An excellent method for developing the fundamentals of penetration testing is to use HackTheBox Starting Point.
Today we are going to look for a Box called Meow which is rated as very easy in terms of difficulty. This machine has three phases: Recon, Enumeration and Exploitation
- BOX Questions
- Task 1 What does the acronym VM stand for?
- Task 2 What tool do we use to interact with the operating system in order to issue commands via the command line, such as the one to start our VPN connection? It’s also known as a console or shell.
- Task 3 What service do we use to form our VPN connection into HTB labs?
- Task 4 What tool do we use to test our connection to the target with an ICMP echo request?
- Task 5 What is the name of the most common tool for finding open ports on a target?
- Task 6 What service do we identify on port 23/tcp during our scans?
- Task 7 What username is able to log into the target over telnet with a blank password?
- Recon & Enumeration
- Exploitation
- Key Takeaways
There are various tasks that needs to be completed to solve the entire Machine/Box.
BOX Questions
Task 1 What does the acronym VM stand for?
Virtual machine
Task 2 What tool do we use to interact with the operating system in order to issue commands via the command line, such as the one to start our VPN connection? It’s also known as a console or shell.
Terminal
Task 3 What service do we use to form our VPN connection into HTB labs?
openvpn
Task 4 What tool do we use to test our connection to the target with an ICMP echo request?
ping
Task 5 What is the name of the most common tool for finding open ports on a target?
Nmap
Task 6 What service do we identify on port 23/tcp during our scans?
Telnet
Task 7 What username is able to log into the target over telnet with a blank password?
root
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP
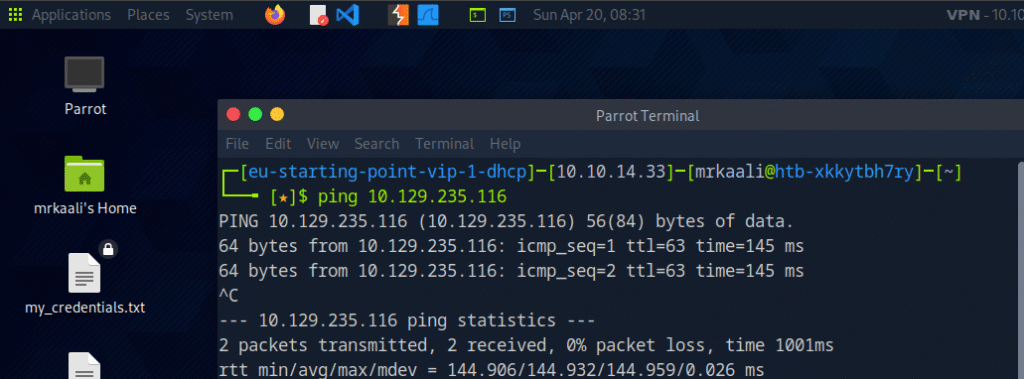
With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
sudo nmap -sV Target_IP

The above output shows that Port 23 is open, and telnet service is running on that port, also we found that the target OS is Linux OS.
Telnet:
Users can connect to distant computers via a TCP/IP network by using the Telnet service, which is a network protocol and program that usually uses port 23. Through a command-line interface, Telnet allows you to get into another computer and interact with it as though you were physically at its terminal.
Telnet is insecure for the majority of contemporary applications since it sends data in plaintext, including usernames and passwords. Because of this, more secure protocols like SSH (Secure Shell), which encrypts the transmission, have mostly superseded Telnet.
Connecting to Telnet: Telnet Target_IP , once you enter the command it will ask for username and password. I tried randomly username as root and blank password and it worked, I got the access
Exploitation


Then I quickly check the current working directory with PWD command and I was in the root directory then I executed the ls and ls -al command to list files present in the root directory and there was the flag.txt

Key Takeaways
- Always enumerate properly.
- Do not use insecure and misconfigured services such as telnet.
- Do not use default, weak and blank credentials for services and accounts.
If you enjoyed this post, share it with your friends and colleagues!