Hi everyone
Today we are going to look for a Linux Box called Three which is rated as very easy in terms of difficulty. This machine has three phases: Recon, Enumeration and Exploitation.
- BOX Questions
- Task 1 How many TCP ports are open?
- Task 2 What is the domain of the email address provided in the “Contact” section of the website?
- Task 3 In the absence of a DNS server, which Linux file can we use to resolve hostnames to IP addresses in order to be able to access the websites that point to those hostnames?
- Task 4 Which sub-domain is discovered during further enumeration?
- Task 5 Which service is running on the discovered sub-domain?
- Task 6 Which command line utility can be used to interact with the service running on the discovered sub-domain?
- Task 7 Which command is used to set up the AWS CLI installation?
- Task 8 What is the command used by the above utility to list all of the S3 buckets?
- Task 9 This server is configured to run files written in what web scripting language?
- Recon & Enumeration
- Exploitation
- Key Takeaways
This room includes various tasks that needs to be completed to solve the entire CTF.
BOX Questions
Task 1 How many TCP ports are open?
2
Task 2 What is the domain of the email address provided in the “Contact” section of the website?
thetoppers.htb
Task 3 In the absence of a DNS server, which Linux file can we use to resolve hostnames to IP addresses in order to be able to access the websites that point to those hostnames?
/etc/hosts
Task 4 Which sub-domain is discovered during further enumeration?
s3.thetoppers.htb
Task 5 Which service is running on the discovered sub-domain?
Amazon S3
Task 6 Which command line utility can be used to interact with the service running on the discovered sub-domain?
awscli
Task 7 Which command is used to set up the AWS CLI installation?
aws configure
Task 8 What is the command used by the above utility to list all of the S3 buckets?
aws s3 ls
Task 9 This server is configured to run files written in what web scripting language?
PHP
Recon & Enumeration
Enumeration plays a very significant role in pen testing. The more properly you enumerate the more it will be easy to get a foothold on the target.
First, we will check whether target is reachable or not with ping command:
ping Target_IP
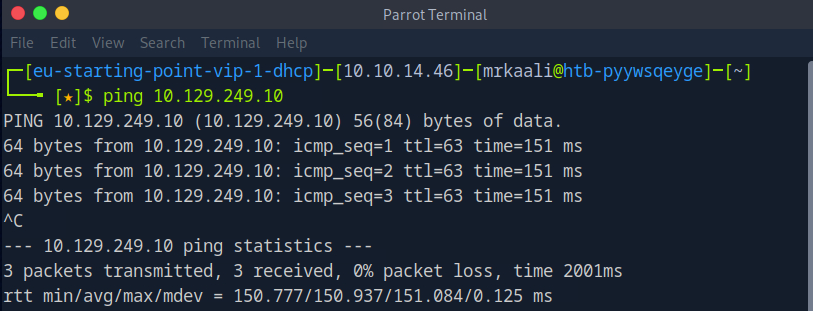
With ping command output we found that the target is reachable.
Now let’s move ahead and run the port scan for which we will be using Nmap a popular tool for port scanning and it will provide details of the various ports which are in Open state. The command for that will be:
sudo nmap -sV -sC -O Target_IP

The above output shows that Port 22 and 80 are open,running Apache 2.4.29 and also we found that the target OS is Linux OS.
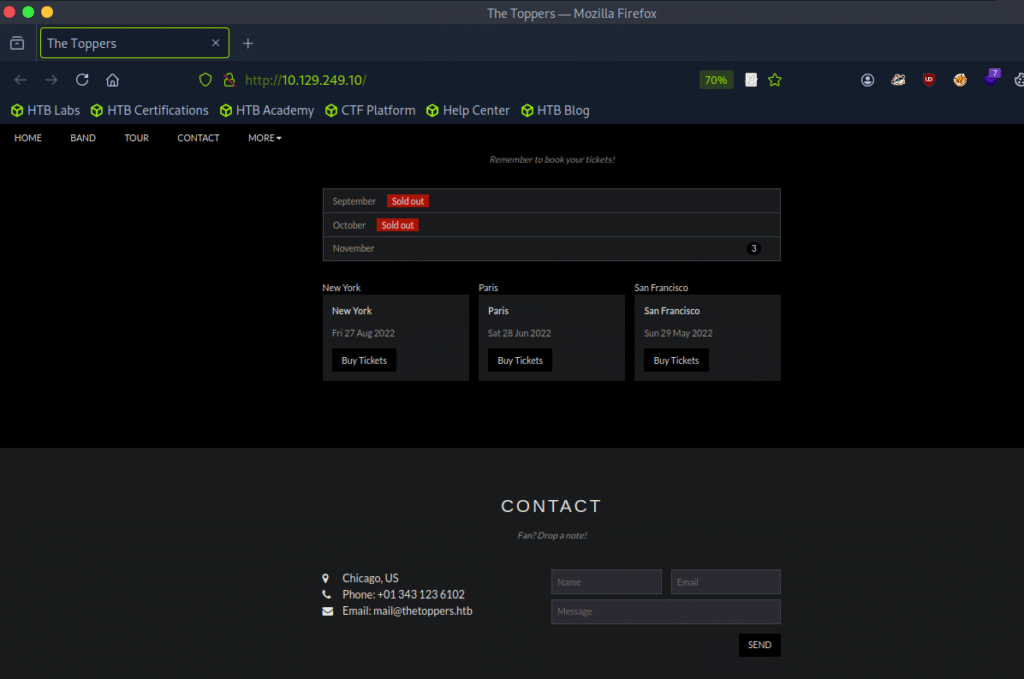
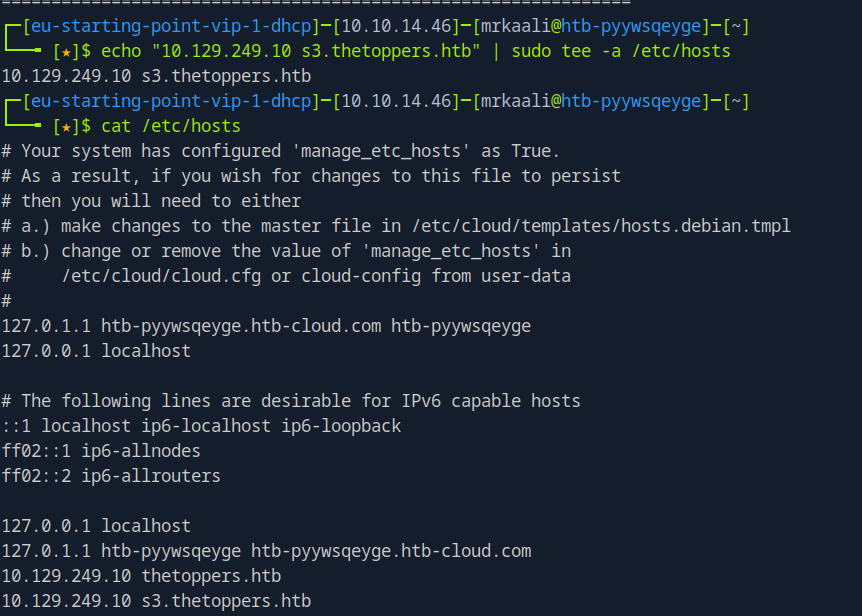
Let’s add an entry for thetoppers.htb in the /etc/hosts file with the corresponding IP address to be able
to access this domain in our browser.
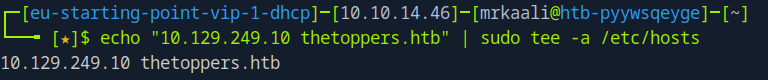
echo “10.129.249.10 thetoppers.htb” | sudo tee -a /etc/hosts : This command adds the line 10.129.249.10 thetoppers.htb to your /etc/hosts file, mapping the domain thetoppers.htb to the IP address 10.129.249.10 locally. This lets you access thetoppers.htb in your browser or tools, and have it resolve to 10.129.249.10.
Let’s use wfuff.
What is wfuff?
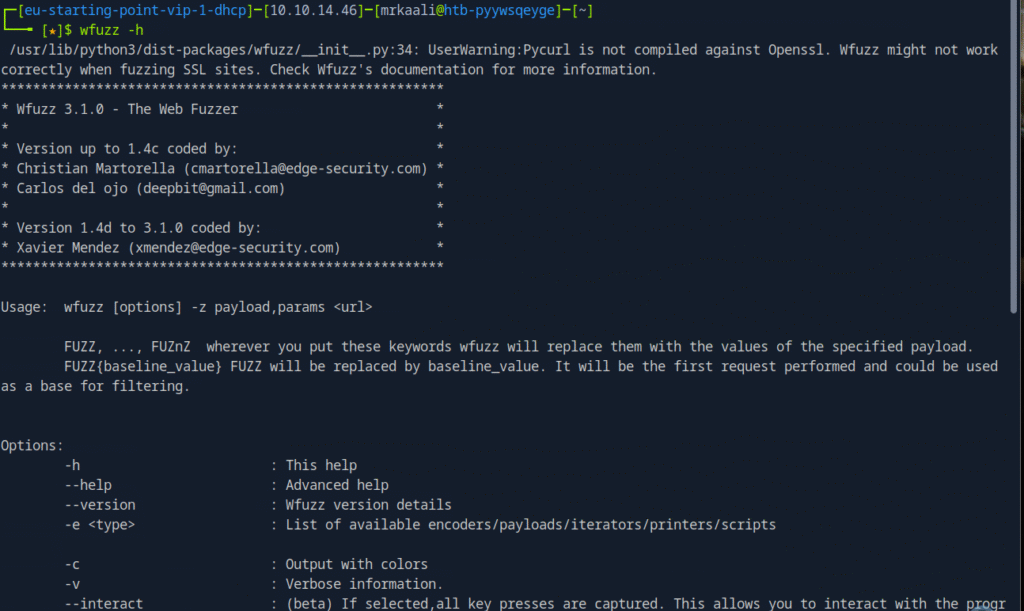
wfuzz -c -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u “http://thetoppers.htb” -H “Host: FUZZ.thetoppers.htb” –hw 1036 -t 5
This wfuzz command is performing subdomain enumeration against thetoppers.htb by fuzzing the Host header with values from the provided wordlist. The -hw 1036 option filters out responses with 1036 words (likely the size of the default/error page), and -t 5 sets the number of concurrent threads to 5.
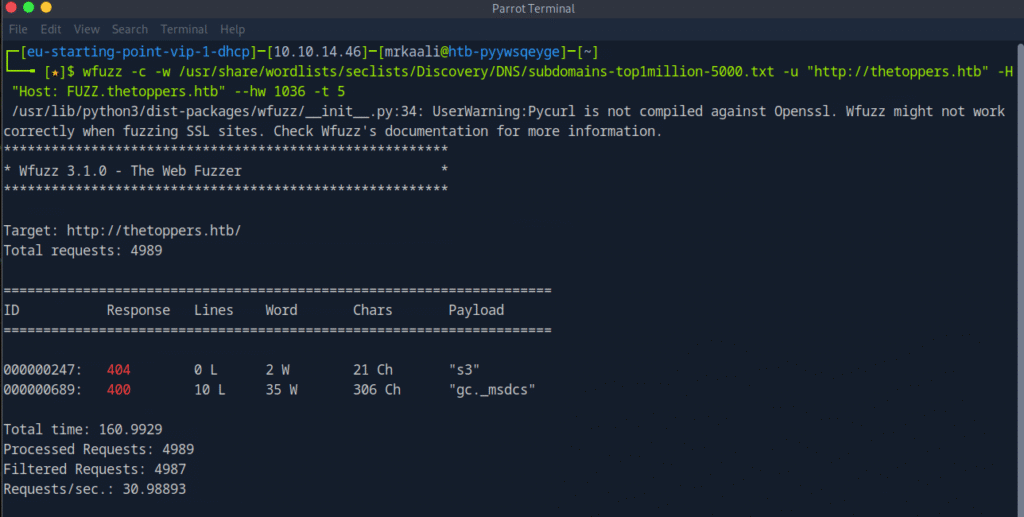
gobuster vhost -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-20000.txt -u http://thetoppers.htb –append-domain
Nothing worked except the –append-domain switch.
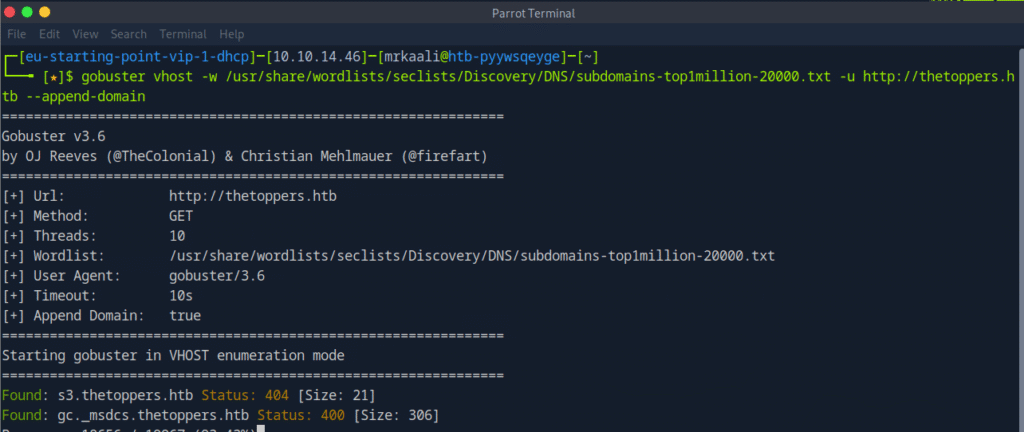
We found two results. One of them was s3.thetoppers.htb. Let’s also add anentry for this sub-domain in the /etc/hosts file.
What exactly is an S3 bucket?
Amazon Web Services (AWS) Simple Storage Service (S3) offers cloud storage containers called S3 buckets. It is used to store and arrange items in the cloud, including backups, documents, photos, and other kinds of data. Every bucket has a distinct name and may be set up with various security and access rights.
We can interact with this S3 bucket with the aid of the awscli utility. It can be installed on Linux using the
command apt install awscli .
aws cli
The AWS CLI (Command Line Interface) is a tool that lets you interact with Amazon Web Services directly from your terminal or command prompt. You can use it to manage resources like S3 buckets, EC2 instances, IAM users, and much more, all through simple commands.
sudo apt install awscli
First, we need to configure it using the following command:
aws configure: aws configure is a command used to set up your AWS CLI (Command Line Interface) credentials and default settings. When you run it, you’ll be prompted to enter your AWS Access Key ID, Secret Access Key, default region, and output format. This allows you to interact with AWS services from your terminal.
Exploitation




Submit root flag
And we got the flag value inside the flag file.
Key Takeaways
- Always enumerate properly.
- If one tool doesn’t give results try various switches as well as other tools.
- Use IAM users with the least privileges necessary.
- Disable public access unless absolutely necessary
- Always enable bucket-level access controls.
- Restrict allowed file extensions and MIME types.
- Store uploaded files outside the web root, and never execute or include uploaded files
If you enjoyed this post, share it with your friends and colleagues!