Hi everyone
Today we are going to look for a Box called Sequel which is rated as very easy in terms of difficulty. This machine has three phases: Recon, Enumeration and Exploitation.
- BOX Questions
- Task 1 During our scan, which port do we find serving MySQL?
- Task 2 What is one of the most common type of SQL vulnerabilities?
- Task 3 When using the MySQL command line client, what switch do we need to use in order to specify a login username?
- Task 4 Which username allows us to log into this MariaDB instance without providing a password?
- Task 5 In SQL, what symbol can we use to specify within the query that we want to display everything inside a table?
- Task 6 In SQL, what symbol do we need to end each query with?
- Task 7 There are three databases in this MySQL instance that are common across all MySQL instances. What is the name of the fourth that’s unique to this host?ound’ errors?
- Recon & Enumeration
- Exploitation
- Key Takeaways
This room includes various tasks that needs to be completed to solve the entire CTF.
BOX Questions
Task 1 During our scan, which port do we find serving MySQL?
3306
Task 2 What is one of the most common type of SQL vulnerabilities?
MariaDB
Task 3 When using the MySQL command line client, what switch do we need to use in order to specify a login username?
-u
Task 4 Which username allows us to log into this MariaDB instance without providing a password?
root
Task 5 In SQL, what symbol can we use to specify within the query that we want to display everything inside a table?
*
Task 6 In SQL, what symbol do we need to end each query with?
;
Task 7 There are three databases in this MySQL instance that are common across all MySQL instances. What is the name of the fourth that’s unique to this host?
ound’ errors?
htb
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP
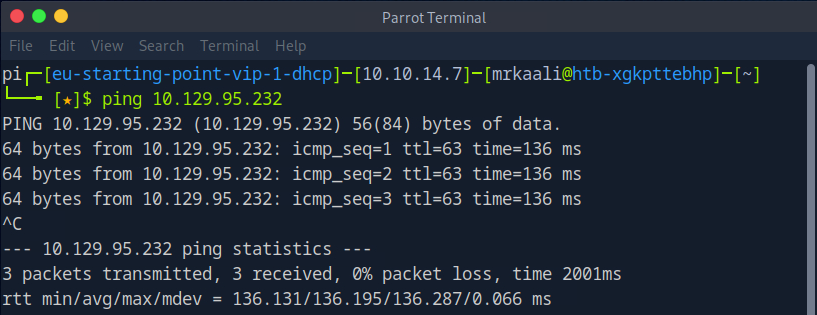
With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
sudo nmap -sV -sC -O Target_IP
sudo nmap -sV -sC -O -p- -T4 Target_IP
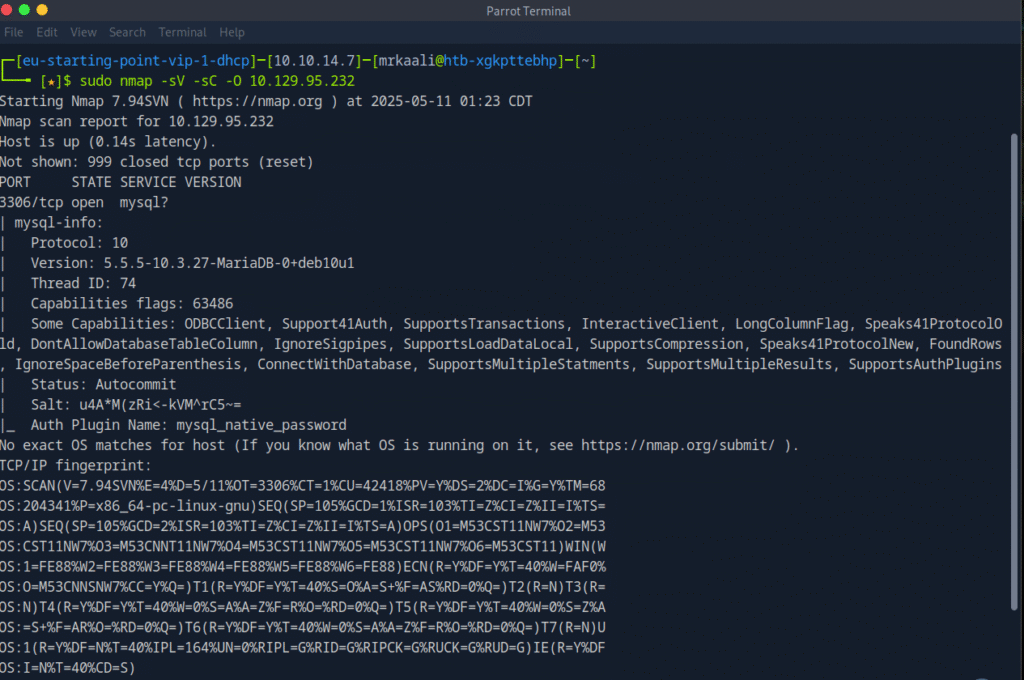
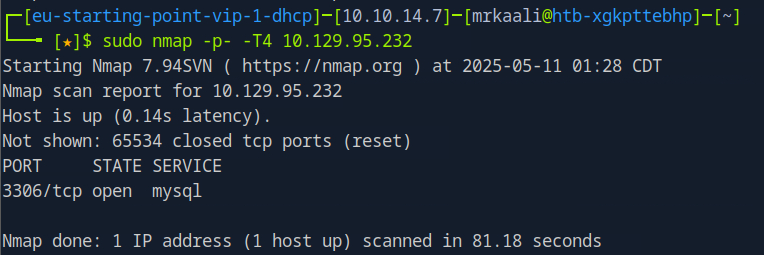
The above output shows that Port 3306is open, and mysql service is running on that port.
MySQL?
MySQL is an open-source relational database management system (RDBMS) that stores and organizes data in tables, allowing users to create, read, update, and delete data using the SQL (Structured Query Language) language.
Exploitation
mysql –help
Now we will be trying to connect to the target mysql server:
mysql -h Target_IP -u root
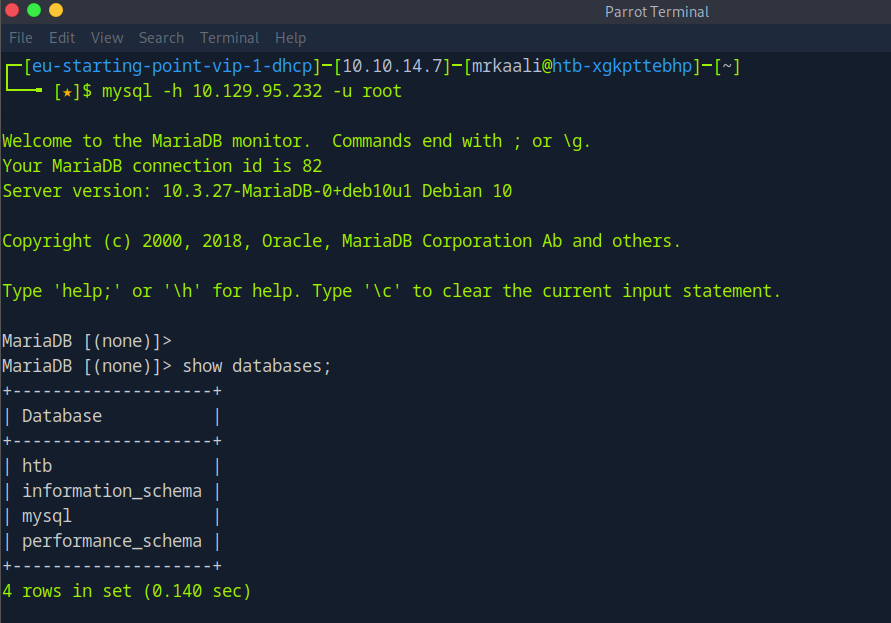

Submit root flag
And we got the flag value inside the flag file.
Key Takeaways
- Always enumerate properly.
- Do not use default or weak credentials for services.
- Apply the principle of least privilege to database accounts
If you enjoyed this post, share it with your friends and colleagues!
