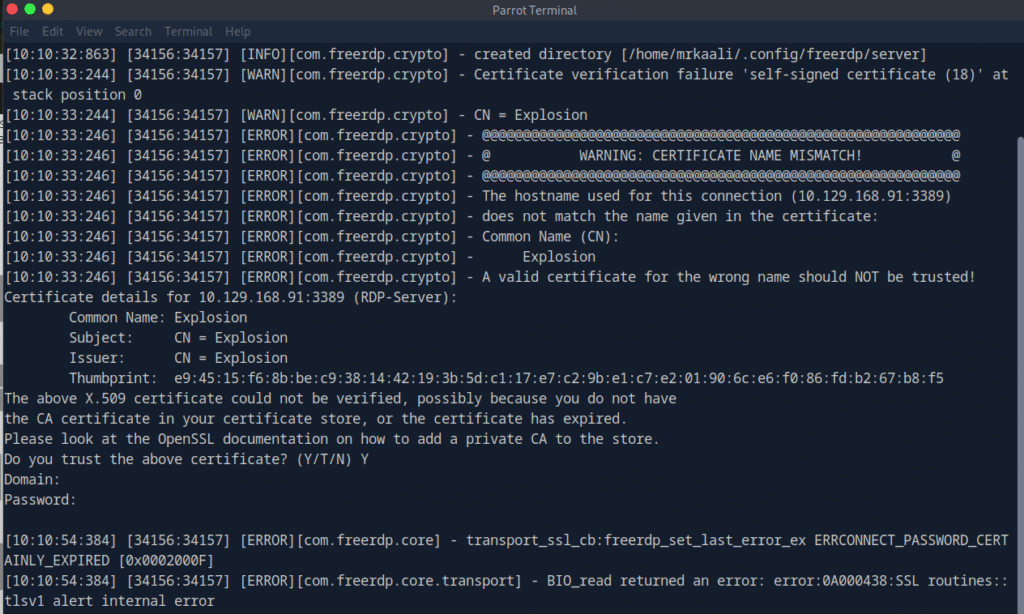
But it didn’t worked so let’s try with /cert:ignore and /u: Administrator:
Command: xfreerdp /v:{target_IP} /cert:ignore /u: Administrator.
The above command is used to connect to a remote desktop service (RDP) using xfreerdp, specifying the target IP, ignoring certificate warnings, and logging in as the Administrator user.

We were able to get RDP session and we can see the flag file:
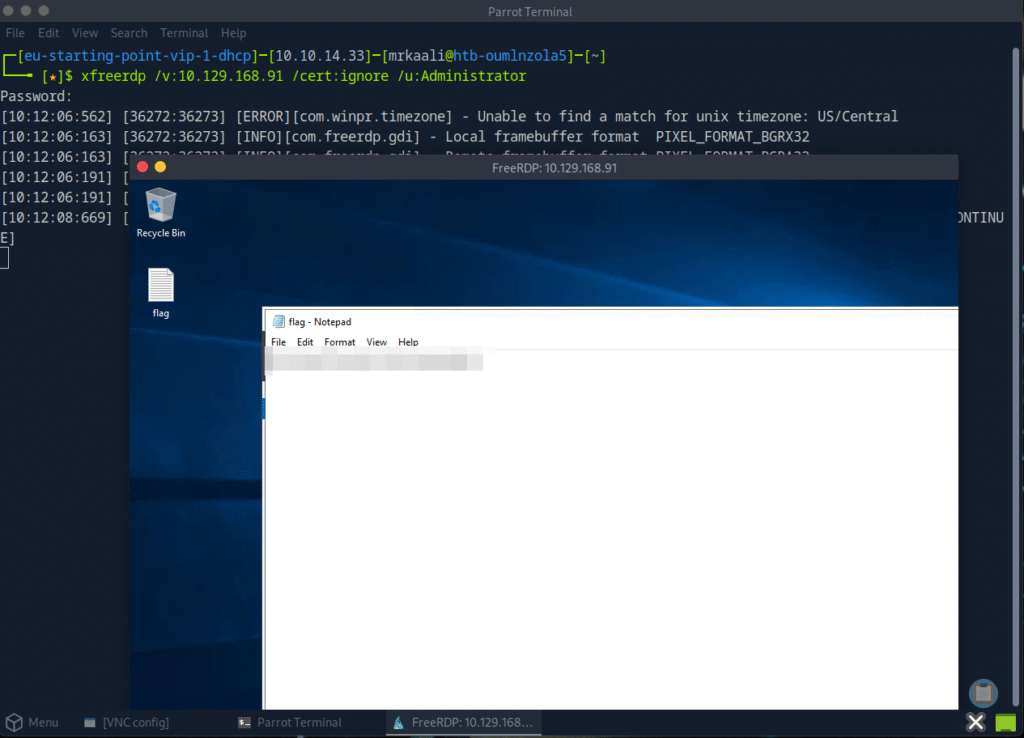
Submit root flag
We were able to successfully retrieve the flag.
Key Takeaways
- Always enumerate properly.
- Do not weak credentials.
- Restrict RDP access to trusted IPs via firewall rules
If you enjoyed this post, share it with your friends and colleagues!