Hi everyone
Today we are going to look for a Box called Fawn which is rated as very easy in terms of difficulty. This machine has three phases: Recon, Enumeration and Exploitation.
- BOX Questions
- Task 1 What does the 3-letter acronym FTP stand for?
- Task 2 Which port does the FTP service listen on usually?
- Task 3 FTP sends data in the clear, without any encryption. What acronym is used for a later protocol designed to provide similar functionality to FTP but securely, as an extension of the SSH protocol?
- Task 4 What is the command we can use to send an ICMP echo request to test our connection to the target?
- Task 5 From your scans, what version is FTP running on the target?
- Task 6 From your scans, what OS type is running on the target?
- Task 7 What is the command we need to run in order to display the ‘ftp’ client help menu?
- Task 8 What is username that is used over FTP when you want to log in without having an account?
- Task 9 What is the response code we get for the FTP message ‘Login successful’?
- Task 10 There are a couple of commands we can use to list the files and directories available on the FTP server. One is dir. What is the other that is a common way to list files on a Linux system.
- Task 11 What is the command used to download the file we found on the FTP server?
- Recon & Enumeration
- Exploitation
- Key Takeaways
There are various tasks that needs to be completed to solve the entire Machine/Box.
BOX Questions
Task 1 What does the 3-letter acronym FTP stand for?
File Transfer Protocol
Task 2 Which port does the FTP service listen on usually?
21
Task 3 FTP sends data in the clear, without any encryption. What acronym is used for a later protocol designed to provide similar functionality to FTP but securely, as an extension of the SSH protocol?
SFTP
Task 4 What is the command we can use to send an ICMP echo request to test our connection to the target?
ping
Task 5 From your scans, what version is FTP running on the target?
vsftpd 3.0.3
Task 6 From your scans, what OS type is running on the target?
Unix
Task 7 What is the command we need to run in order to display the ‘ftp’ client help menu?
ftp -?
Task 8 What is username that is used over FTP when you want to log in without having an account?
anonymous
Task 9 What is the response code we get for the FTP message ‘Login successful’?
230
Task 10 There are a couple of commands we can use to list the files and directories available on the FTP server. One is dir. What is the other that is a common way to list files on a Linux system.
ls
Task 11 What is the command used to download the file we found on the FTP server?
get
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP

With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
sudo nmap -sV Target_IP

The above output shows that Port 21 is open, and ftp service is running on that port, also we found that the target OS is Unix OS.
FTP:
A common network protocol called File Transfer Protocol, or FTP, is used to move files across a TCP-based network, such the Internet, between a client and a server. It is described in RFC 959 and was created in the early days of networking.
FTP uses two different channels: a data channel for file transfers and a command channel for transmitting commands and answers. In active mode, FTP uses port 20 for the data channel and port 21 for the command channel by default.
Unless used with encryption extensions like FTPS (FTP Secure) or replaced by more secure protocols like SFTP (SSH File Transfer Protocol), FTP is insecure for sensitive data because it sends data, including credentials, in plaintext. FTP offers basic authentication (username and password).
Exploitation
To move ahead with the exploitation lets ee the options for FTP and that we can see with the command ftp -?

Now let’s move ahead and try connecting to FTP using the command ftp Target_IP.
When asked for the credentials try FTP Anonymous Login.
What is Anonymous login?
Users can access an FTP server without a distinct username and password by using anonymous FTP login. Rather, users use the username anonymous (or occasionally ftp) to log in, and the password is frequently left blank or any email address. This is frequently used to make files, such software repositories or public datasets, accessible to the general public.

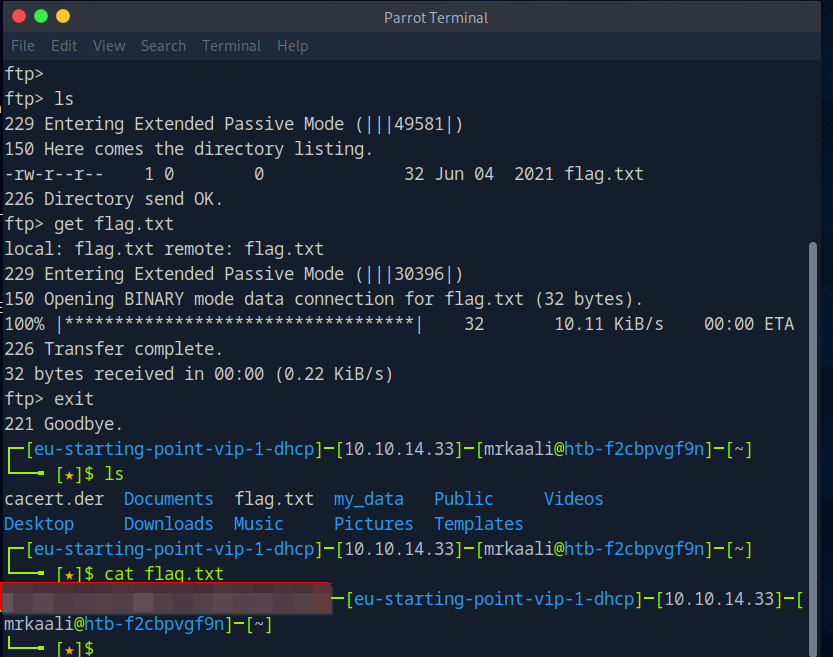
We are able to successfully login and let’s try digging more.
We got the flag.txt


Submit root flag
And we got the flag value inside the flag.txt file.
Key Takeaways
- Always enumerate properly.
- Do not use insecure logins like Anonymous logins and insecure FTP service.
- If using FTP service make sure to implement strong credentials.
If you enjoyed this post, share it with your friends and colleagues!
